The Criticality of Security: How to Address the Modern Challenge of Securing APIs

Application Programming Interfaces (API) are dominating the Internet, with successful API requests accounting for 57% of the Internet traffic (dynamic HTTP traffic) processed by Cloudflare so far in 2024. This trend will only continue, leading to more API vulnerabilities and increased efforts for more stringent regulations.
Alarmingly, it appears organisations are not aware of the exact number of APIs they are using, with Cloudflare’s machine learning models discovering 30.7% more API endpoints than what organisations have previously self-reported. These “shadow APIs” may not be inherently malicious, but because they are APIs that haven’t been managed or secured, they do leave critical security gaps that threat actors can exploit.
Equally worrying, Cloudflare anticipates that cybercriminals will increasingly target workflow APIs, exploiting their relative stability compared to web app user interfaces and their often-weaker security, leading to more efficient and frequent attacks. This is why Cloudflare estimates that attacks on workflow APIs will become more prevalent and sophisticated, driven by the fact that APIs are less frequently updated and inherently less secure than web app interfaces.
In short, the API landscape is about to get a whole lot more challenging.
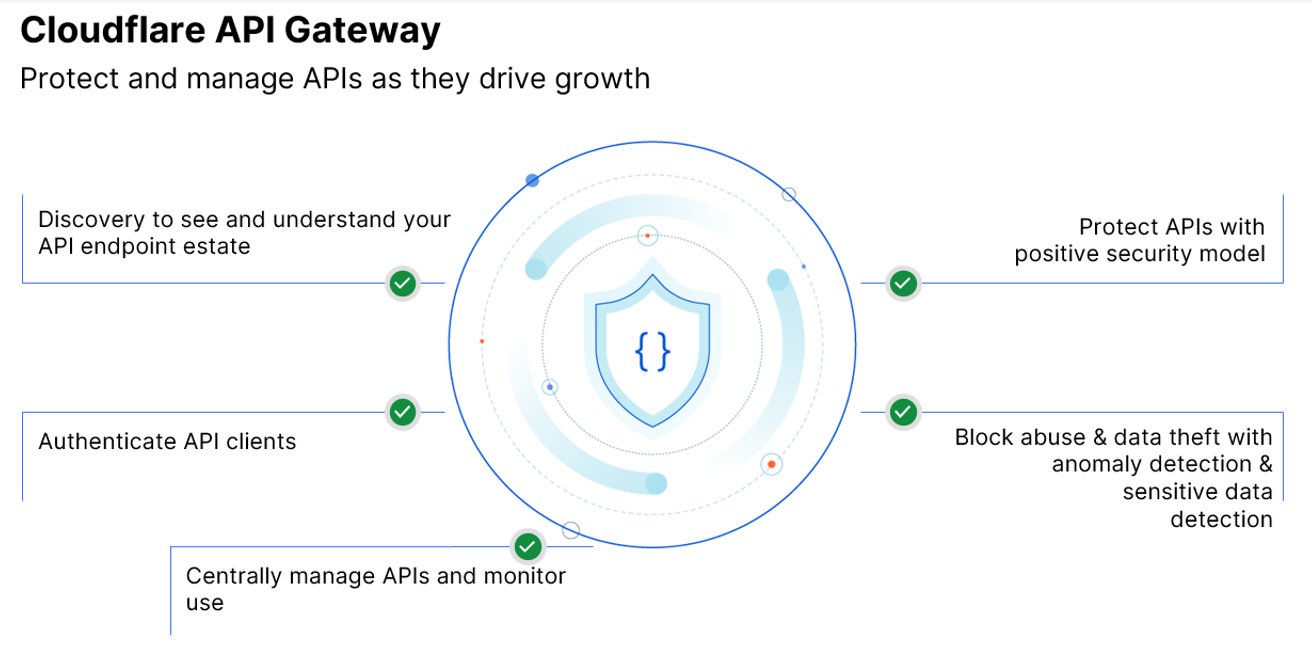
Cloudflare can help organisations meet this challenge head-on with the Cloudflare API Gateway, which automatically discovers, secures, and monitors API endpoints across an organisation’s entire digital landscape—but without slowing business innovation. In other words, Cloudflare API Gateway helps companies protect and manage APIs by:
- Enabling them to completely see and understand their API endpoint estate.
- Protecting APIs with a positive security model.
- Centrally managing the organisation’s APIs and monitoring usage.
- Authenticating API clients.
- Blocking abuse and data theft with anomaly detection and sensitive data
Cloudflare API Gateway also leverages layered API security that includes:
- L3 and L7 DDoS to stop all volumetric DDoS attacks at network and application layers.
- Strong authentication to authenticate mobile and IoT with mTLS while confirming credentials are not compromised.
- Positive API security model that blocks everything except traffic that conforms to the schema, which is in contrast to the negative security model that blocks the “known bad”—problematic IPs, ASNs, and countries or requests with problematic signatures.
- Anomaly detection that stops API abuse with advanced rate limiting that block blocking of volumetric anomaly.
- Sensitive data protection that prevents sensitive data from leaking via API.
The growing importance of APIs in today’s digital landscape cannot be overemphasised, as they play a crucial role in adding functionality to existing applications or websites without having to build them from scratch. But this rise to prominence has come at a cost: These all-important APIs are getting harder to manage by the day, leaving critical security gaps that expose organisations to increasingly sophisticated threats. This underscores the need for better ways to protect these digital assets—and, by extension, the company itself—so they can do what they’re supposed to do without compromising the organisation.
So, are you ready to protect these valuable digital assets? Download this e-book to find out more about the common issues organisations face with APIs and the ways to best secure them.