Cisco – The Five Pillars of Cybersecurity in a Hybrid World
With the rise of hybrid working models, cybersecurity has become more complex and challenging. Cybercriminals are exploiting the security gaps created by the sudden shift to remote work. From phishing scams and malware to social engineering and insider threats, organisations must be prepared to defend themselves against a wide range of cyber risks.

Leading technology company, Cisco, has introduced the five pillars of cybersecurity in a hybrid world, revealed by Tay Bee Kheng, ASEAN President of Cisco, and Koo Juan Huat, ASEAN Cybersecurity Lead for Cisco, during a recent media briefing.
According to Tay, the shift to a hybrid working environment has certainly presented companies with new challenges in cybersecurity. “As companies adopt new ways of working, it’s important to ensure that their cybersecurity strategies are updated to reflect these changes,” said Tay. “The five pillars of cybersecurity provide a framework that companies can use to strengthen their defences against cyber threats.”
The five pillars of cybersecurity in a hybrid world, as outlined by ASEAN Cisco, are identity verification, devices, networks, applications, and data. Koo explained that the entire infrastructure needs to work together as a platform for effective cybersecurity. “Visibility, automation, orchestration, and governance are essential to ensure that the infrastructure is secure,” said Koo.
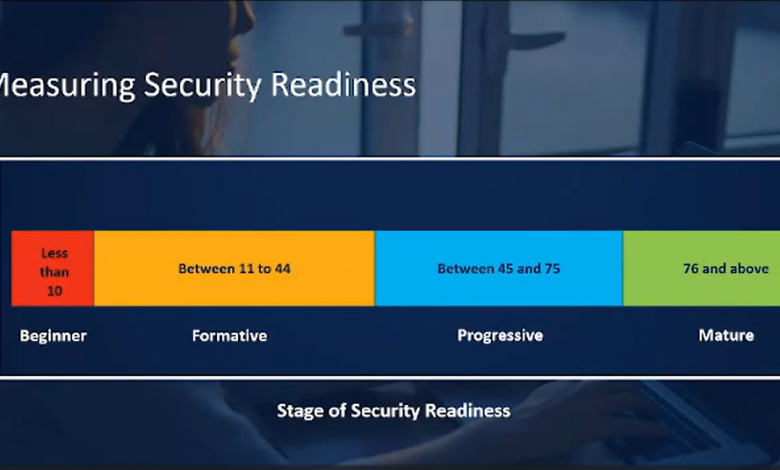
Cisco has also determined, in order of significance across all five pillars, the capabilities that businesses should have in order to establish an optimal cybersecurity posture. The organisations were then categorised as either “beginner,” “formative,” “progressive,” or “mature” based on their level of development. Just 27% of the 6,700 cybersecurity leaders polled are at the mature level, which indicates they are well along in the deployment process and ready to take on security challenges.
The impact of industry on the cybersecurity readiness measure was also discussed during the meeting. “Different industries have different cybersecurity needs,” said Tay. “It’s important for companies to understand their specific risks and develop cybersecurity strategies that are tailored to their industry.”

Koo highlighted the importance of identity verification in the zero-trust model of cybersecurity. “80% of web application breaches happen due to stolen credentials,” he said. “Identity verification is critical to ensure that only authorised users can access sensitive data.”
In this new era of work, cybersecurity has become critical to the survival of businesses. Cybercriminals are becoming more sophisticated, and the risks associated with hybrid work environments are increasing. However, by leveraging the framework of the five pillars of cybersecurity, companies can develop a comprehensive security strategy that protects against cyber threats and safeguards their business operations.
With the right capabilities and strategies in place, businesses can achieve an ideal cybersecurity posture and defend themselves against the constantly evolving landscape of cyber risks.




