Krasue’s Curse: Group-IB Discovers New Linux Remote Access Trojan Targeting Companies in Thailand
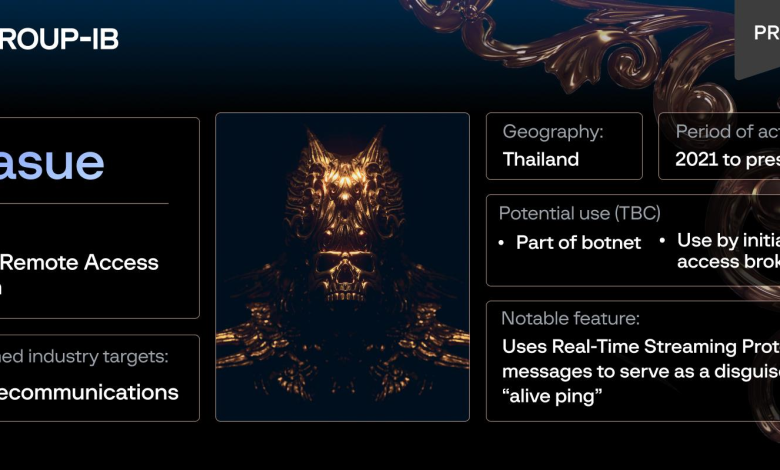
Group-IB, a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime, has discovered a new Linux Remote Access Trojan (RAT) that has been leveraged by cybercriminals looking to stealthily maintain access to the networks of targeted companies, which were exclusively based in Thailand. This Trojan, which has been named Krasue by Group-IB’s Threat Intelligence unit as a nod to the Thai name of a nocturnal native spirit known throughout Southeast Asian folklore, has been active since at least 2021, although remained under the radar for a significant period of time. At this stage, Group-IB researchers can confirm that Krasue was used against telecommunications companies in Thailand, although it has likely been part of attacks against organizations in other verticals.

Figure 1. Krasue profile made by Group-IB Threat Intelligence.
Upon discovery of Krasue, Group-IB’s Threat Intelligence customers were promptly notified of the threat, and Group-IB’s blog into this Linux RAT contains a full list of YARA rules so that organizations can actively hunt for this threat. Group-IB’s Computer Emergency Response Team (GIB-CERT) shared the report with the Thailand Computer Emergency Response Team (ThaiCERT) and the Thailand Telecommunications Sector Computer Emergency Response Team (TTC-CERT) in line with its zero-tolerance policy to cybercrime, and further research and outreach efforts are ongoing.
Krasue’s core functionality lies in its ability to maintain access to a targeted network, in the summer of 2023. The initial infection vector and the full scale of its usage have not been determined, but the Linux RAT could likely enter systems via vulnerability exploitation, credential brute force attacks, or more uncommonly, downloaded as part of a deceptive package or binary (i.e. a file masquerading as a product update) from an untrustworthy third-party source. The malware is able to conceal its own presence during the initialization phase, meaning that it can evade detection. Group-IB experts believe that Krasue is either deployed by malicious actors as part of a botnet, or access to Krasue is sold to other cybercriminals, such as ransomware gangs, by initial access brokers (IAB).
At the heart of Krasue is its rootkit, a piece of software used by cybercriminals to maintain privileged access to a computer while hiding its presence. Krasue’s rootkit is based on three open-source, publicly-available Linux Kernel Module rootkits, and Group-IB researchers also found that Krasue contained seven embedded rootkits that mean it can be functional on different versions of Linux. Krasue’s rootkit also contains multiple similarities with XorDdos, another Linux malware. As a result, Group-IB experts believe that Krasue was either created by the same author as XorDdos, or by an individual who had access to XorDdos’ source code.
Notably, Krasue uses Real Time Streaming Protocol (RTSP) — a network protocol designed for controlling the delivery of real-time media streams over IP networks — to communicate with its master command and control (C2 server). Group-IB researchers suspect that this tactic is a ploy that helps Krasue evade detection, although they note that using RTSP for this purpose is highly uncommon.
“Group-IB is committed to fighting against cybercrime in all its forms, and the discovery of Krasue, a sophisticated Linux Remote Access Trojan that has targeted organizations in Thailand, underscores the need for constant vigilance. Group-IB’s rapid response upon discovery of this malware and information sharing with ThaiCERT and TTC-CERT are vital steps towards countering this threat. Group-IB will continue to monitor Krasue’s spread both within Thailand and in other geographies, and take all measures to proactively inform affected parties,” Benyatip Hongto, Group-IB’s Business Development Manager, Thailand, said.
In March 2023, Group-IB announced its intention to open a Digital Crime Resistance Center in Thailand in order to counter the growing cyber risks in the country and provide localized support for Thai organizations. At the same time, Group-IB signed a partnership with leading Thai cybersecurity distributor nForce. Building on this momentum, Group-IB signed a memorandum of understanding with the Defence Technology Institute, a government agency under the supervision of the Minister of Defence of Thailand, in May 2023 to enhance knowledge sharing and collaboration in the development of the Defense Technology Institute Cyber Academy Program.