Cyber Predators Target Vulnerable Victims: Hackers Blackmail Hospitals, Trade Patient Data and Find Partners Through Darknet Ads

In a world of crime, expect no mercy. Cybercrime goes hard after its goal, which is most often financial gain. Hackers choose their victims accordingly, where they are most likely to succeed and where the most valuable data is located. It is therefore not surprising that the third most common target of cyberattacks is healthcare.
According to data from Check Point Research (CPR), the Threat Intelligence arm of Check Point® Software Technologies Ltd. (NASDAQ: CHKP) a leading AI-powered, cloud-delivered cyber security platform provider, from January – September 2024, the global weekly average number of attacks per organisation within the healthcare industry was 2,018, representing a 32% increase, compared to the same period last year.
Around the world, healthcare organisations continue to face a worrying increase in cyberattacks since the beginning of this year. Between January – September this year, the APAC region was leading in attack volume, averaging 4,556 weekly attacks per organisation, a 54% increase. The rapid digital transformation in APAC’s healthcare systems, driven by expanding access to digital health records and telemedicine, has increased vulnerabilities, fuelled by the lack of robust cyber security infrastructure required to protect against advanced threats, thus making them attractive targets for cybercriminals.
Latin America, with a weekly average of 2,703 attacks per organisation, a 34% increase, experienced such attacks possibly due to weaker regulations and underfunded cyber security initiatives in the healthcare sector, creating easy entry points for attackers. Europe, despite experiencing a lower number of weekly attacks (1,686), saw the largest percentage increase (56%), indicating a heavier reliance on digital tools without parallel investments in their security posture, making them prime targets for ransomware and data theft. Meanwhile, North America’s healthcare sector, which averaged 1,607 weekly attacks with a 20% increase, remains a lucrative target due to its wealth of sensitive patient data and established digital infrastructure.
Hospitals and other healthcare institutions cannot afford service outages or disruptions, because it could directly endanger the lives of patients. Conversely as mentioned, sensitive patient data is a very hot commodity when traded on the dark net and can also serve as leverage in corporate extortion. And the biggest threat nowadays, which has already paralysed countless hospitals around the world, is ransomware.
The World Health Organisation (WHO) has therefore declared 17 September World Patient Safety Day to highlight the potential risks. Patient safety is not only a matter of physical care but patients’ health and lives may also be at risk in the event of a cyberattack. The problem is even bigger because many cybercriminals are working together. Some offer access to organisations they have previously breached, and others offer to rent their infrastructure for a fee. The dark net is full of advertisements offering ransomware-as-a-service (RaaS), so that even amateur cyber criminals who would otherwise not have the technical knowledge and experience for similarly serious attacks can threaten hospitals and other healthcare institutions.
A real-life example where a hacker with the nickname Cicada3301 posted an advertisement on a closed Russian-language underground forum announcing a new team offering ransomware as a service. He only asks for a commission of 20% on successful attacks. This is an illustration of how RaaS cybercriminals recruit their partners and what the standard revenue distribution is. The interesting thing is that some forums have an arbitration and dispute resolution mechanism in cases where both parties disagree on payment or services delivered. This is essential as all communicating parties are criminals who communicate in an anonymous environment. As you can see, cybercrime works according to similar rules as regular business.
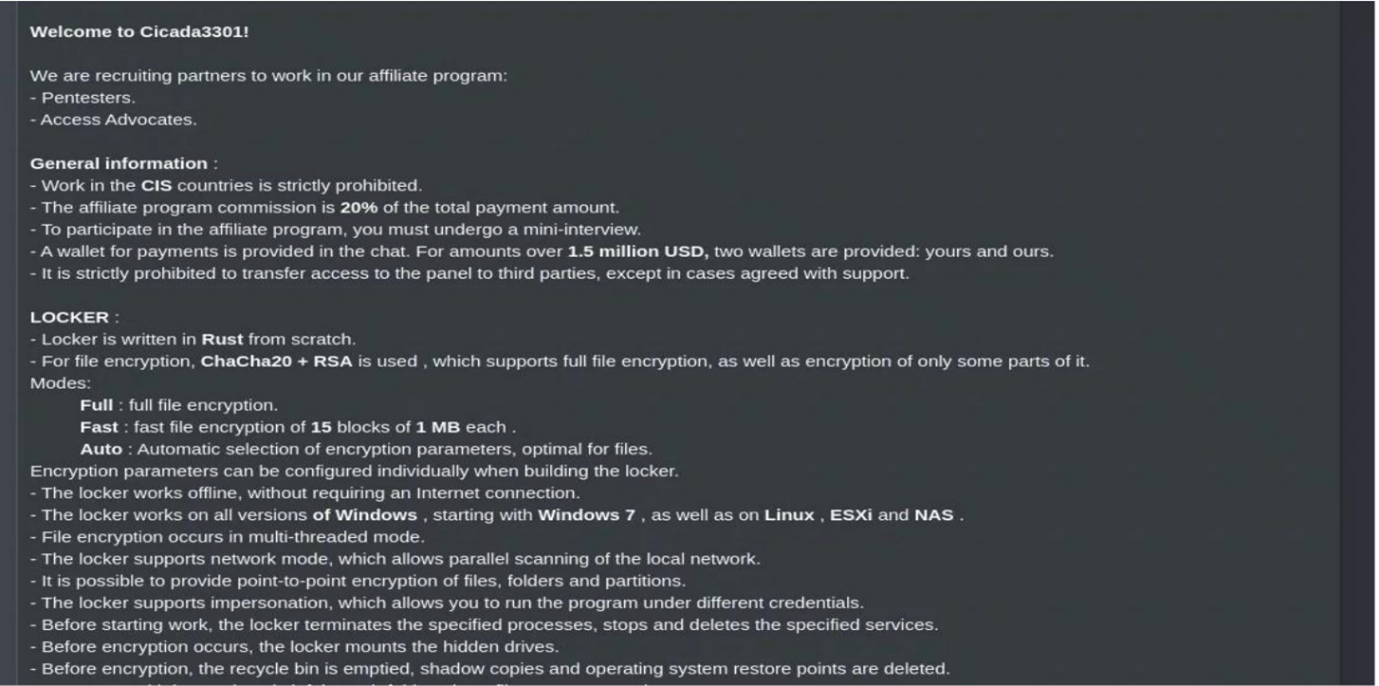
Hacker Cicada3301 also posted information on a special extortion site about several victims, including the Italian medical organisation ASST Rhodense. The hospital had to cancel and reschedule operations as a result of the attack. And unfortunately, this is not an isolated case.
