Most Educational Organisations Paid More Than the Original Ransom Demand, Says Sophos Survey

Sophos, a global leader of innovative security solutions that defeat cyberattacks, today released findings from its annual sector survey report, “The State of Ransomware in Education 2024.” According to the report, the median ransom payment was $6.6 million for lower education and $4.4 million for higher education organisations. In addition, the survey states that 55% of lower education respondents and 67% of higher education respondents paid more than the initial demand.
Ransomware attacks are causing more of a strain as only 30% of ransomware victims surveyed in both lower and higher education were able to fully recover in a week or less, down from last year’s 33% (lower education) and 40% (higher education). This slowing recovery rate is likely due to education organisations operating with limited teams and resources, making it harder for them to coordinate recovery efforts.
“Unfortunately, schools, universities and other educational institutions are targets that are beholden to municipalities, communities and the students themselves, which inherently creates high-pressure situations if they are hit and destabilised by ransomware. Educational institutions feel a sense of responsibility to remain open and continue providing their services to their communities. These two factors could be contributing to why victims feel so much pressure to pay,” said Chester Wisniewski, Director, Field CTO, Sophos.
“We also know that ransomware attackers have upped the ante when it comes to getting paid. Compromising their victims’ backups is now a mainstream element of ransomware attacks, giving adversaries the opportunity to subsequently increase the ransom demand when it is clear that the data cannot be recovered without the decryption key.”
In fact, 95% of respondents said that cybercriminals tried to compromise their backups during the attack, with 71% being successful – the second-highest backup compromise rate across all industry sectors. Having backups compromised also considerably increases recovery costs, with the total bill coming in five times higher in lower education and four times higher in higher education.
Sophos Findings
Despite difficult dealings with ransomware, the overall attack rate dropped over the last year. Sixty-three percent of lower education organisations and 66% of higher education organisations were hit by ransomware attacks – down from 80% and 79%, respectively. At the same time, the rate of data encryption has increased slightly, with eighty-five percent of attacks on lower education and 77% of attacks on higher education organisations resulting in data encryption, slightly up from the 81% and 73%, respectively, reported in the 2023 survey. Unfortunately, cybercriminals are not only encrypting data, they’re also stealing it, using it as leverage to further monetise the attack. Twenty-two percent of lower education organisations that had data encrypted said the data was also stolen, together with 18% in higher education.
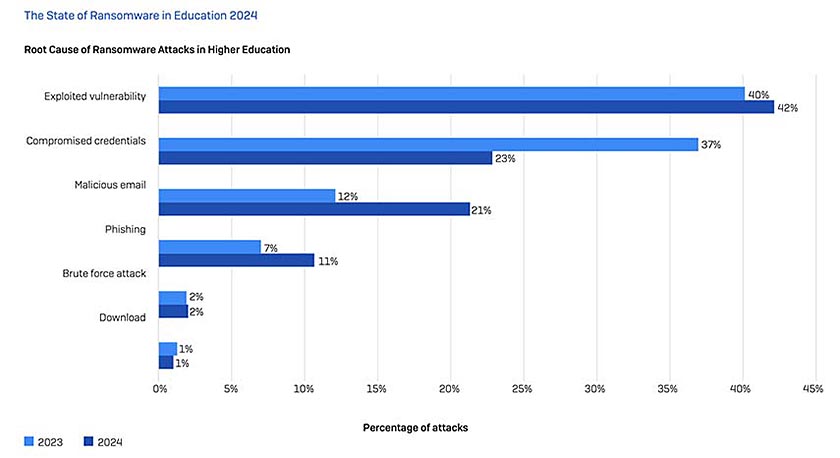
The survey reveals that exploited vulnerabilities were the leading root cause of attacks in education, providing cybercriminals with a way into the network for 44% of lower education and 42% of higher education ransomware attacks.
Based on this Sophos survey data, schools and other educational organisations could benefit from a layered security approach that includes vulnerability scanning and patching prioritisation guidance to reduce their attack surface, endpoint protection with anti-ransomware capabilities that automatically detect and stop attacks, and 24/7 human-led managed detection and response (MDR) services to neutralise advanced human-led attacks, ideally leveraging telemetry from backup solutions to detect and stop adversaries before they can cause damage.
“While there appears to be some positive progress towards combatting ransomware in the education sector, it’s concerning that the rate of data encryption continues to increase year after year, which suggests educational organisations need to continue working towards improving their ransomware resilience. With stretched resources and limited budgets, education organisations need to focus on the controls that will have the greatest impact. With the median ransomware recovery cost for education now hitting $3 million, it’s clear that investing in strong prevention and protection solutions can considerably reduce the overall financial impact of cyber to educational organisations,” said Wisniewski.
Sophos’ report this year incorporates new areas of study: insight into the role of law enforcement in ransomware remediation for education providers. Ninety-nine percent of lower education and 98% of higher education organisations engaged with law enforcement and/or official government bodies following a ransomware attack. As a result, 64% of lower education organisations and 66% of higher education organisations benefitted from advice about dealing with the attack. Sixty-one percent of lower and higher education organisations received help and support investigating the attack, and nearly 49% of lower education organisations and 48% of higher education organisations sought law enforcement’s help recovering data encrypted in the attack.
Data for the State of Ransomware in Education 2024 report comes from a vendor-agnostic survey of 600 cybersecurity/IT leaders working in the education sector conducted between January and February 2024. Respondents were based in 14 countries across the Americas, EMEA, and Asia Pacific. All respondents represent organisations with between 100 and 5,000 employees.
Read the full State of Ransomware in Education 2024 report on Sophos.com for additional global findings and data by sector.




