Remote Ransomware Attacks Surge 50% as Threat Actors Exploit Shared Drives
Remote ransomware attacks are on the rise as cybercriminals increasingly target shared drives through unmanaged endpoints.

A sharp increase in remote ransomware attacks is raising alarm across the cybersecurity landscape, as attackers move away from traditional infection models and adopt stealthier, more targeted approaches. Sophos reports that the remote ransomware incidents rose by 50% year-over-year in 2024, marking a 141% increase since 2022.
Unlike conventional ransomware, which typically executes on a victim’s machine and encrypts local files, remote ransomware operates out of sight. It leverages compromised, unmanaged endpoints as access points to encrypt files stored on other devices across the network. This technique not only evades traditional endpoint defences but also exploits overlooked vulnerabilities in enterprise environments.
A Shift in Attack Methodology

CyberSecurity Asia was able to reach Chester Wisniewski, Director and Global Field CISO at Sophos to enlighten this case further. He explained in an email interview that the primary issue lies in how most endpoint security tools function.
“Most endpoint security products only monitor for ransomware and encryption processes locally on the machine,” he said. “This leaves file shares on Windows Servers, NetApp boxes, etcetera vulnerable to be encrypted by an unprotected endpoint.”
Wisniewski also mentioned that the most common tactic involves using an unprotected device within the network as a jump box. Once the attackers breach such a device—often one already logged into the domain—they deploy malware that scans and encrypts any accessible shared folders. These can include file shares on protected machines, which remain vulnerable simply because the ransomware isn’t running locally on them.
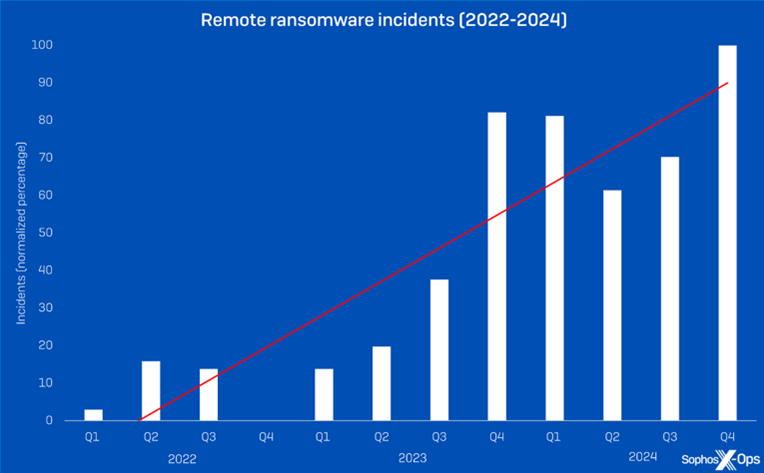
According to Sophos X-Ops data, remote encryption was relatively low throughout 2022 and the first half of 2023. However, the latter of 2023 saw a significant uptick, and the trend has maintained high levels ever since.
The Speed and Stealth of Remote Ransomware

Despite executing over the network, remote ransomware attacks are not slow. Wisniewski noted that in many enterprise setups, file servers are equipped with 10-gigabit ethernet, allowing attackers to access and encrypt data rapidly.
Modern ransomware tools are also designed for efficiency. The Sophos’ Global Field CISO also mentioned that some had used fast algorithms like CHACHA20, which only encrypt the first few hundred kilobytes of a file—just enough to render it unusable.
This combination of speed and stealth makes remote ransomware particularly dangerous. Since the malicious encryption doesn’t occur on the file’s host machine, detection mechanisms like memory scanning and behaviour monitoring are often bypassed entirely.
Exploiting the Unmanaged
The root of many remote ransomware attacks lies in unmanaged devices—endpoints that are not protected by enterprise-grade security solutions.
These devices often have weaker access controls and are less frequently monitored. Microsoft’s 2023 Digital Defence Report found that 60% of human-operated ransomware attacks involved remote encryption, with 80% of compromises originating from unmanaged devices. By 2024, that figure rose to 70% for successful attacks involving remote encryption.
The attack lifecycle typically begins with gaining access through misconfigured permissions, stolen credentials, or both. “The techniques are no different than in most attacks with active adversaries,” Wisniewski said. “They will often use exploits to elevate their privileges to administrative rights. This is far easier on an unprotected device than on one using a modern sophisticated XDR solution.”
Detecting the Invisible

Spotting a remote ransomware attack before damage is done is not easy, but there are early indicators.
Unusual patterns in file access logs or network traffic, such as a single endpoint suddenly accessing a broad range of file shares, can raise red flags. Wisniewski suggested that behavioural analytic tools that monitor anomalies in access patterns may help defenders respond before files are fully encrypted.
The threat intelligence veteran had also mentioned that certain solutions like Sophos CryptoGuard can detect remote encryption activity and isolate file shares from the network in real time to prevent further tampering.
Still, the core prevention strategy remains consistent, which is to eliminate blind spots and enforce uniform protection across all endpoints.
Minimising Risk in a Shifting Landscape
Although organisations are becoming more aware of ransomware as a threat, the nature of remote encryption means many still underestimate how easily attackers can circumvent existing defences. This evolving threat highlights the urgent need for businesses to reassess how they monitor file activity and secure unmanaged devices within their networks.
Sophos recommends several mitigation strategies to stay protected against remote ransomware:
- Active asset management – Maintain visibility over all devices and endpoints.
- Identify unmanaged machines – Regularly scan for rogue devices that may serve as attack vectors.
- Monitor file activity in real time – Use tools that can track and flag unusual file transfers.
- Enforce good cyber hygiene – Apply strong passwords, software updates, multi-factor authentication, and regular staff training.
As remote ransomware becomes more common, endpoint protection won’t suffice. Organisations need layered defences with behavioural monitoring and full network visibility to stay ahead of threats that never even touch their core systems.



