Group-IB Reveals Covert BEC Phishing Empire Targeting Microsoft 365

Group-IB, a global cybersecurity leader headquartered in Singapore, has published a new threat report “W3LL DONE: HIDDEN PHISHING ECOSYSTEM DRIVING BEC ATTACKS”. The report details the operations of W3LL, a threat actor behind a phishing empire that has remained largely unknown until now. Group-IB’s Threat Intelligence and Cyber Investigations teams have tracked the evolution of W3LL and uncovered that they played a major role in compromising Microsoft 365 business email accounts over the past 6 years.
The threat actor created a hidden underground market, named W3LL Store, that served a closed community of at least 500 threat actors who could purchase a custom phishing kit called W3LL Panel, designed to bypass MFA, as well as 16 other fully customized tools for business email compromise (BEC) attacks. Group-IB investigators identified that W3LL’s phishing tools were used to target over 56,000 corporate Microsoft 365 accounts in the USA, Australia, and Europe between October 2022 and July 2023. According to Group-IB’s rough estimates, W3LL’s Store’s turnover for the last 10 months may have reached $500,000. All the information collected by Group-IB’s cyber investigators about W3LL has been shared with relevant law enforcement organizations.
Do not Talk about W3LL Club
W3LL’s cybercriminal career can be traced back to 2017 when they entered the market with W3LL SMTP Sender – a custom tool for bulk email spam. Later, W3LL developed and started selling their version of a phishing kit for targeting corporate Microsoft 365 accounts. The growing popularity of the convenient toolset prompted the threat actor to venture into opening a covert English-speaking underground marketplace. The W3LL store began operations in 2018. Over time, the platform evolved into a fully sufficient BEC ecosystem offering an entire spectrum of phishing services for cybercriminals of all levels, from custom phishing tools to supplementary items such as mailing lists and access to compromised servers.
W3LL Store provides “customer support” through a ticketing system and live webchat. Cybercriminals who do not have the skills required to leverage the tools can watch video tutorials. W3LL Store has its own referral bonus program (with a 10% commission on referrals) and a reseller program (with a 70/30 split on the profits made by third-party vendors from selling on W3LL Store).
At present, the W3LL store has more than 500 active users. To become a W3LL store customer, newcomers need to be referred by existing members. New users have 3 days to make a deposit to their balance, otherwise, their account will be deactivated. The developer does not advertise the W3LL store and asks their customers to refrain from spreading the word about it online. Group-IB identified over 3,800 items sold via the marketplace between October 2022 and July 2023. Over 12,000 items are currently on sale. W3LL’s Store’s turnover for the last 10 months was estimated to be $500,000.
Revealing W3LL Infrastructure
W3LL’s major weapon, W3LL Panel, may be considered one of the most advanced phishing kits in class, featuring adversary-in-the-middle functionality, API, source code protection, and other unique capabilities. W3LL Panel does not have a variety of fake pages and it was designed to compromise Microsoft 365 accounts specifically. However, due to its high efficiency, the phishing kit became trusted by a narrow circle of BEC criminals. W3LL offers a 3-month phishing kit subscription for $500, with subsequent months costing $150 each. Each copy of W3LL Panel has to be enabled through the token-based activation mechanism, which prevents the kit from being resold or its source code being stolen.
As of August 2023, in addition to the W3LL Panel phishing kit, the marketplace offers 16 other fully customized tools entirely compatible with each other that all together constitute a complete setup for BEC attacks. These tools include SMTP senders (PunnySender and W3LL Sender), a malicious link stager (W3LL Redirect), a vulnerability scanner (OKELO), an automated account discovery instrument (CONTOOL), reconnaissance tools, and many more. The tools are available on a licensing basis and cost between $50 and $350 per month. Furthermore, W3LL regularly updates its tools, adding new functionalities, improving anti-detection mechanisms, and creating new ones, which underlines the importance of staying up-to-date with the most recent changes in their TTPs.
Phishing W3LL: Geography of Operations
Phishing campaigns involving W3LL tools are highly persuasive and usually involve several W3LL-developed instruments that cover almost the entire kill chain of BEC attacks, all the while providing a high level of automation and scalability. After compromising a target, threat actors proceed to the account discovery phase and then may employ one of the following scenarios: data theft, fake invoice scam, account owner impersonation, or malware distribution using the compromised email account. The consequences for a company that has suffered a BEC attack can go beyond direct financial losses (which may range from thousands to millions of dollars) and could extend to data leaks, reputational damage, compensation claims, and even lawsuits.
