Mitigating Cyber Attacks Through Micro-Segmentation
If you have already implemented micro-segmentation for your network, you are one step ahead! If not, it’s time for you to consider doing so, sooner rather than later.
A well-protected network perimeter is crucial to establishing a robust security architecture. After all, it makes perfect sense to defend against external threats looking to break into your organisation’s network via “north-south” traffic—or traffic between your internal network and the Internet. But if you focus solely on shoring up your network perimeter, you might not be protecting what’s inside adequately. If so, that is a loophole that many threat actors can exploit.
Cybercriminals are actively looking to exploit such loopholes in potential victim networks. They find a way in—either by exploiting the weakest point of an organisation’s network perimeter defence, leveraging social engineering, or utilising someone on the inside to get them in undetected. Once in, they can implant whatever malware or virus they want and then let “east-west” traffic spread the attack. East-west traffic is one that moves from one network segment or internal host to another, and threat actors leverage this method to travel within the network—often undetected. This is why east-west traffic is being targeted more and more.
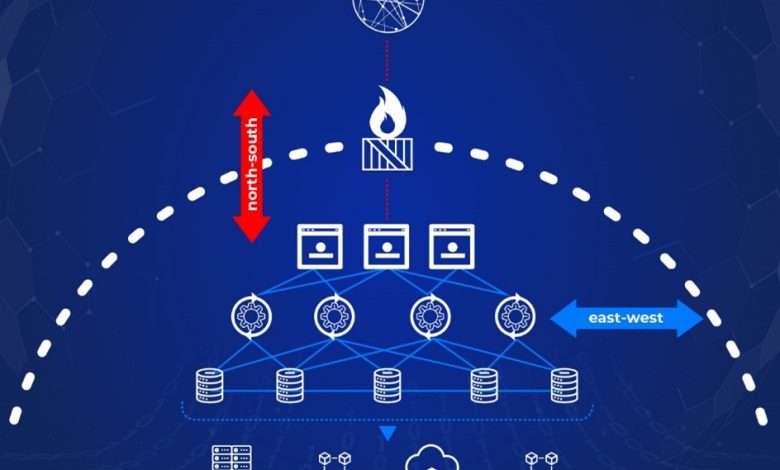
Take a look at Figure 1, which shows north-south and east-west traffic, and why the latter is potentially a problem area:
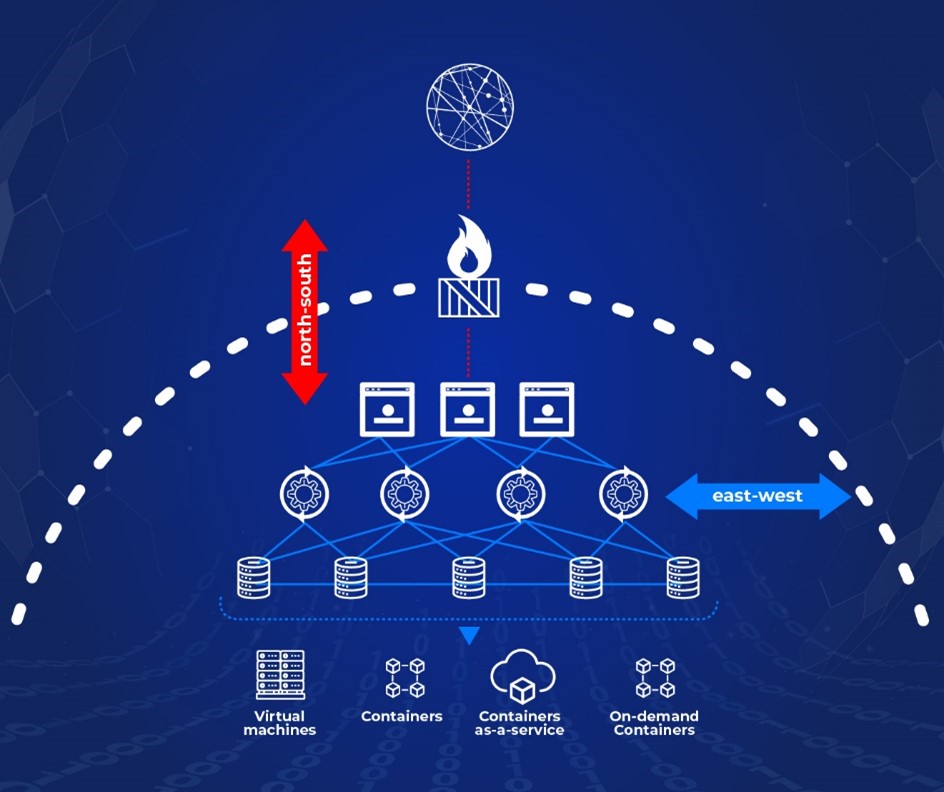
Figure 1: North-south traffic vs. East-west traffic
This is where micro-segmentation comes in. Micro-segmentation is a network security strategy that divides the network environment into individual “segments,” with each one given its own security control and threat protection capabilities. This creates distinct security zones that secure each individual segment and contains threats that may have been implanted there. In doing so, threats are effectively isolated and kept from spreading to the other segments within the network, thus mitigating their impact. In a nutshell, micro-segmentation is essentially a set of mini policies and strict rules that regulate how traffic can flow and what can be allowed. It is one of the ways by which the Zero-Trust strategy is implemented—similar to how Machine-Learning (ML) is one of the ways of implementing Artificial Intelligence (AI).
