CloudSEK Exposes Third-Party API Vulnerabilities as 30,000+ Public Workspaces Leak Sensitive Data
APIs Have Become Prime Targets of Cyber Criminals

CloudSEK’s TRIAD team, using their flagship platform XVigil, has identified major vulnerabilities stemming from the misuse of Postman workspaces—a widely-used API development and testing tool.
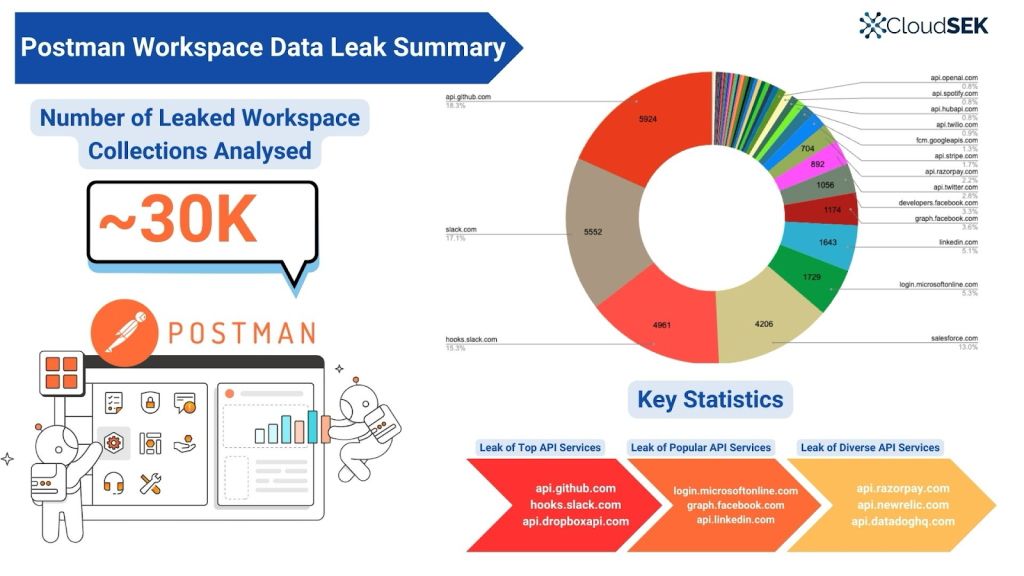
Over the course of a year, the CloudSEK team uncovered more than 30,000 publicly accessible workspaces leaking sensitive information about third-party API, posing severe risks to businesses and individuals alike.
Key Findings of the CloudSEK Report
- Over 30,000 publicly accessible Postman workspaces were discovered leaking sensitive information, including access tokens, refresh tokens, and third-party API keys.
- Leaked data spans organisations across various industries, from small businesses to large enterprises, with some owners of the leaked API keys/access tokens remaining unidentified due to inadequate permissions or API limitations, and it still poses risks to those leaked API Keys/ Tokens.
- Major platforms impacted include GitHub (5,924 exposures), Slack (5,552), and Salesforce (4,206), showcasing widespread misconfiguration.
- Critical sectors affected include healthcare, athletic apparel, and financial services, exposing organizations to significant security risks.
- Sensitive information uncovered includes administrator credentials, payment processing API keys, and access to internal systems, highlighting the potential for severe financial and reputational damage.
- CloudSEK has responsibly reported most identified incidents to affected organisations, helping mitigate risks.
Postman workspaces often contain sensitive data, including API keys, tokens, credentials, and documentation. When mishandled, this data becomes a treasure trove for malicious actors capable of exploiting vulnerabilities for financial fraud, data breaches, and reputational damage.
Investigation Highlights
- API Risks in Athletic Apparel. Leaked credentials from a Postman workspace exposed an athletic brand’s internal APIs, risking shipment data, invoices, and trade secrets.
- Healthcare Breach via Zendesk. Exposed admin credentials gave full access to a healthcare provider’s support system, threatening customer data and system integrity.
- Razorpay Key Exposure. Publicly shared API keys could enable unauthorised transactions and financial fraud.
- CRM Token Leak. A refresh token and API endpoint leak allowed unauthorised access to a CRM platform, risking data theft and session hijacking.
- New Relic Data Exposed. Leaked API keys provided access to sensitive system logs and infrastructure data.
- API Docs and Tokens Exposed. Public workspaces revealed API documentation and working tokens, enabling phishing, SQL injection, and service misuse.
In response to these findings, Postman has implemented new security measures, including proactive secret detection and user notifications when sensitive data is detected in public workspaces.
How Data Leaks Happen
The CloudSEK team’s findings emphasise common practices leading to sensitive data exposure, including:
- Inadvertent sharing of Postman collections.
- Misconfigured access controls.
- Syncing with publicly accessible repositories.
- Storing sensitive data in plaintext without encryption.
These vulnerabilities open doors to catastrophic consequences, from data breaches and unauthorized transactions to reputational and financial damages.
A Call to Action: Best Practices for Securing APIs
CloudSEK urges organisations to adopt robust security measures to prevent such exposures:
- Use environment variables to avoid hardcoding sensitive data.
- Limit permissions and review access controls regularly.
- Rotate tokens frequently and avoid using long-lived credentials.
- Leverage secrets management tools for secure data storage.
- Double-check collections before sharing and monitor activity logs for suspicious behaviour.
As API ecosystems grow increasingly complex, security lapses such as these can have far-reaching consequences.
For further details on our findings and actionable security insights, check the full report.