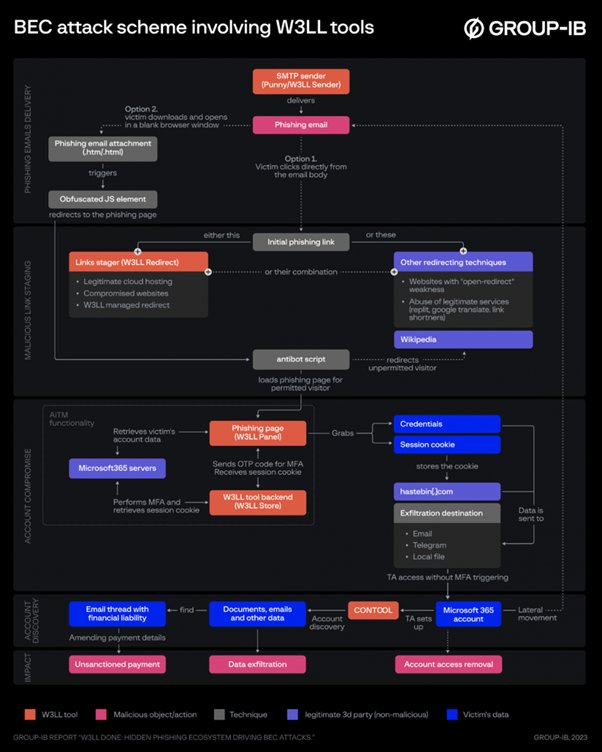
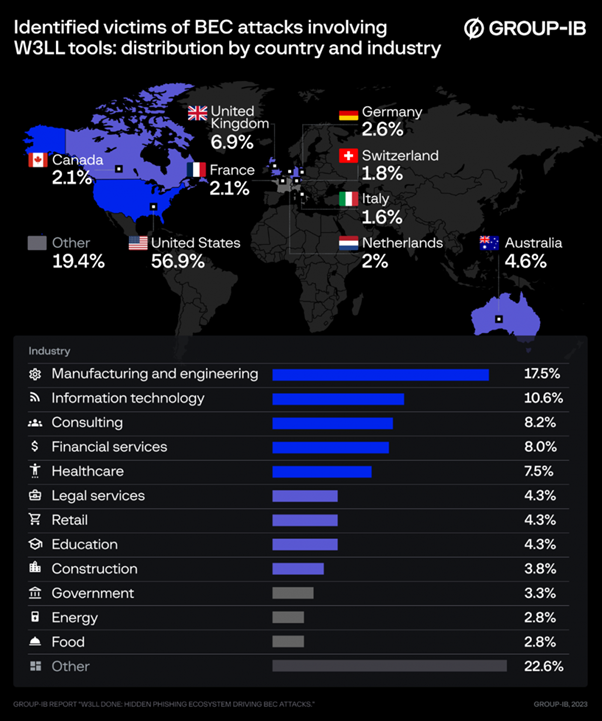
Group-IB researchers identified close to 850 unique phishing websites attributed to W3LL Panel over the last 10 months. By analyzing Telegram groups and chats controlled by W3LL as well as the infrastructure related to W3LL phishing campaigns, Group-IB researchers established that during the same period, BEC threat actors who used W3LL’s tools targeted at least 56,000 corporate Microsoft 365 business accounts and more than 8,000 (about 14.3%) of them were ultimately compromised. The actual number of victims and the final impact could be significantly higher. W3LL tools are designed to target companies regardless of their origin, but most of the identified targets are organizations in the USA, Australia, the UK, and other countries in Europe (Germany, France, Italy, Switzerland, Netherlands). The most frequently targeted industries, as identified by Group-IB, are manufacturing, IT, financial services, consulting, healthcare, and legal services.
“What really makes W3LL Store and its products stand out from other underground markets is the fact that W3LL created not just a marketplace but a complex phishing ecosystem with a fully compatible custom toolset that covers almost the entire killchain of BEC and can be used by cybercriminals of all technical skill levels,” says Anton Ushakov, Deputy Head of Group-IB’s High-Tech Crime Investigation Department, Europe. “The growing demand for phishing tools has created a thriving underground market, attracting an increasing number of vendors. This competition drives continuous innovation among phishing developers, who seek to enhance the efficiency of their malicious tools through new features and approaches to their criminal operations.”
Group-IB’s new report is available for download here. The report contains a list of Indicators of Compromise (IOCs) as well as YARA rules that can be used to hunt and detect W3LL Panel phishing pages.