Combatting the Sophistication of Cyber Attacks

Technological advancement is akin to a double-edged sword. On one side, it presents endless new possibilities; on the other, it offers opportunities for misuse, as seen in cyber attacks. Compounding this issue, cyber attacks are becoming bolder and more sophisticated by the day, leveraging emerging technologies to bypass targeted organisations’ security measures almost undetected. This escalating trend presents a formidable challenge in effectively combatting this growing concern.
The increasing frequency and sophistication of cyber attacks underscore the need for effective preventative measures—exactly the kind of security solutions that a company like Gigamon can provide for enterprises looking for effective ways to prevent attacks on their digital infrastructure.
Ensuring Data Safety From the Unseen Threats
 According to Michael Dickman, Chief Product Officer at Gigamon, there are several reasons why preventative approaches are necessary. The most obvious is that they serve as the first line of defence, acting as guardrails to prevent unauthorised access or changes. This helps organisations safeguard their data from threats such as ransomware or phishing, which can lead to financial losses and reputational damage.
According to Michael Dickman, Chief Product Officer at Gigamon, there are several reasons why preventative approaches are necessary. The most obvious is that they serve as the first line of defence, acting as guardrails to prevent unauthorised access or changes. This helps organisations safeguard their data from threats such as ransomware or phishing, which can lead to financial losses and reputational damage.
Furthermore, preventative approaches ensure organisational compliance with data security by protecting personal and sensitive data from unauthorised use, disclosure, and breaches, thereby avoiding penalties associated with non-compliance.
The question then becomes: What is the best way to adopt a preventative approach and ensure that your organisation is more proactive in mitigating cyber threats?
Before delving into the answer to said question, Dickman quoted the adage, “You can’t secure what you can’t see,” which pretty much sums up why it is imperative to deploy a more holistic cybersecurity approach—ideally, one that can see everything.
This need for encompassing visibility is particularly significant in countering cyber attacks concealed within encryption, as they are often left uninspected mainly due to data privacy concerns. Exacerbating the matter is either the lack of suitable tools to thoroughly inspect encryption or the often high costs of the decryption process. Along with this, Dickman emphasised the need to take a proactive approach that encompasses detection, prevention, and incident response and remediation.
Dickman’s emphasis on a more holistic and proactive cybersecurity approach is at the core of the Gigamon Deep Observability Pipeline, a network-level intelligence that ensures security and compliance governance, detects threats even in encrypted traffic, and speeds incident response via granular root-cause analysis.
In addition to all the security benefits, deep observability helps organisations solve performance bottlenecks and lower the operation overhead associated with managing hybrid and multi-cloud IT environments.
The multiple benefits provided by the Gigamon Deep Observability Pipeline free up significant excess tool capacity, allowing enterprises to avoid new tool instance purchases for the next four years—and saving up on cybersecurity costs along the way.
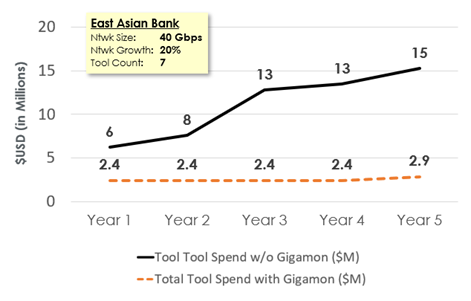
So, how is this possible? Most tools do not need to see every packet, and some tools need only information-dense metadata. The Gigamon Deep Observability Pipeline includes several methods to optimise the traffic to every tool, far beyond basic filtering. Gigamon GigaSMART, in particular, includes advanced methods like application filtering, flow slicing, and deduplication and removing noise to focus on the signal only, which is then optimised for each type of network, workload, and tool.
Misconception on the Dangers of Encrypted Traffic
Data encryption mainly serves as a protection for data confidentiality stored on a device or when transmitted to another device using an Internet connection or computer network. However, according to Dickman, data encryption has become a tool for attackers to cloak their movements. They disguise their actions as routine encrypted traffic flows, thereby avoiding detection for the most part. In fact, over 93 per cent of malware now lurks behind encryption.