Figure 2 shows a network that is micro-segmented as opposed to one that isn’t. Notice how a threat can spread easily without micro-segmentation and how micro-segmentation contains the attack to one zone only.
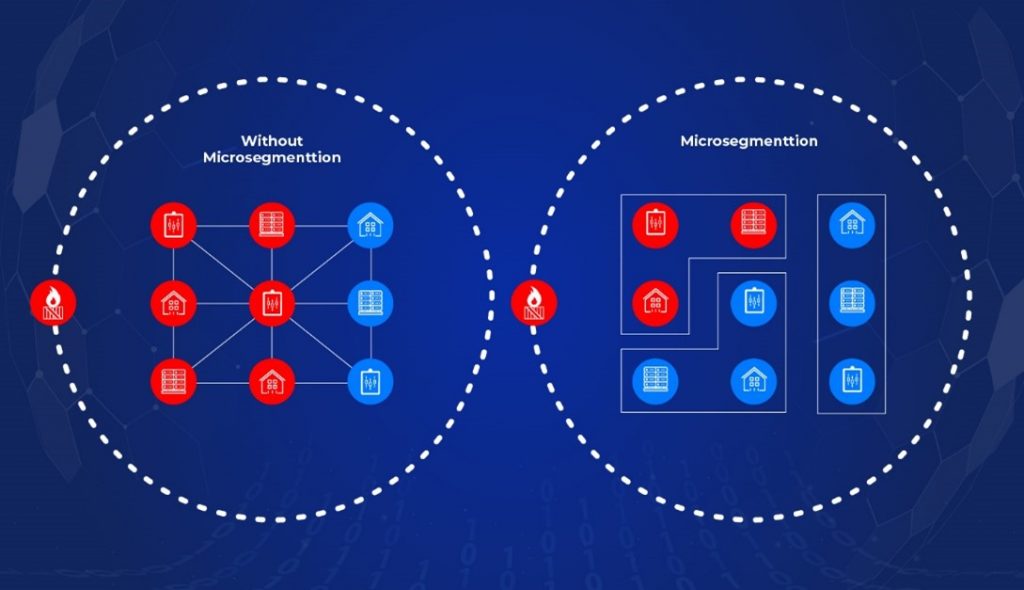
Figure 2. A network without micro-segmentation vs. a network with micro-segmentation
Micro-Segmenting the Private Cloud
Micro-segmentation adds a layer of security for cloud-based environments, where east-west traffic between shared physical and virtual resources is even more pronounced. This increases lateral movement within the cloud environment and is the reason micro-segmentation is needed. In fact, it has emerged as a highly effective method when it comes to securing cloud-based data centres, whether private or public.
Microsegmentation, incidentally, is one of the key features of CloudHive, a comprehensive Cloud Workload Protection Platform (CWPP) by Hillstone Networks that help organisations secure enterprise Virtual Machines (VM) in private clouds. It leverages microsegmentation technology to secure each VM, provides comprehensive visibility of east-west traffic and enables complete protection to stop lateral attacks between VMs. CloudHive “sees” all traffic from and into any and all VMs through Insight, whose advanced visualisation tools are also capable of spotting anomalous activities and suspicious behaviour. It is also easily scalable, allowing it to meet business needs without interruption.
With CloudHive, organisations can:
- Achieve unparalleled live traffic visibility by monitoring all VM access points, thus showing even the subtlest changes in the virtual network.
- Reduce the attack surface considerably through microsegmentation and augmented by L2–L7 security services, which include policy control and session limits.
- Monitor service performance in real-time by diving deep into the cloud environment and building the first line of security and defence for VMs—as well as the critical data and applications that reside in them.
- Improve efficiency while reducing costs by decreasing deployment and configuration overhead and minimising network interruption.
Being in the cloud can drive your organisation forward in the digital age but you will need to secure your cloud deployment, even if it is a private one. However, you cannot settle for just any run-of-the-mill security solution; you need one that offers micro-segmentation, which can effectively secure east-west traffic in your network. That solution is Hillstone CloudHive, as it provides complete visibility, comprehensive protection and easy scalability—all at a reasonable cost.
Click here to find out more.
If you wish to know more about CloudHive by Hillstone check out this interactive image.