Check Point Research Reveals Ongoing NFT Airdrop Scam
Check Point Research has issued an alert about a new and sophisticated NFT scam campaign targeting token holders of over 100 popular projects. The scam involves sending airdrops that appear to be from legitimate sources, such as the Ape NFT airdrop for APE token holders. These airdrops link to specially crafted websites designed to trick victims into connecting their wallets, thereby giving attackers full access to their funds.
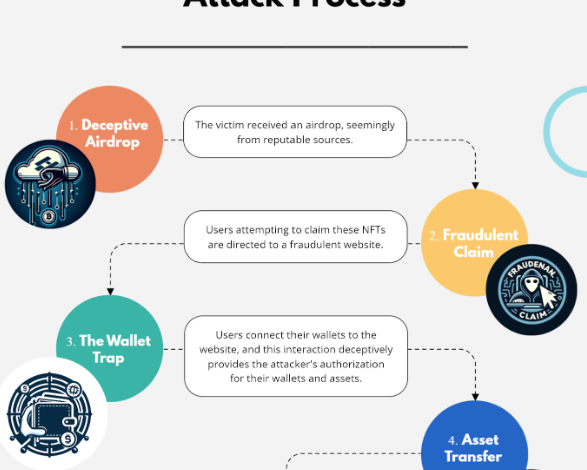
The scam unfolds in stages: recipients receive an airdrop from a seemingly reputable source, are enticed to claim a reward on a fraudulent website, and upon connecting their wallets, unknowingly authorise the attacker, leading to the theft of their funds.
Check Point Research’s investigation revealed that the attackers used a sophisticated infrastructure to distribute these fake airdrops to over 200,000 people. By analysing specific transactions, they found that the “From” addresses were spoofed, giving the illusion that the NFTs originated from credible sources like Yuga Labs or Immutable X.
The scam’s effectiveness lies in its use of blockchain technology’s complexities. Attackers exploit the way transaction information is processed and presented, using proxy contracts and unverified contract codes to obscure their actions. This approach makes it challenging for users and analysts to discern the true nature of the transactions.
.png)
How Did the Scam Work?
The scam uncovered by Check Point Research represents a complex and cunning exploitation of blockchain technology’s intricacies. The attackers, targeting token holders from over 100 popular projects, initiated their scheme by distributing airdrops that masqueraded as legitimate offerings from well-known sources, such as Yuga Labs and Immutable X.
The Stages of the Scam
-
Initial Contact: Victims first received an airdrop, carefully labelled to mimic a genuine offer from a trusted entity. For example, APE token holders received an airdrop seemingly related to Ape NFTs.
-
Luring to a Fraudulent Website: The airdrop included a link to a website, ostensibly for claiming the promised NFT reward. These sites were meticulously designed to appear legitimate and trustworthy.
-
Wallet Connection: Upon visiting the site, victims were prompted to connect their cryptocurrency wallets to claim their NFT or access some related benefit. This step mirrors common practices in legitimate NFT transactions, adding to the scam’s credibility.
-
Authorisation and Theft: By connecting their wallets, victims unwittingly authorised the attackers to access their funds. The scammers then proceeded to drain the wallets, completing the theft.
The sophistication of the scam lay not just in its deceptive appearance but also in its technical execution. The attackers used source spoofing techniques, where the “From” address in the transaction was manipulated to appear as if it was from a credible entity. This method exploited the way blockchain explorers like Etherscan process and display transaction information, making the scam difficult to detect for both users and automated systems.
Moreover, the scam involved the use of proxy contracts and unverified contract codes. These elements added layers of complexity and obfuscation, making it challenging for victims and analysts alike to discern the true nature of the transactions. The attackers leveraged the emit command in Solidity (used for recording logs on the blockchain) to create misleading information about the transaction’s origin.
This elaborate scheme underscores the evolving nature of threats in the digital asset space. It highlights the necessity for users to remain vigilant and sceptical, particularly when dealing with unsolicited airdrops or engaging with external links associated with digital assets. The scam is a stark reminder that in the world of blockchain and NFTs, where the excitement and perceived legitimacy can often cloud judgment, the best defence is a cautious and well-informed approach.
Users are advised to be wary, scrutinise links, understand smart contract interactions, and use trusted tools for verifying transactions. The report highlights the need for continual vigilance and scepticism in the digital asset environment, given the increasing sophistication of such scams.
The Threat Intel Blockchain system, developed by Check Point Software, continues to accumulate valuable information on emerging threats, and this intelligence will be shared in the future. In this collaborative effort, we aim to empower investors with the knowledge needed to navigate the crypto space securely and protect themselves from potential pitfalls.




