Microsoft Revokes Malicious Drivers in Patch Tuesday Culling

Authored by: Andrew Brandt, Principal Researcher, SophosLabs
 In December 2022, Microsoft published their monthly Windows Update packages that included an advisory about malicious drivers, signed by Microsoft and other code-signing authorities, that Sophos X-Ops (and others) observed threat actors abusing during attacks. Today, Microsoft issued Security Advisory ADV230001 as part of their July Windows Update that addresses Sophos’ discovery of more than 100 malicious drivers that had been digitally signed by Microsoft and others, dating as far back as April 2021.
In December 2022, Microsoft published their monthly Windows Update packages that included an advisory about malicious drivers, signed by Microsoft and other code-signing authorities, that Sophos X-Ops (and others) observed threat actors abusing during attacks. Today, Microsoft issued Security Advisory ADV230001 as part of their July Windows Update that addresses Sophos’ discovery of more than 100 malicious drivers that had been digitally signed by Microsoft and others, dating as far back as April 2021.
They also released Knowledge Base article 5029033, which includes new, more detailed information on the technical measures Microsoft has taken to protect against these malicious signed drivers. Sophos has had protection measures in place since 2022 that could detect the presence of, and block the installation of, these drivers.
As part of the security model for the most recent generations of 64-bit Windows, Microsoft instituted a policy in 2016 (beginning with Windows 10, version 1607), that kernel drivers must carry a valid digital signature before a Windows operating system with Secure Boot enabled will load them.
This is important because the nature of third-party drivers is that they function almost as operating system components, at a very low level. Depending on how they are created and installed, drivers can load before other parts of an operating system (including endpoint security software) can start.
In our December story about malicious signed drivers, that’s exactly what we discovered attackers were doing – they would use their previously-obtained Administrator privileges to set up the drivers to load during the boot process, before security software was running, and once they were loaded, the drivers would sabotage various types of security (and other) applications, preventing them from running as designed. Sophos endpoint products were among the security tools that were targeted.
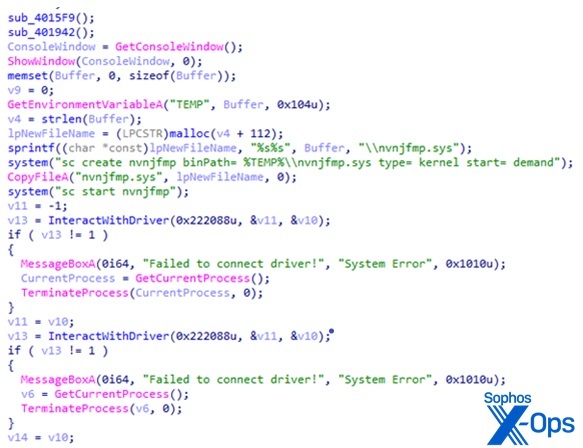 Scripting used to load a malicious EDR-killer driver and set up persistence
Scripting used to load a malicious EDR-killer driver and set up persistence
In some cases, the drivers disclosed (and functionally neutered) last December had been signed using code-signing certificates that had been issued to software publishers, stolen, and then leaked to the internet. In others, they were mysteriously, validly signed using the Microsoft Windows Hardware Compatibility Publisher (WHCP) certificate.
Microsoft only signs code using the WHCP certificate when a software or hardware vendor who previously registered for Microsoft’s Windows Hardware Dev Centre program, and is in possession of an Extended Validation code signing certificate, submits the driver to the company for signing.
(If someone has physical access to a Windows machine and can reboot it into the Windows bootloader, it’s possible for them to turn off this feature on a case-by-case basis using the Disable Driver Signature Enforcement option before Windows boots. The attackers, in the cases we investigated, did not have physical access to the machines.)
Breaking the trust chain
Microsoft invalidated the drivers we reported to them last year, rendering them unable to load. On the same day as the announcement, in close coordination with Microsoft, Sophos published updated endpoint protection signatures that would detect and remove any such driver found on a computer.
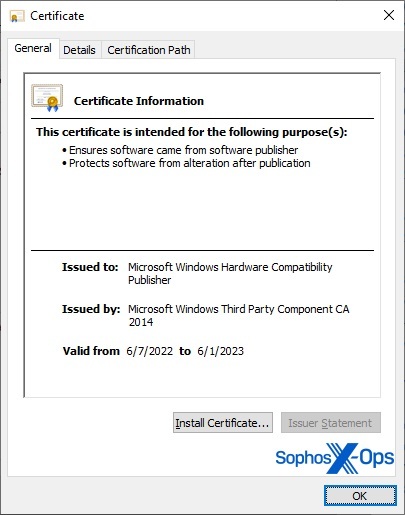 The WHCP certificate was used to sign drivers dating back as far as early 2022
The WHCP certificate was used to sign drivers dating back as far as early 2022
The digital signatures embedded in the driver files revealed that the problem was far larger than either Sophos or Microsoft had anticipated. In the weeks that followed, Sophos discovered 133 malicious drivers, 100 of which had been signed by Microsoft’s WHCP certificate.
