Bridging the Data Protection Gap Between M365 and Ransomware

Microsoft 365 (M365) is picking up, with an unprecedented 50% growth in subscriptions—translating to over 300 million users—in just two years. On the rise as well is ransomware. With the number of attacks increasing exponentially over the years, it is now one of the biggest cyber threats facing businesses, with Cybersecurity Ventures expecting ransomware pay-outs to reach a staggering USD $1.75 trillion—TRILLION!—by 2025.
The problem here is that your M365 data is not entirely protected from ransomware, even if Microsoft does offer a level of built-in protection, including retention and versioning capabilities. None of these, however, are backups. Even OneDrive’s 93-day retention and 30-day recovery point provision are wholly inadequate versus ransomware, which can infect and then hide for weeks or months before launching an attack. What’s more, versioning in either OneDrive or Sharepoint is not suitable to recover from ransomware because recovery needs to happen from a specific point in time on the entire data set—not individual files—to ensure the data is clean from ransomware infection.
That is the extent of protection you get from M365, and the rest is up to you as dictated by the shared responsibility model in protecting data in the cloud. Under this model, customers are responsible for their data, while the cloud provider—Microsoft in the case of M365—is responsible for infrastructure availability and uptime only.

And so that begs the question: What is the best way to protect your data under the shared responsibility model?
Taking the SaaS Approach to Combat Ransomware
The best course of action would be to deploy a reliable, cloud-based data management solution that empowers you to perform three key steps to properly defend your data:
- Adopt fast, flexible protection and recovery.
- Secure backups.
- Meet SLAs and simplify hybrid cloud operations.
This makes Data Management-as-a-Service (DMaaS) the ideal solution for data protection, particularly against ransomware. With DMaaS, which is an effective form of SaaS data protection, it is the vendor that organises, maintains and updates all the necessary infrastructure, software and hardware for effective and efficient data management, effectively augmenting your end in the shared responsibility model.
Choosing the Right SaaS Data Protection For Your Business
Your choice of third-party SaaS data protection truly matters as this will determine how effective it can help you recover from a ransomware attack. In short, you need a reliable, best-in-class platform—exactly the kind Cohesity offers.
Among the as-a-Service solutions Cohesity offers is Cohesity DataProtect, which enables fast and flexible recovery that can recover data from any point in time and do it fast and make immutable backups to keep your data from being tampered with or deleted during a user-defined retention period.
Enhancing Cohesity DataProtect is Cohesity FortKnox. It is another as-a-service offering by Cohesity that provides customers with an easy way to create a third copy of backup data—only this time, this backup is isolated in a secure data vault in the AWS cloud— that can be recovered back to its source location or to alternate locations in case of a ransomware attack or any other incident that compromises your primary and secondary copies.
Cohesity FortKnox simplifies complex data isolation and recovery methods through a modern SaaS solution for isolating data in the cloud. That also minimises attack surfaces and improves recovery time SLAs. FortKnox even enhances ransomware attack and recovery preparedness by identifying clean copies of data to minimise the risk of re-infection and by providing an environment for sandbox testing of recovery operations.
The isolation techniques of FortKnox provide an organisation with the perfect balance of isolation and RPO/RTO so it can better meet its operational objectives. This means enabling the organisation to quickly recover from cybersecurity incidents while, at the same time, supporting SLAs and improving cyber resilience. The graph below demonstrates this critical relationship, where protected replication with isolation is the preferred approach:
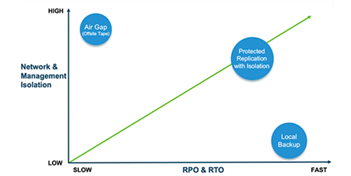
In addition, FortKnox updates the industry standard 3-2-1 Rule by allowing the off-site copy to be an isolated replication for data to be both protected and agile. This enables rapid recovery from ransomware and all other attacks.
The rise of ransomware—along with other threats—requires a next-gen approach, and that is precisely what Cohesity provides. The DataProtect and FortKnox offerings included as part of its SaaS data protection platform are crucial to simplifying data management and enabling comprehensive protection against threats of all kinds.
Download the “Ransomware Protection for Microsoft 365” guide to learn more about the impact of ransomware on M365 and your broader IT environment. The guide also explores in-depth critical considerations for protecting your data and recovering from an attack.





