Leveraging a Managed Detection and Response (MDR) Provider to Anticipate Cybersecurity Threats

As the saying goes “prevention is always better than cure” but if you don’t know what’s wrong, how can you prevent it?
Cybersecurity has been a major topic of discussion within the past few years as the technology becomes more sophisticated and cybercriminals become bolder. Ensuring your company is protected against cyber threats is not only a concern to your stakeholders but also to current and potential customers.
In 2011, the hacktivist organisation Anonymous launched Operation Malaysia, which targeted 91 websites, including 51 government websites. The strikes came after the Internet vigilante group Anonymous threatened to attack the government’s official portal in retaliation for blocking Wikileaks, a website that tries to expose governments and companies by leaking secret documents. The majority of Malaysian websites targeted by Anonymous during the attack were crushed beneath the boot of botnet-fueled distributed denial of service attacks but several were actually infiltrated and defaced. Despite the fact that most websites were restored within 24 hours of the attack, undisclosed financial and intelligence losses would lead Malaysia to be one of the most cyber-protected countries today.

Being breached can have devastating effects on the reputation and credibility of your organisation. With data breaches making headlines on a regular basis, customers ought to be wary of the companies they do business with. Consider the Operation Malaysia incident, which escalated to the point where national classified sovereignty was breached.
Operating in the midst of these threats, how can your organisation prove that you are prepared to protect customer data?
It takes no less than around-the-clock surveillance to stand a chance against a cyber attack and deploying reliable MDR capabilities seems to be the solution. What is an MDR you may ask?
MDR (Managed Detection and Response) is an outsourced service that provides end-to-end cybersecurity protection that responds to threats as soon as they are detected. Its purpose is to equip an organisation with the necessary tools and expertise to pinpoint attacks and prevent them in real-time. Log entries consist of a wealth of information that can facilitate the identification of problems and patterns.
By monitoring the log entries, MDRs may be able to discover suspicious activities that could indicate an attack on organisational systems. It can also assist in the recording of baseline behaviour of equipment, systems, or users in order to spot anomalies that need to be investigated – utilising use cases, easy access at console and a visualised dashboard for easier detection of anomalies.
In effect, MDRs will analyse, investigate and report their findings and help prevent similar attacks in the future. By leveraging MDR, your organisation can benefit from faster responses to cyber attacks which will, in turn, minimise cost and most importantly protect customer trust.
Now, consider what it would take for an organisation to build such capabilities from the ground up. It would need an incident response program, assemble a security and incident response team (which may include security engineers, analysts, SOC managers, threat hunters, researchers and data scientists), devise a communications plan, escalation and notification, etc, to enable the most critical components of MDR – such as threat intelligence, threat hunting, round-the-clock security monitoring, incident analysis, and real-time incident response. All this could easily cost an organisation over USD $1 Million annually.
The problem is that not all organisations have the resources to build and maintain a dedicated team to fend off and anticipate cyber attacks. Does this mean there is no hope at all?
Absolutely not! With the rise of as-a-Service models in various areas of tech, MDR is the answer to identify active threats across an organisation and then respond to eliminate them. By depending on an MDR provider, you are essentially outsourcing your cybersecurity to external experts who can monitor and analyse threats to your company reactively and proactively through a subscription model.
Bluesify offers the most advanced cyber threat centre in Malaysia with their 24×7 Cyber Security Operations Centre. Their cyber threat centre offers XDR, 24/7 MDR and response automation to protect the organisations that they serve. With real-time advanced threat intelligence, non-stop cybersecurity monitoring and incident response services, and cybersecurity consulting services alongside security advisory and vulnerability management, Bluesify can address your cybersecurity needs.
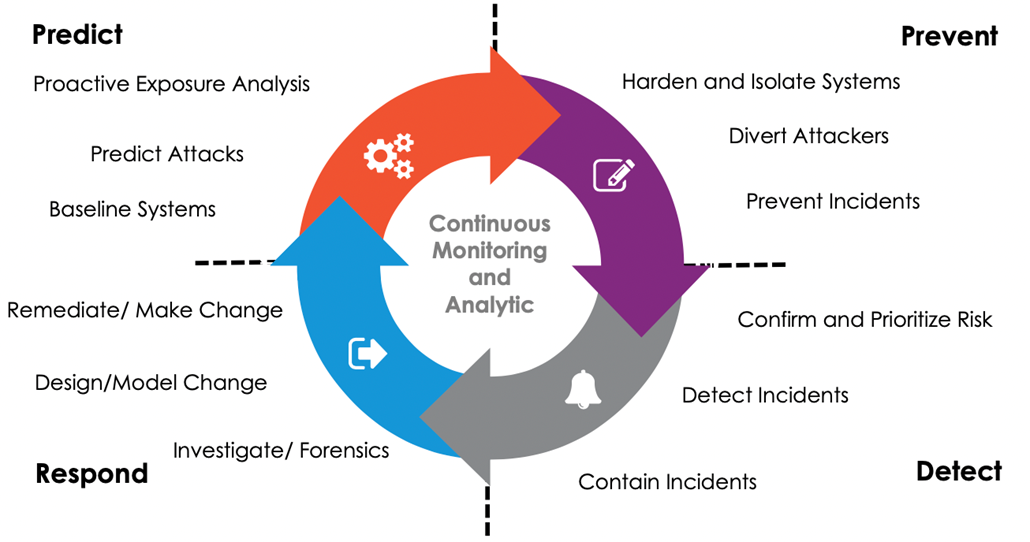
Their cyber threat centre can help to address 12 critical capabilities (Reference Garner) with continuous monitoring and analytics in order to prevent, detect, respond and predict incoming cyber attacks. Through Bluesify, your organisation has the luxury of anticipating cyber threats before they happen, ensuring the safety of your customer data and your organisation’s reputation. How they do that is nicely summarised in this diagram:

The growth of the cyber threat landscape, particularly post-pandemic, has been both mind-boggling and concerning. It usually goes back and forth in the cat-and-mouse race. Statistics demonstrate, however, that cybercriminals are constantly several steps ahead in this race. At this point, precautionary measures are no longer complementary and should be considered seriously before escalating to something worse than a financial hit to your organisation.
It’s time to take a proactive stance against cyber attacks. Click here to find out how Bluesify’s cybersecurity solutions can help your organisation fortify its defences.





