Barracuda Report: 44% of Ransomware Attacks Stopped During Lateral Movement

Our researchers analysed 200 reported/publicised incidents from August 2023 to July 2024, in 37 countries and involving 36 different ransomware groups. We included incidents in all industry sectors, with a focus on the primary categories we track year to year — municipalities, healthcare, education, infrastructure, and financial services.
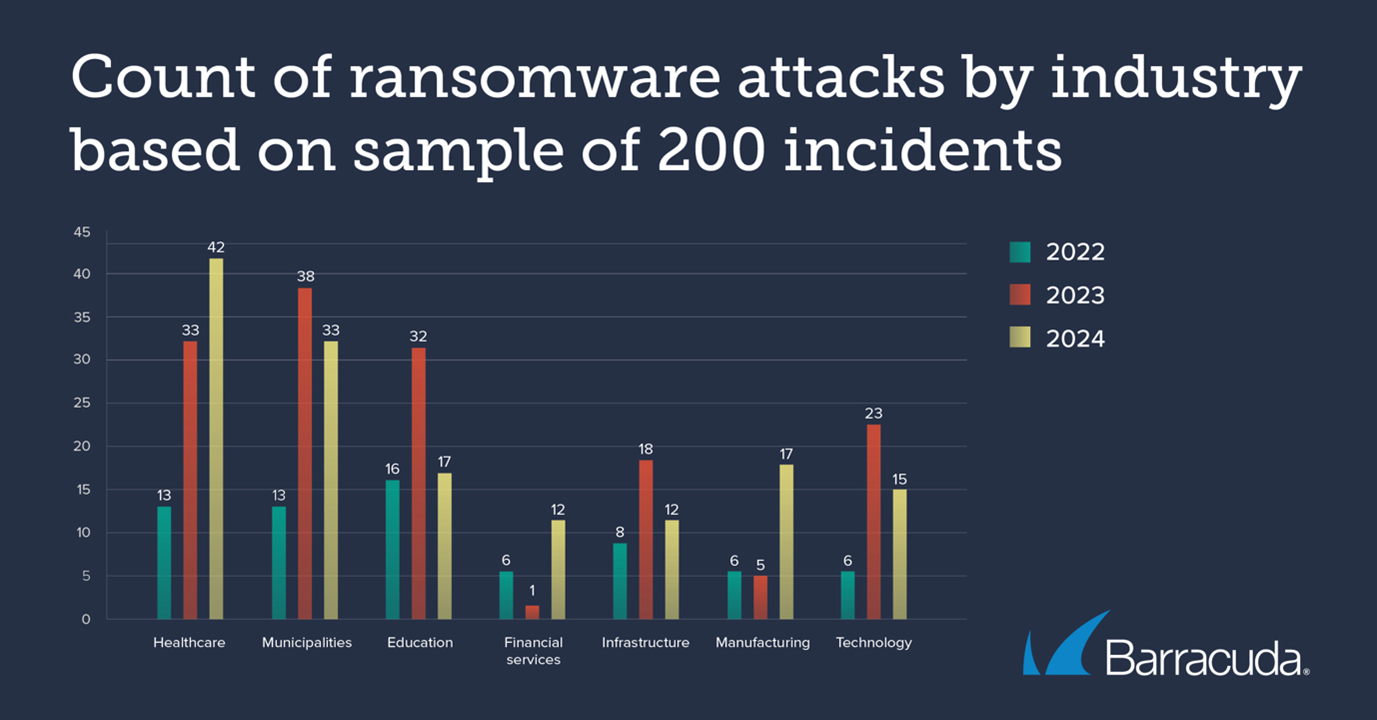
The sample shows that attacks against healthcare organisations continue to rise. Just over one in five attacks (21%) hit healthcare in 2023/24, up from 18% a year ago. Some of these made global headlines, with operations postponed and long-term treatment plans disrupted.
Incidents involving education halved from last year’s 18% to account for 9% of attacks in 2023/24, while those against financial services jumped from less than 1% to 6% in 2024.
