Tenable Patch Management Now Available, Helps Close Security Exposures
Autonomous Patching Streamlines Discovery to Remediation, with Customisable Controls That Prevent Problematic Updates

Tenable®, the exposure management company, recently announced the release of Tenable Patch Management, an autonomous patch solution built to quickly and effectively close vulnerability exposures in a unified solution. A strategic partnership and integration with Adaptiva, a global leader in autonomous endpoint management, provides the foundation of the solution.
Vulnerability remediation remains a critical challenge as identifying, testing, and installing the countless patches released every day is cumbersome. A recent Tenable report found that only 11% of organisations say they are efficient at vulnerability remediation. The result is that organisations are exposed for long periods of time, as attackers’ average time-to-exploitation has shrunk from 32 days to five.
Tenable Patch Management addresses these issues head on. The integrated solution pairs autonomous patch functionality from Adaptiva with Tenable’s leading vulnerability coverage, built-in prioritisation, threat intelligence and real-time insight to empower organisations to close the loop on vulnerability exposure through automated correlation of vulnerabilities to available patches. With Tenable Patch Management, organisations shorten the time from discovery to remediation by knowing the most impactful vulnerabilities across their environments, exposing priority gaps and taking rapid, decisive action to close critical exposures.
Taking Proactive Action with Tenable Patch Management
Tenable Patch Management mobilises teams to take action against vulnerabilities with full control to determine when, how and where a patch is deployed. Organisations can autonomously patch with confidence, with customisable controls and automatic patch testing that blocks problematic updates from going out.
“Tenable’s approach to patch management keeps security teams in the driver’s seat,” said Shai Morag, Chief Product Officer at Tenable. “Organisations can accurately remediate exposures, streamlining the time from discovery to remediation all while in full control. The combined power of Tenable’s market-leading identification and prioritisation and Adaptiva’s innovative autonomous patch functionality enables enterprises of all sizes to close the gap between security and IT and free up team resources to focus on the threats that matter most to their business.”
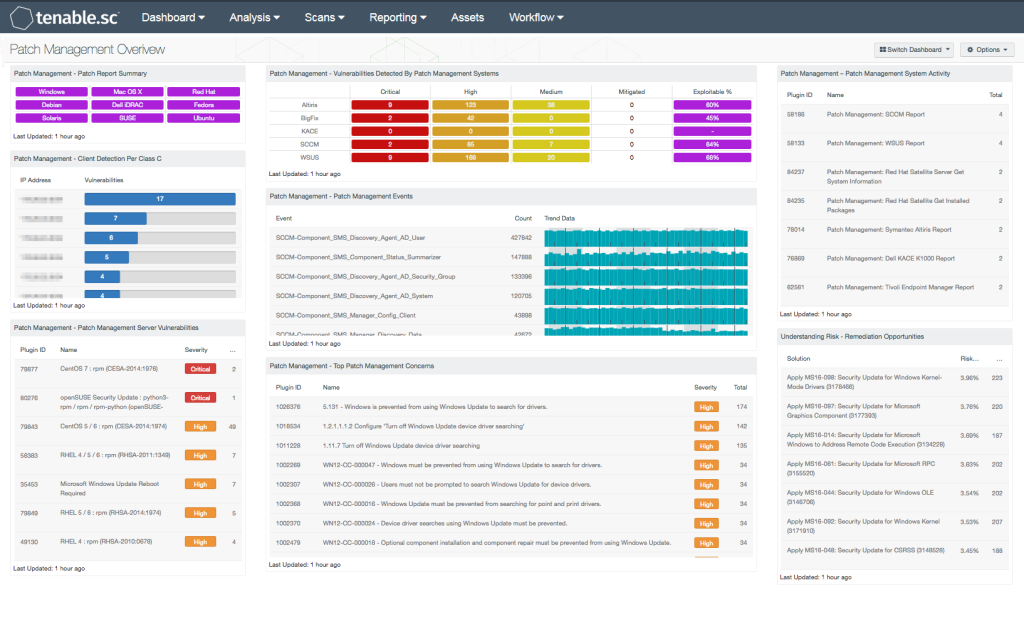
Available as an add on in Tenable One, Tenable Vulnerability Management, Tenable Security Center and Tenable Enclave Security, Tenable Patch Management includes:
- Automated correlation between vulnerabilities and available patches, helping teams overcome the bottleneck that occurs between prioritisation and remediation.
- Automated patching with customisable controls and approval management capabilities, giving IT admins the ability to define and edit specific approval settings and real-time control of deployment actions, including targeted or global pausing, cancelling, rolling back patches and applying precise controls like version management and product exceptions.
- Automatic validation enables teams to easily confirm that a remediation was successful following the subsequent scan.
- Monitor compliance status to align with company policy, while providing leadership with easy-to-use metrics that can be shared with executives.
More information on Tenable Patch Management is available at: https://tenable.com/products/patch-management.