Rafel RAT: The Android Malware Powering Everything from Spying to Ransomware

When it comes to mobile devices, Android is the most popular and used operating system with over 3.9 billion active users in over 190 countries. Three-quarters of all mobile devices run on Android. However, with its widespread adoption and open environment comes the risk of malicious activity. Android malware, a malicious software designed to target Android devices, poses a significant threat to users’ privacy, security, and data integrity. These malicious programs come in various forms, including viruses, Trojans, ransomware, spyware, and adware, and they can infiltrate devices through multiple vectors, such as app downloads, malicious websites, phishing attacks, and even system vulnerabilities.
Check Point Research (CPR) has identified multiple threat actors utilising Rafel, an open-source remote administration tool (RAT). The discovery of an espionage group leveraging Rafel in their operations was of particular significance, as it indicates the tool’s efficacy across various threat actor profiles and operational objectives.
In an earlier publication, we identified APT-C-35 / DoNot Team utilising Rafel RAT. Rafel’s features and capabilities, such as remote access, surveillance, data exfiltration, and persistence mechanisms, make it a potent tool for conducting covert operations and infiltrating high-value targets.
CPR collected multiple malware samples from this Android RAT, and around 120 command and control servers. Further on, we conducted victims’ analysis and found that the most targeted countries were the United States of America, China, and Indonesia.
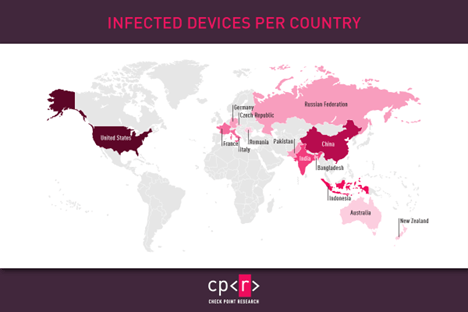
Figure 1 – Infected devices per country
The majority of victims had Samsung phones, with Xiaomi, Vivo, and Huawei users comprising the second-largest group among the targeted victims. This result corresponds to the popularity of the devices in various markets.

Figure 2 – Victims Devices
It is intriguing to note the distribution of Android versions among the most affected victims. Android 11 is the most prevalent, followed by versions 8 and 5. Despite the variety of Android versions, malware can generally operate across all. However, newer versions of the operating system typically present more challenges for malware to execute its functions or require more actions from the victim to be effective.
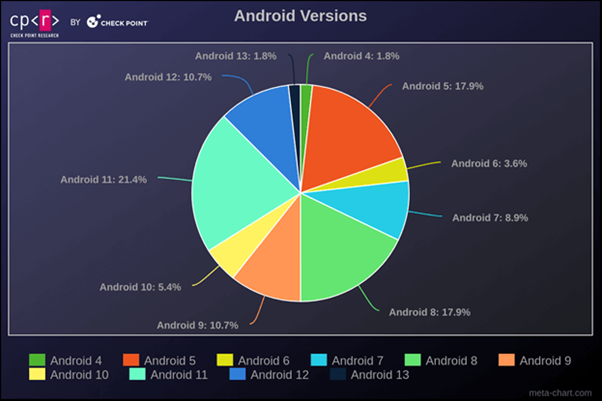
Figure 3 – Android Versions
One thing we constantly observe in Windows bots is the consistently high number of Windows XP infections, despite the fact that this version reached its End of Life in 2014. We observed the same scenario in infected Android devices. More than 87% of the affected victims are running Android versions that are no longer supported and, consequently, not receiving security fixes.
Furthermore, CPR analysed three specific cases in depth. The first was an Android ransomware operation in which the threat actor encrypted the device’s files. The second was leaked Two-Factor Authentication messages (2FA) which could possibly lead to 2FA bypass, and the last case was a threat actor installing Rafel command and control on a hacked government website and infected devices reporting to it.
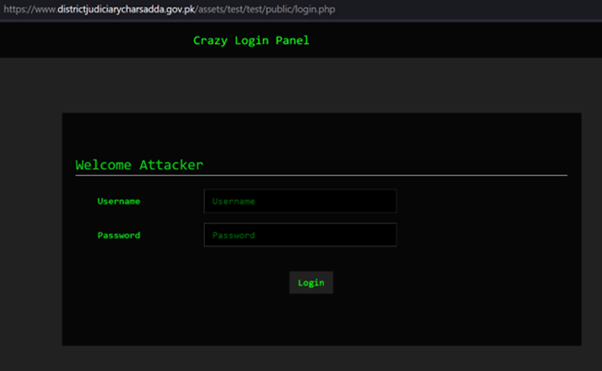
Figure 4 – Rafel RAT is hosted on Pakistan’s government website
Rafel RAT is a potent example of the evolving landscape of Android malware, characterised by its open-source nature, extensive feature set, and widespread utilisation across various illicit activities. The prevalence of Rafel RAT highlights the need for continual vigilance and proactive security measures to safeguard Android devices against malicious exploitation. As cyber criminals continue to leverage techniques and tools such as Rafel RAT to compromise user privacy, steal sensitive data, and perpetrate financial fraud, a multi-layered approach to mobile security is essential.
Steps Android Users Need to take to stay safe:
- Install Apps from Trusted Sources: Only download and install apps from reputable sources like the Google Play Store. Avoid third-party app stores and be cautious with apps that have few downloads or poor reviews. Always check app permissions and reviews before installing.
- Keep Your Software Updated: Regularly update your Android operating system and apps. Updates often include security patches that protect against newly discovered vulnerabilities. Enable automatic updates to ensure you receive the latest protections without delay.
- Use a Reliable Mobile Security App: Install a reputable mobile security app that offers real-time protection against malware. These apps can scan for malicious software, detect suspicious activity, and provide additional security features like anti-theft measures and safe browsing.
By following the steps listed above, Android users can significantly reduce their risk of encountering malware and enhance their device security.