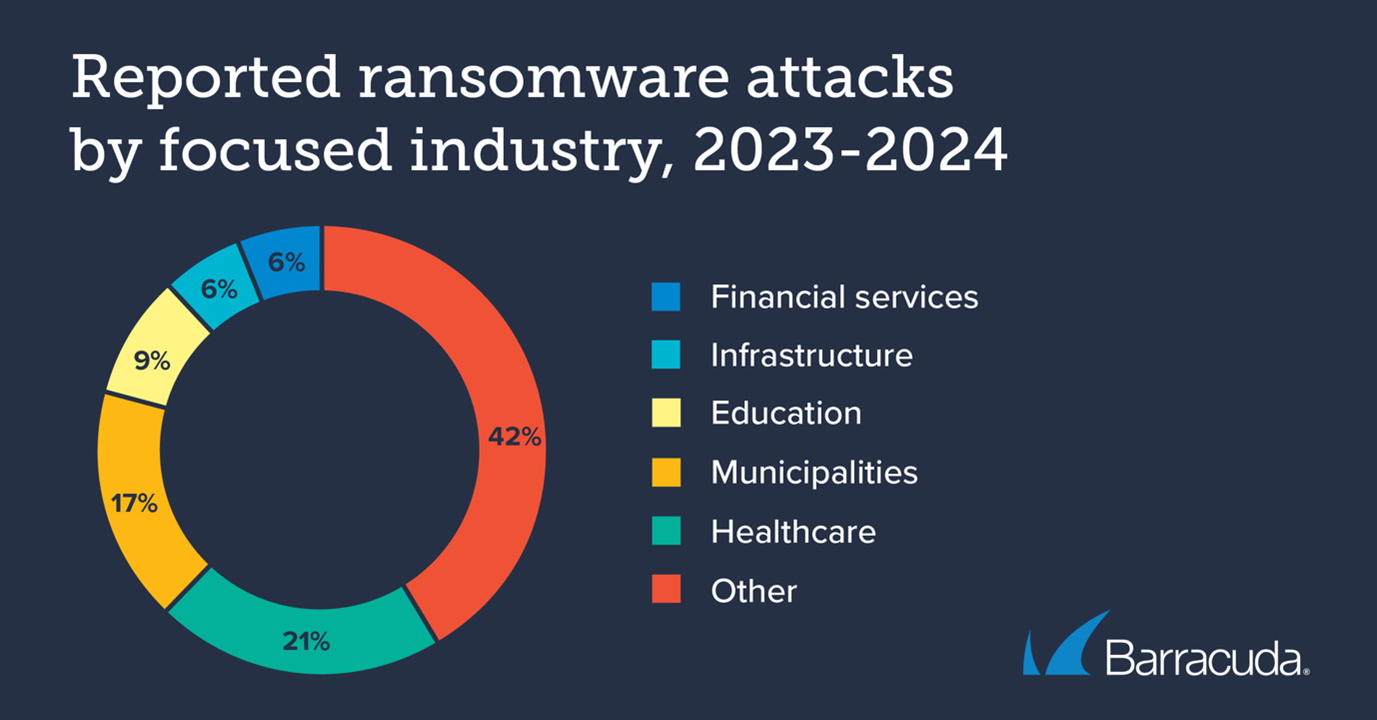
The proportion of attacks targeting other industries increased, with 42% of all attacks hitting sectors outside our focused group, up from 32% the previous year. In 2023/24, 15% of reported attacks were against manufacturing and 13% targeted technology companies.
These results are a timely reminder that every organisation in every industry is a potential target for ransomware.
It is worth noting that different regulations around the world mean that some organisations or industries have a legal obligation to report cybersecurity incidents, and this may influence industry-related results.
Ransomware For Rent
The most prevalent ransomware groups in our sample are, perhaps unsurprisingly, ransomware-as-a-service (RaaS) models. These include LockBit, which in 2023/24 was behind one in six, or 18% of the attacks where the identity of the attacker is known, despite the law enforcement takedown of the group in February 2024. Of these incidents, 28% targeted healthcare organisations, 21% municipalities, and 14% education.
ALPHV ransomware, also known as BlackCat, accounted for 14% of attacks in 2023/24 where the identity of the attacker is known, with a third of these incidents targeting healthcare organisations, while 17% hit financial services.
Rhysida, a new ransomware group that appeared in early 2023, accounted for 8% of named attacks, with 38% of them hitting healthcare.
RaaS ransomware attacks can be hard to predict and therefore contain. The number and range of affiliates implementing attacks from the same ransomware family can lead to significant variation in observed tactics, techniques, and procedures (TTPs).