A Gigamon report underscored this grim reality: Over 70 per cent of the 1,000 global IT and security leaders surveyed by the company admitted to not inspecting the encrypted data flowing across their hybrid cloud infrastructure. This practice inadvertently puts businesses at risk of being infiltrated because data are not sufficiently analysed, which means malware threats cannot be detected by security and monitoring tools alone as encrypted data traverses internally, externally, or laterally across an organisation.
Gigamon Precryption™: Heightened Visibility of Encrypted Traffic While Maintaining Privacy
To remediate the problem of threats going unscathed due to encryption, Gigamon has pioneered an innovative technology called Gigamon Precryption™. This innovative solution aims to reveal concealed threats within virtual, cloud, and container applications, including lateral movement, malware distribution, and data exfiltration. It achieves this by leveraging a fundamental component of the Linux kernel known as eBPF to extract plaintext (unencrypted) traffic for capture—either before encryption or after decryption.
The approach circumvents the need for key interception or costly decryption processes. Furthermore, Precryption technology functions independently of the application, avoiding the operational challenges of traditional agent-based approaches. It is, in other words, decrypting without actually decrypting, in effect eliminating costly decryption and tiptoeing around data privacy tenets (since nothing is actually being done on the actual encrypted item).
Precryption technology works with all TLS encryption methods, including TLS 1.3 with perfect-forward secrecy, as well as TLS 1.2 and older versions. Once unencrypted data is extracted, the Gigamon Deep Observability Pipeline optionally transforms raw communication data into flow-level metadata records for certain types of tools like SIEMs.
This reduces false positives, helps identify suspicious activity like port spoofing, and accelerates threat detection through proactive, real-time monitoring versus reactive forensics. Moreover, this network-derived intelligence is not subject to log modification, and it feeds into observability tools used by both SecOps and DevOps teams.
Gigamon’s Precryption technology offers a comprehensive solution for organisations seeking to bolster security and compliance within their hybrid cloud infrastructure while simultaneously maintaining privacy. To maintain privacy, Gigamon enables secure tunnelling from the point of data acquisition (inside the workload) to wherever the security tool is hosted. According to Dickman, Gigamon’s products and services adhere to many regulatory requirements, including data privacy, as stated by US National Security Agency (NSA): For optimal security posture, companies should at least decrypt once.
Building a Secure Future Through Product Innovations
The fight against cyber attacks is an ongoing battle, so it is paramount to stay ahead of the curve. This is precisely why Gigamon is committed to assisting organisations to enhance their cyber resilience while optimising IT operations, as emphasised by Dickman. He also noted how Gigamon will play a pivotal role in improving companies’ security posture by ensuring complete visibility as workloads migrate to private clouds and public clouds, and occasionally back to on-premises environments.
Moreover, Dickman disclosed that Gigamon intends to build the recently launched Precryption technology to overcome a long-standing challenge: Eliminating significant blind spots that had previously made security, monitoring, and troubleshooting difficult.
In addition, another key focus for Gigamon in 2024, according to Dickman, is to assist their customers in enhancing the effectiveness of their current tools with new telemetry derived from network traffic. The introduction of the Gigamon Deep Observability Pipeline enables intelligence extraction from network traffic and allows our customers to broaden the visibility and use cases of their current tool set. This possibility extends to various applications, including strengthening security posture, faster troubleshooting, and ensuring cloud providers’ Service Level Objectives (SLOs) are delivered as promised, among others.
Indeed, cybersecurity is an ongoing battle, and cybercriminals are always trying to get a step ahead. Enterprises, therefore, will need to keep pace with their cyber adversaries—or even go steps ahead by being proactive about cybersecurity. Gigamon can help them in this regard, and it will continue doing so in years to come.