Disrupting the Disruptor: A Step-by-Step Strategy to Stonewall DDoS Attacks

Service delays are bad for business. Service denial is even worse.
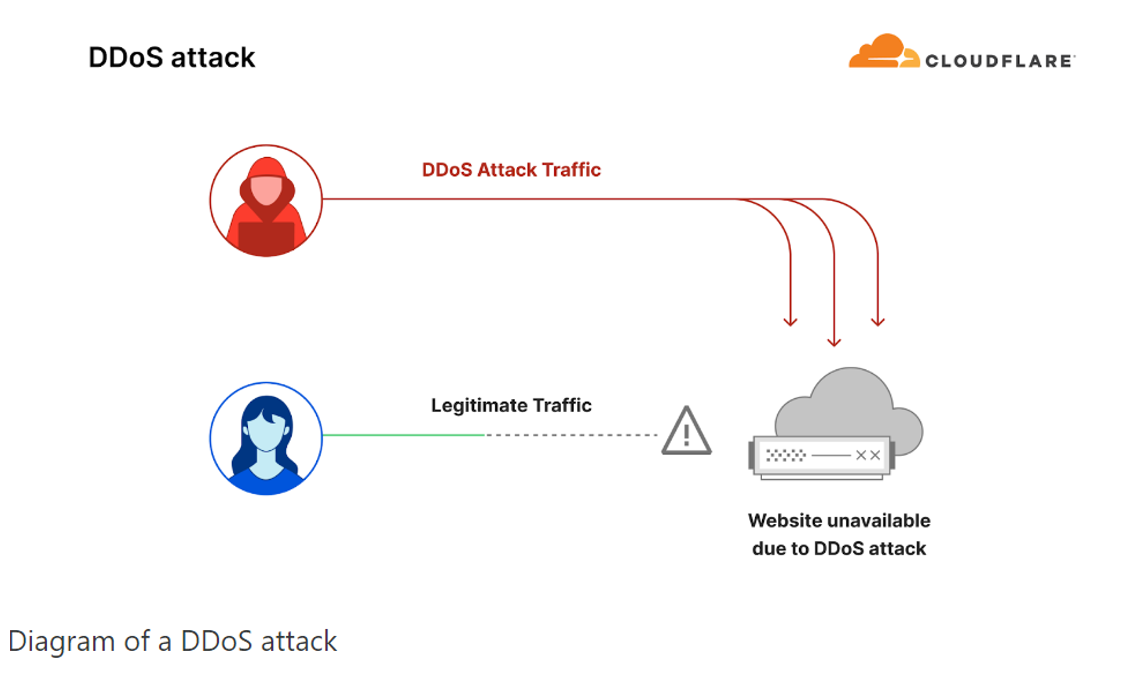
Distributed Denial-of-Service (DDoS) attacks can do both, overwhelming a targeted server, service, or network with a flood of Internet traffic to disrupt normal operations and leave users in the dark and unable to access what they need. They are quite common as well, with Cloudflare mitigating a staggering 8.5 million attempts in the first half of 2024 alone—accounting for a 20% year-on-year increase and 60% of the total attacks (approximately 14 million) Cloudflare mitigated in all of 2023.
Those alarming numbers shouldn’t come as a surprise given the sheer number of DDoS attacks threat actors can toy with. These include Slowloris, where attackers keep multiple connections open with a slow and continuous HTTP; Telnet DDoS attacks, where attackers exploit defects in Telnet by sending many irrelevant data frames to throttle the connection; and Ping of Death, where attackers exploit vulnerabilities in certain operating systems.