Some affiliates may use different ransomware types in different attacks, further muddying the waters. Fortunately, there are tried and tested TTPs that most attackers rely on, and these can help to signpost an unfolding incident.
The Anatomy of Active Ransomware Attacks
Data from Barracuda XDR’s Endpoint Security suggests that in the first six months of 2024 (January 1 to the end of June), around one in four (23%) XDR customers faced an attempted ransomware attack.
In that time, Barracuda XDR’s Endpoint Security detected and blocked 6,052 instances (tools, techniques, or behaviours) that indicate a likely ransomware attack. The most prevalent detections represent navigational markers that security teams can look out for when hunting intruders.
Top Attack Tools and Behaviours Detected In 2024
Security analysts rely on a range of detection rules and engines to identify activity that denotes the presence of cyber threats. These multiple detection layers are essential in the battle against active threats such as ransomware, where attackers often leverage commercially available tools used legitimately by IT teams and can make real-time adjustments in their behaviour and tactics to succeed.
Further, the execution of the ransomware component of the attack, such as file encryption, is often the final phase of the incident. This is often preceded by scanning, lateral movement, malware download, and more, which offer security teams several opportunities to detect, contain, and mitigate ransomware incidents before they have a chance to fully unfold.
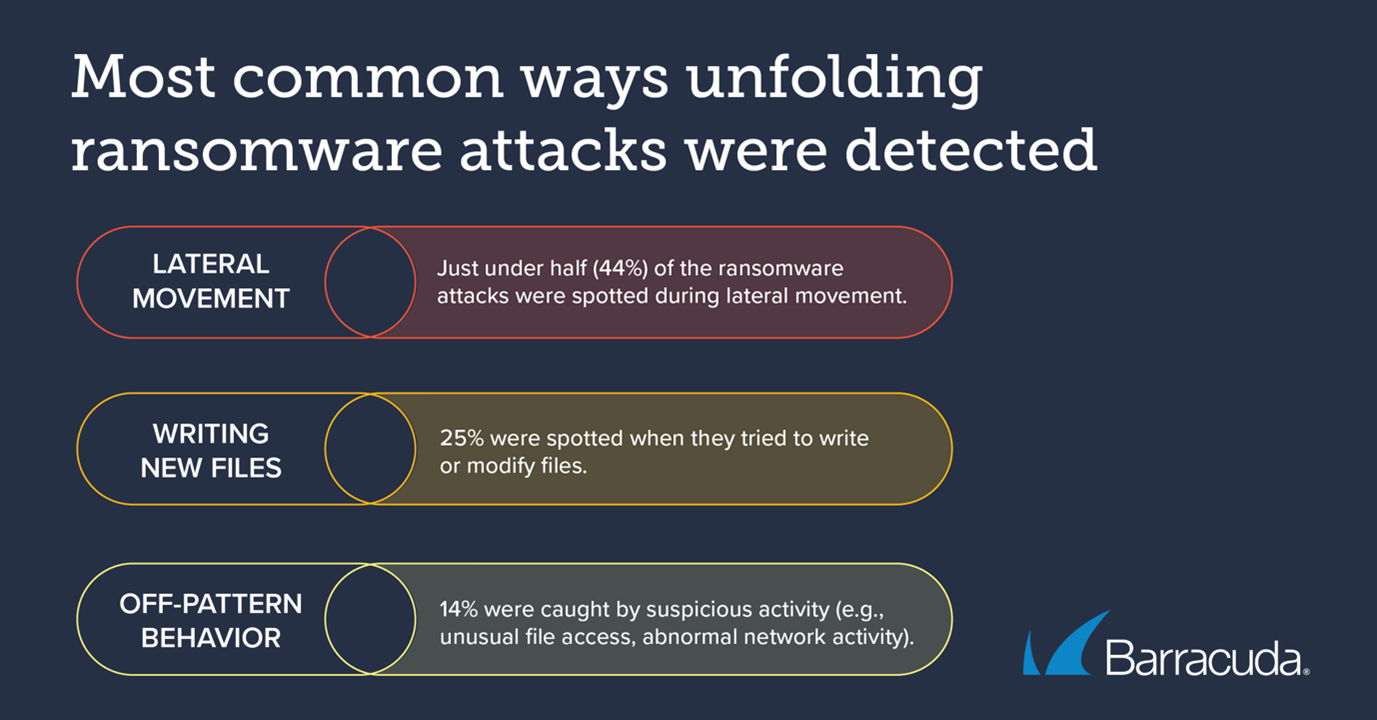
The data for 2024 shows that lateral movement is the clearest sign of ransomware activity. Just under half (44%) of the ransomware attacks were spotted by the lateral movement detection engine.
