Cybercriminals Hide Phishing QR Codes in PDFs to Bypass Detection – Barracuda Threat Spotlight
Cybercriminals Are Evolving, and Cybersecurity Experts Are Faced with a New Challenge

Cybercriminals are using phishing QR codes hidden in PDF attachments to bypass defences and steal sensitive information, according to a new Threat Spotlight from Barracuda.
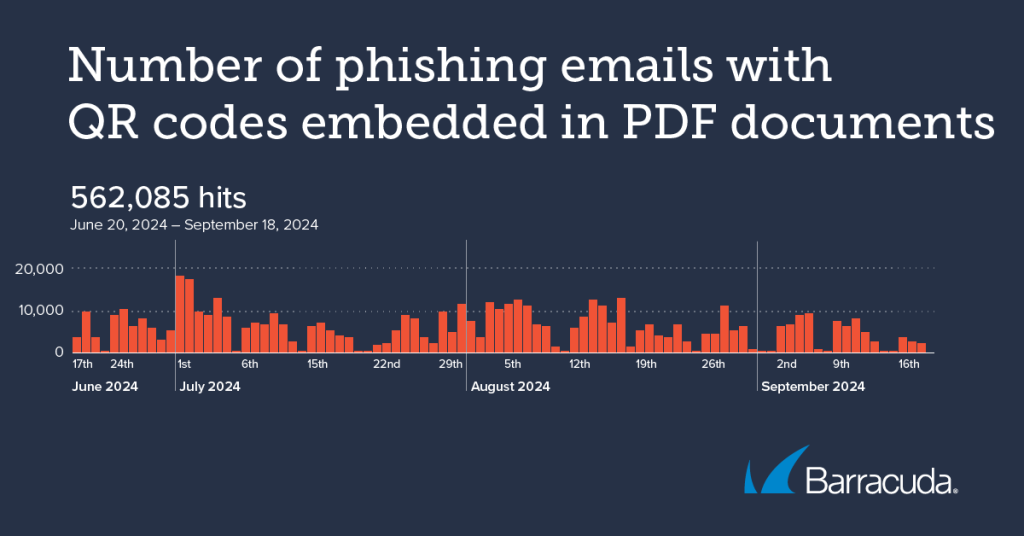
Analysing a snapshot of data over a three-month period (June–September), Barracuda researchers detected over half a million phishing emails using this tactic, which they highlight is an evolution from attackers embedding the codes directly in emails, making these campaigns more difficult for organisations to detect and prevent.
QR code phishing, also known as quishing, is a type of social engineering attack. Cybercriminals try to trick victims into using the camera on their mobile phone to scan a QR code that links to a malicious website to steal sensitive information, such as login credentials or financial data.
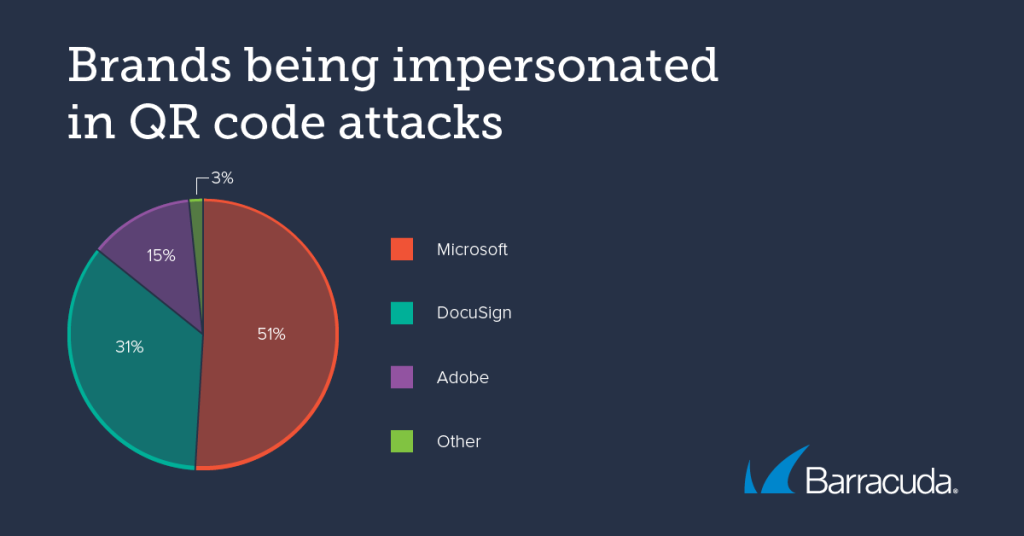
According to Barracuda researchers, the PDF documents attached to phishing emails exploit brand impersonation and urgency to lure individuals to scan the code. They also revealed that many of these phishing emails mimic well-known brands. Microsoft, along with its services like SharePoint and OneDrive, was impersonated in 51% of the attacks, followed by DocuSign at 31% and Adobe at 15%. In fewer cases, scammers pretended to represent the human resources department of the targeted company.
Typically, these phishing attempts with phishing QR codes involve a simple one or two-page PDF that includes a phishing QR code and lacks further external links or embedded files. The email directs users to scan the phishing QR codes to access a file, sign a document, or listen to a voice message. However, scanning the code redirects victims to a phishing site aiming to capture login details.
Phishing QR Codes Represent a New and Unique Challenge for Cyber Teams
Quishing poses some unique security challenges for businesses. Traditional email filters struggle to detect these attacks because there are no direct links or suspicious attachments to scan. Additionally, quishing often involves multiple devices: employees receive the phishing email on one device but scan the phishing QR code using a different device, such as a personal mobile phone that may lack the same level of security protection as corporate systems. As a result, these attacks can bypass corporate defences, making them difficult to track or prevent.
Commenting, Kyle Blanker, Manager, Software Engineering, at Barracuda, said: “Traditional email threat scanners can miss phishing content and malicious payloads if they are embedded within PDFs, which makes this an attractive tactic for attackers trying to evade detection. Between June and September our security technologies detected around half a million attempted attacks where weaponised QR codes were embedded in PDFs.
“Phishing is a relatively low cost, easy to implement attack vector with potentially high rewards, so it is not surprising that attackers are continuously trying new approaches to overcome the latest advances in protection. For examples, our security researchers have recently reported on a new generation of phishing QR codes built from text-based ASCII/Unicode characters and using specially crafted URLs to create hard-to-detect phishing pages.”
Adam Khan, VP Global Security Operations at Barracuda, added: “Cybercriminals are constantly refining their phishing techniques to make attacks appear more legitimate and convincing to the unsuspecting victim, with the use of QR codes in PDF documents being one of many tactics we’re closely tracking. These attacks can easily evade traditional email filters, making them difficult to detect.
“Organisations must adopt multilayered email security with advanced AI that analyses not just links and attachments, but also potential impersonation attempts within attachments. Educating users about the risks of scanning phishing QR codes from unknown or questionable sources is essential. Additionally, ensuring that spam and malware filters are properly configured, conducting regular health checks on email gateway settings, and enabling multi-factor authentication will significantly enhance overall protection.”
Read more here: https://blog.barracuda.com/2024/10/22/threat-spotlight-evolving-qr-codes-phishing-attacks.




