The Evolution of QR Code Phishing: ASCII-Based QR Codes

by Jeremy Fuchs, Cybersecurity Researcher and Analyst at Check Point Software Technologies

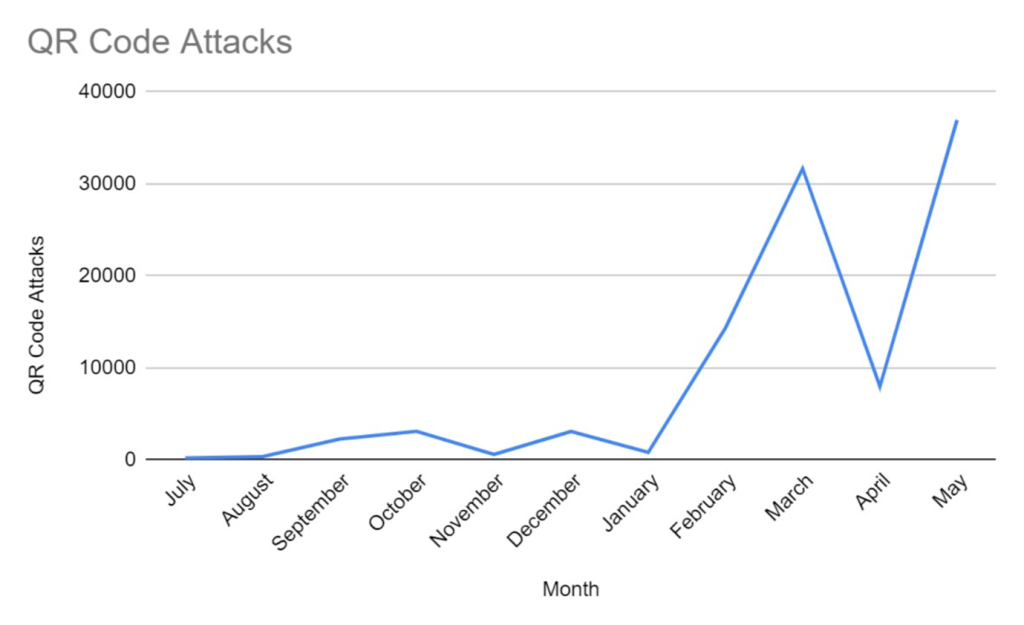
Quishing – QR code phishing – is a rapidly evolving threat. Starting around August, when we saw the first rapid increase, we’ve also seen a change in the type of QR code attacks. It started with standard Multi-Factor Authentication (MFA) requests. It then evolved to conditional routing and custom targeting. Now, we’re seeing another evolution, in the manipulation of QR codes.
Harmony Email Researchers have uncovered a new campaign, where the QR code is not in an image, but rather created via HTML and ASCII characters. Harmony Email researchers have seen over 600 similar emails in late May.
Email Example
In this email, the QR Code looks like this:

Notice anything different? Here’s a standard QR Code:

It’s subtle. But one is an image. The other is created via HTML. And that’s where our problem begins.
These “QR Codes” are being created with ASCII characters. The idea is to bypass OCR engines. Here’s what the HTML looks like:

Essentially, the threat actors are putting in small blocks in the HTML. In the email, it will look like a QR code. But to a typical OCR, it doesn’t look like anything. There are websites that help threat actors generate these automatically, and then can still be configured to include malicious links.
Here’s another example:
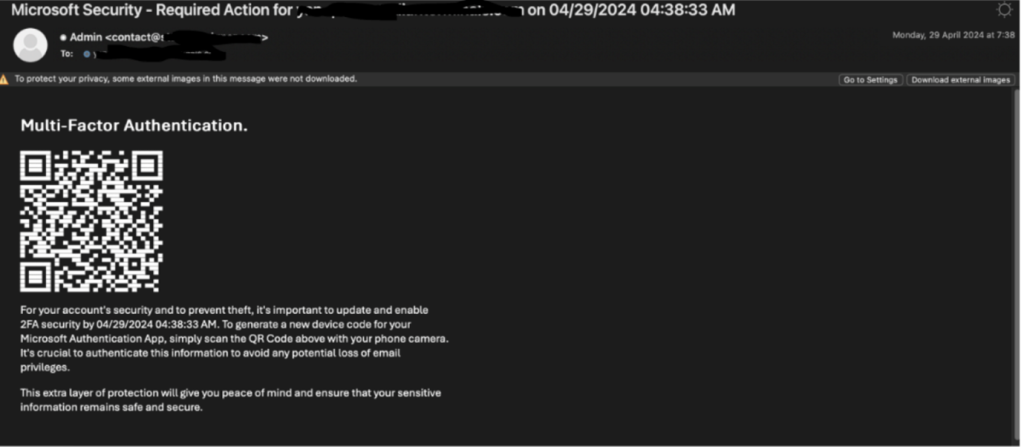
Like many QR code phishing attacks, the email is around a re-authentication request. But the QR code has ASCII characters behind it, which could lead security systems to ignore it and think it’s a clean email.
Techniques
Attack forms all evolve. QR code phishing is no different. It’s unique, though, that the evolution has happened so rapidly. It started off with standard MFA verification codes. These were pretty straightforward, asking users to scan a code, either to re-set MFA or even look at financial data like an annual 401k contribution.
The second iteration, QR Code Phishing 2.0, was conditional routing attacks. The link looks for where the user is interacting with it and adjusts accordingly. If the user is on a Mac, one link appears. If the user is on an Android phone, another one pops up. We also saw custom QR Code campaigns, where hackers are dynamically populating the logo of the company and the correct username.
Now, we’re seeing QR Code 3.0, which manifests itself as a manipulation campaign. It’s not actually a traditional QR code, but rather a text-based representation of one. This makes it incredibly difficult for OCR systems to see it and detect it.
It also represents how threat actors are responding to the landscape. Practically every email security vendor made a huge splash about new QR code protection (HEC has had them in place since 2019). Many use some form of OCR . Hackers know this and have adjusted their campaigns accordingly.
It’s the never-ending cat-and-mouse game of cyber security. Hackers find something to exploit. Cyber security defenders find a solution. Hackers find something to exploit. And so on.
It happens with every attack form, and QR codes are no different.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that automatically decodes QR codes embedded in emails and analysed the URLs for malicious content
- Utilise security that rewrites the embedded QR code in the email body and replaces it with a safe, re-written link
- Implement security that utilises advanced AI to look at multiple indicators of phishing