A quarter (25%) were detected by the engine that spots when files are being written or modified and analyse them to see if they match any known ransomware signatures or suspicious patterns, and 14% were caught by the detection engine that identifies abnormal behaviour within a system or network. This engine learns the typical behaviour of users, processes, and applications. When it detects deviations (such as unusual file access, tampering with operating system components, or suspicious network activity), it triggers an alert.
Alongside the powerful detection engines, Barracuda’s Security Operations Center (SOC) analysts have developed custom rules to automatically identify and mitigate suspected threats and quarantine endpoints.
In the first six months of 2024, more than 3,600 security alerts were triggered based on these custom rules. Many of these threats can be seen in ransomware incidents, and they represent further warning signs for security teams that something untoward is underway.

Two Ransomware Attacks from The XDR Case Book
Case study 1:
- Target – A health technology company with 150 – 200 employees
- Threat actor – PLAY ransomware
The target had deployed security on most, but not all devices. This created a significant visibility and security gap.
The attackers gained access by compromising an account belonging to a third-party developer who was working for the target.
They then used the breached account to access the corporate VPN, which did not have multifactor authentication (MFA) enabled. Once inside the network, the intruders moved laterally before settling on an under-protected application server.
The main attack
From this vulnerable server, they established a link to 11 business critical servers and tried to delete shadow copies of files, disable security measures, and establish persistence using a commercial remote access tool.
The attackers also tried to hide malicious files in the video and music folders on computers.
As each malicious activity was executed, the security agent on protected devices promptly killed, quarantined, and remediated the threat files.
Eight minutes later, the attackers tried again.
Using the unprotected application server as a base, they started trying to remotely encrypt files on the 11 servers. They managed to partially encrypt files on a few devices before the servers were automatically isolated from the network, ensuring no further harm could be done.
The attackers were however able to exfiltrate data from a server that couldn’t be inspected by the security software.
In one final effort, the attackers tried to execute additional malware, including a file called killer.exe, which failed to kill anything before being annihilated.
The compromised account was disabled and changes to the firewall prevented further connections from the threat actor.

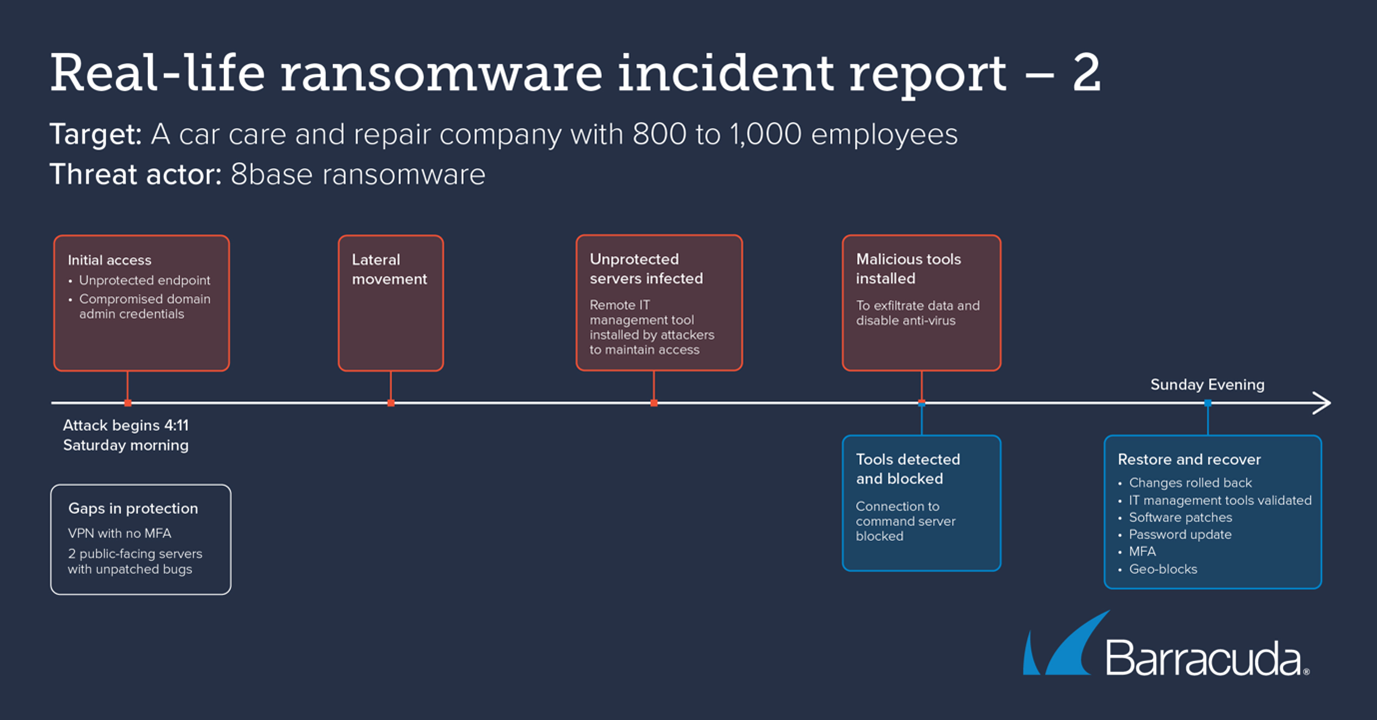
Case study 2:
- Target – A manufacturer of car care and repair products with 800 – 1,000 employees
- Threat actor – 8base ransomware
The attack took place over a weekend in January 2024.
Just before dawn on a Saturday morning in late January, cyber attackers used compromised or stolen domain admin credentials to gain remote access to a workstation.
The main attack