Among the certificate owners of the non-WHCP signed drivers, the certificate details reveal they had been issued to companies whose names indicate they are based in China. These certificates were owned by the following company names:
- Beijing Kate Zhanhong Technology Co.,Ltd.
- Zhuhai liancheng Technology Co., Ltd.
- Beijing JoinHope Image Technology Ltd.
- 海南巨灵网络科技有限公司 (Hainan Giant Spirit Network Technology Co., Ltd.)
- Shenzhen Luyoudashi Technology Co., Ltd.
- Chengdu Lule Cube
- Bopsoft
It is also notable that we encountered a small number of unsigned, malicious drivers that were functionally identical to the signed drivers. SophosLabs analysts hypothesized that these unsigned drivers may have been the versions later submitted into the code-signing mechanisms like WHCP.
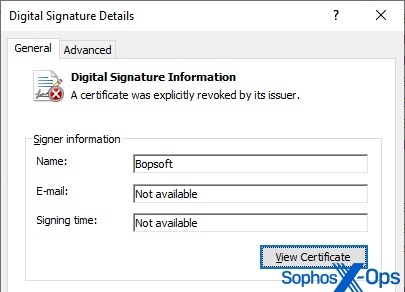
Some of the driver signing certificates from other companies have been revoked
Many of the signed drivers were also packed using runtime packer software. Packer utilities are used by both legitimate software publishers and malware creators to obfuscate and conceal the functions inside an executable (drivers are a form of a Windows Portable Executable, or PE). However, most legitimate drivers are not packed. Some of the drivers were packed using VMProtect, a commercial runtime packer.
Upon closer scrutiny, our analysts discovered interesting details that revealed hints about how the person or people behind the scheme to get the malicious drivers signed operated. Based on our analyses of the signed drivers and their underlying binaries, it appears the creator of the malicious driver built out one “parent” version of the driver, then ran the parent version through one or more packer utilities one or more times, creating in some cases dozens of “child” variants, all of which the creators could submit to Microsoft for signing.
What the drivers are capable of
Sophos discovered that the drivers fell into one of two general categories: They were either “Endpoint protection killers” functionally similar to the drivers discovered last year, or they were a form of rootkit, meant to quietly run in the background on an infected computer. As we previously mentioned, these drivers could only be installed by someone who had administrative privileges on the system.
Among the “endpoint protection killer” drivers, 68 had been signed by Microsoft, and 13 were signed by certificates belonging to other companies.
Among the rootkit drivers, 32 of them had been signed by Microsoft, 4 were signed by other companies, and 16 were unsigned variations of one of the four signed drivers.
While some of the signing certificates are now expired, many more remained valid until the Patch Tuesday release
The majority of the rootkit drivers had the capability to monitor network traffic using the Windows Filtering Platform (WFP), which would have given them the ability to observe sensitive data sent over or received from the internet.
Several of the rootkits appear to be variants of known Windows rootkit families, such as the FU rootkit, the Fivesys rootkit, the FK_undead rootkit, or the Netfilter rootkit. Some of these rootkits have the capability to disable the Windows User Account Controls (UAC) features, which permit the operator of the rootkit to elevate the privileges of other applications to an Administrator level without a UAC prompt appearing on the screen.
Many of the rootkits also have the capability to communicate with a command-and-control server whose address is based on a Domain Generating Algorithm (DGA), and which changes over time. These rootkits communicated with DGA domain names that used the .xyz top-level domain (TLD).
Detection and guidance
Drivers with capabilities similar to those found in the course of this investigation will be detected with any or all of the following signatures: Mal/Rootkit-BE, Troj/Rootkit-VE, Troj/Agent-BJJB, Mal/Rootkit-VF, Troj/Rootkit-ND, Troj/Rootkit-NH, Troj/Rootkit-NO, Troj/Rootkit-NP, or Troj/Rootkit-NS.
Driver files reported by Sophos to Microsoft will be, as of the July 11, 2023, patch release, invalidated and their signatures revoked by Microsoft’s update mechanism, and will no longer run. Microsoft may also invalidate other drivers whose provenance matches the source of the known-malicious drivers at any point in the future.