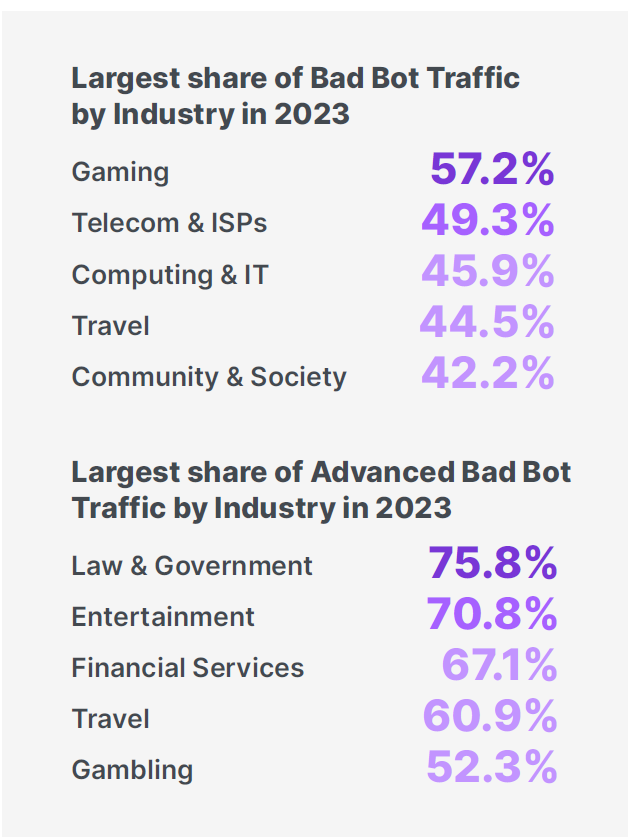
Travel Industry Faces A 45% Surge in Bad Bot Traffic

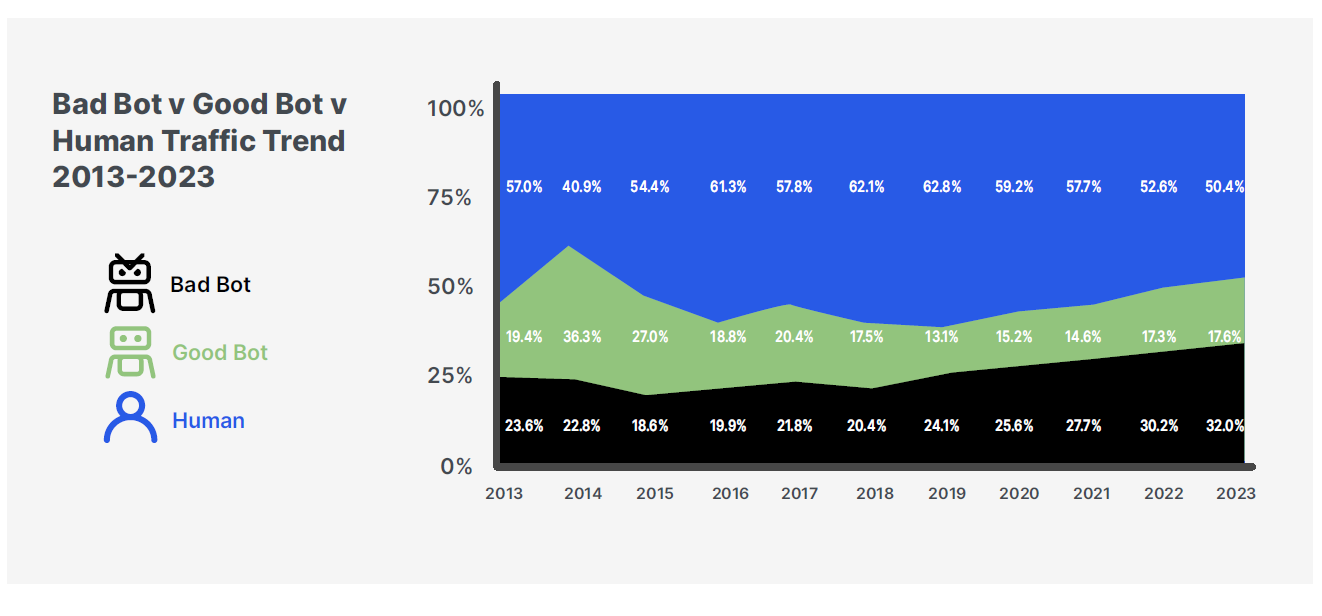
Imperva, a Thales company (@Imperva), the cybersecurity leader that protects critical applications, APIs, and data anywhere at scale, warns that as the travel industry rebounds post-pandemic, it is increasingly targeted by automated threats, with the sector experiencing more than a fifth (21%) of all attack traffic requests monitored last year. The Imperva 2024 Bad Bot Report found that bad bots accounted for 45% of the global industry’s web traffic in 2023 – a significant jump from 37% in 2022.
Travel Industry Saw One of the Highest Surge of Bad Bots
As travel continues to ramp up towards year-end, the industry will likely see a surge in bot activity. These bots target travel companies through seat spinning, unauthorised web scraping, account takeover, and fraud.
Seat spinning is particularly rife in Asia, as bots hold airline seats – often for up to a day – without making payment. This enables operators like unauthorised online travel agencies (OTAs) to resell these seats without risking upfront payment. If these operators fail to offload these seats, airlines can suddenly find seemingly fully booked flights set to depart far below their capacity. The result is significant financial and reputational damage.
In unauthorised web scraping, bots run by OTAs, aggregators and competitors access airlines’ web properties without permission to harvest data. This can damage critical business insights and metrics like look-to-book ratios and even increase the fees airlines must pay their partners. One airline last year ended up paying US$500,000 per month for API requests due to the surge in bad bot traffic scraping its search API.
In terms of account takeovers (ATOs) and fraud, the travel industry experienced the second-highest volume of ATO attempts in 2023, with 11% of all ATO attacks globally targeting the industry. Cybercriminals zero in on the travel sector due to the valuable personal information, stored payment methods, and loyalty points within user accounts. Once the bad actors can access customer accounts, they can steal loyalty points and fraudulently “buy” flights or hotel rooms for onward sale.
Imperva recommends that travel companies deploy a multi-layered defence strategy to mitigate these threats across all digital touchpoints, including APIs and mobile applications. Organisations must identify risks through advanced traffic analysis and real-time bot detection. Understanding exposure, particularly around login functionalities, is crucial as these are prime targets for credential stuffing and brute force attacks.
“Quick wins for security teams would include blocking outdated browser versions, restricting access from bulk IP data centres, and implementing detection strategies for signs of automation, like unusually fast interactions,” said Daniel Toh, Chief Solutions Architect, Asia Pacific and Japan, Imperva. “Analysing suspicious traffic sources – like single IP addresses – can provide valuable insights, as can regularly watching for traffic anomalies like high bounce rates and sudden spikes.”
“Lastly, monitor the news and stay abreast of new data breaches which threat actors can use to fuel automated account takeover attacks.”