Over the next two days, the intruders expanded their footprint from the first compromised device, moving laterally to hundreds of devices within the infrastructure, infecting several unprotected machines.
The attackers leveraged a remote access service to establish persistent access to the infected servers.
The attackers then deployed the ransomware. They were able to encrypt several files. They also tried to disable security software and attempted to exfiltrate data. Most of this activity failed.
Even though not all devices were protected, there was enough security in place to prevent the attackers from fully encrypting affected machines and disabling the security.
Restore and Recover
The firewall blocked the attackers’ attempts to connect with their command-and-control and exfiltrate data.
By Sunday evening the attack was fully blocked and over. A total of 13 affected devices were “rolled back” to their pre-attack state, and a further six were restored manually.
In both examples, the target companies were advised to extend security to all devices to prevent and remediate any future attacks; to investigate all detected use of IT management and remote management tools; and to implement good cyber hygiene in terms of patching and passwords.
Conclusion: Building Resilience Against Ransomware Attacks
The ransomware landscape is evolving all the time, and that will continue. With so many different threat groups and affiliates in the game, it is challenging to predict exactly how attackers will behave. But there is a lot that companies can do to prepare and respond.
The priority should be to have measures and tools in place to detect and prevent a successful attack in the first place. These should ideally include multilayered security technologies, featuring AI-powered email protection and Zero Trust access measures, application security, threat hunting, XDR capabilities, and effective incident response to spot intruders and close gaps so that attackers cannot easily find their way in to install backdoors, steal, or encrypt data.
Don’t overlook the security basics: Keep software up to date, prioritise patching for known and exploited vulnerabilities, and implement regular cybersecurity awareness training for employees, as many ransomware attacks start with email-borne social engineering attacks such as phishing.
Reduce the attack surface by enforcing least-privilege access controls and closing public-facing or remote services that are not needed.
Double-check that any identified commercial IT administration tools are being used legitimately, and segment networks to prevent the spread of intruders and malware.
Implement encrypted, immutable backup systems that are segmented and isolated from the main network so that attackers cannot reach them, and which have strong authentication and access policies.
Last, but not least, ensure the organisation has an incident response plan in place about what to do in the case of a successful ransomware attack — with details about compliance and reporting requirements.
For more information on how to secure your organisation against ransomware visit this website.
For more information on Barracuda Managed XDR visit Managed Extended Detection and Response (Managed XDR) | Barracuda Networks.