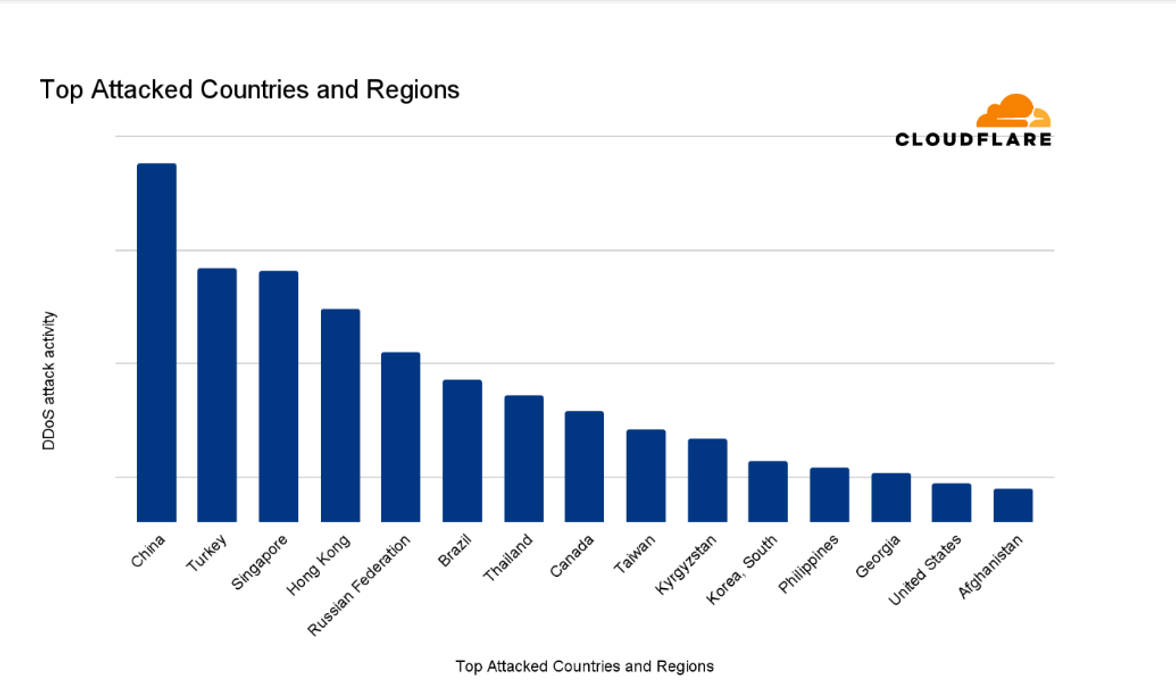
Aside from growing in frequency, these attacks are also becoming more and more sophisticated, making DDoS attacks a formidable threat that deserves the full attention of organisations. This is particularly true for businesses in Singapore, Hong Kong, Thailand, and the Philippines, which are 3rd, 4th, 7th, and 12th in Cloudflare’s list of top attacked countries—joining fellow Asian nations China, Taiwan, South Korea, and Afghanistan.
This grave threat is getting noticed. The Cyber Security Agency of Singapore (CSA), no doubt cognisant of the serious threat DDoS attacks pose on Singaporean businesses, has issued guidelines on how to best deal with DDoS attacks. The guidelines—contained in an advisory—cover a step-by-step approach that highlights the importance of preparing for, identifying, containing, and mitigating these attacks while also minimising their impact on business operations. The steps are as follows:
- Govern. Governance is a critical tone-setter where organisations outline cybersecurity policies that specifically address DDoS risks, define everyone’s roles and responsibilities, ensure top management support, and allocate resources effectively.
- Identify. This is where organisations identify potential vulnerabilities and risks associated with DDoS attacks, and it involves assessing risks, conducting asset inventories, and understanding the normal traffic patterns of your network. The goal is to detect any anomalies that may signal the start of a DDoS attack.
- Protect. Protective measures must be implemented after vulnerabilities are identified. Critical measures to implement include deploying Web Application Firewalls (WAFs), Content Delivery Networks (CDNs), and load balancers that can absorb and redistribute excessive traffic.
- Detect. Early detection is the key to stonewalling DDoS attacks. Organisations need to leverage real-time monitoring tools and threat intelligence feeds—the kind that Cloudflare’s best-in-class DDoS protection provides—to do early detection and respond accordingly and immediately.
- Respond. A well-prepared response plan can make all the difference between shutting down an attack and getting attacked. This plan must cover everything from escalation procedures to predefined steps for activating mitigation technologies—Cloudflare’s industry-leading DDoS mitigation comes to mind—and everything in between.
- Recover. After the attack has been contained, the focus must shift to restoring normal operations as quickly as possible. This stage includes conducting a post-incident analysis to identify lessons learned and improving defences against future attacks.
These guidelines also underscore the preeminent role the three pillars of cybersecurity—people, process, and technology—must play in mitigating DDoS attacks, with a well-trained staff supposed to respond to threats following set processes and using the right technologies.
This critical interplay between people, process, and technology will be even more vital in the days ahead as DDoS attacks grow more frequent and more sophisticated. Without a well-coordinated and multipronged approach to mitigation, these risks will turn into full-blown attacks, slowing down services or denying them outright—to the detriment of any business.
That’s why it’s time to get ahead and deny these attacks. Discover how Cloudflare can protect your business—click here to learn more.