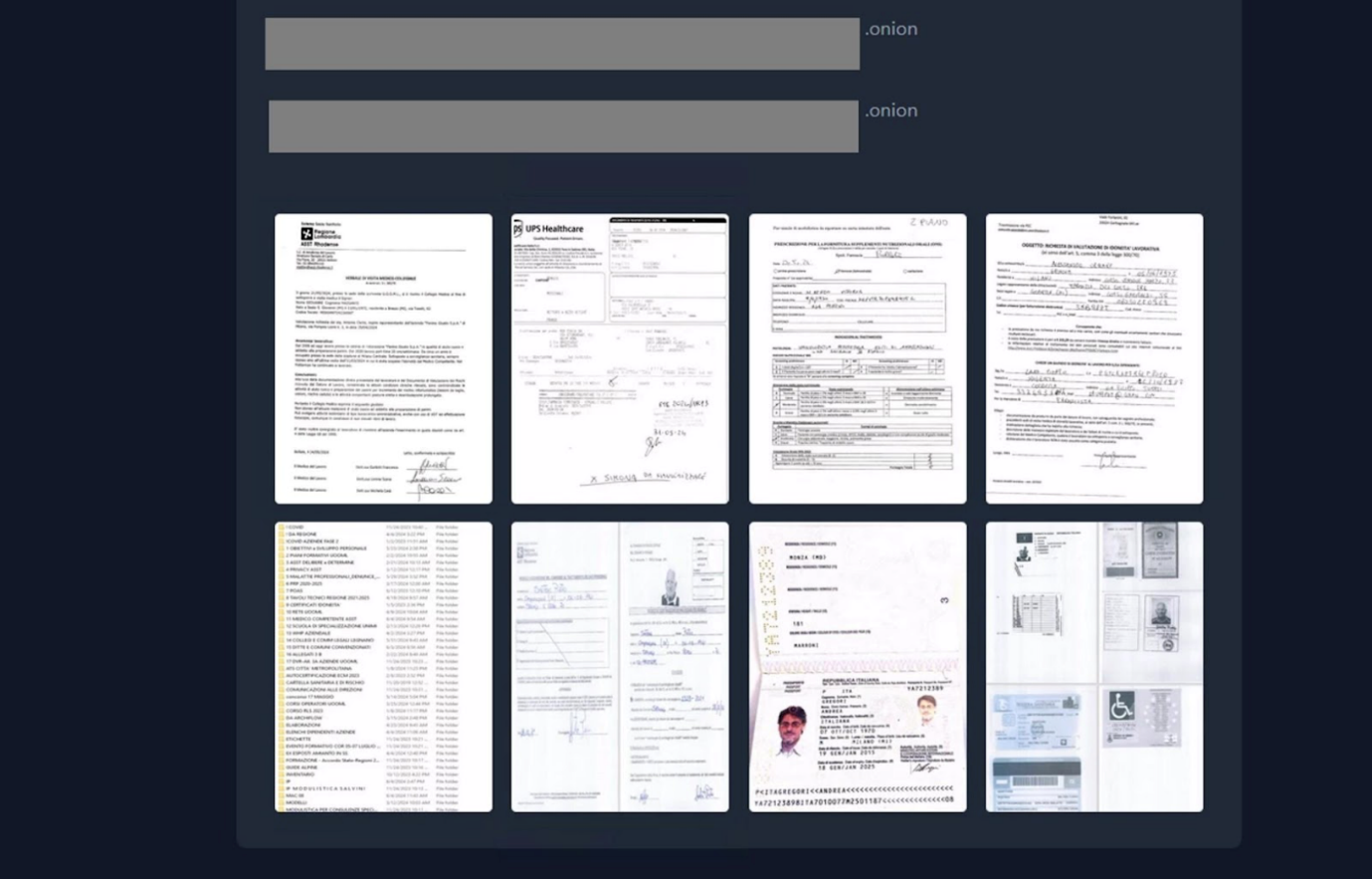
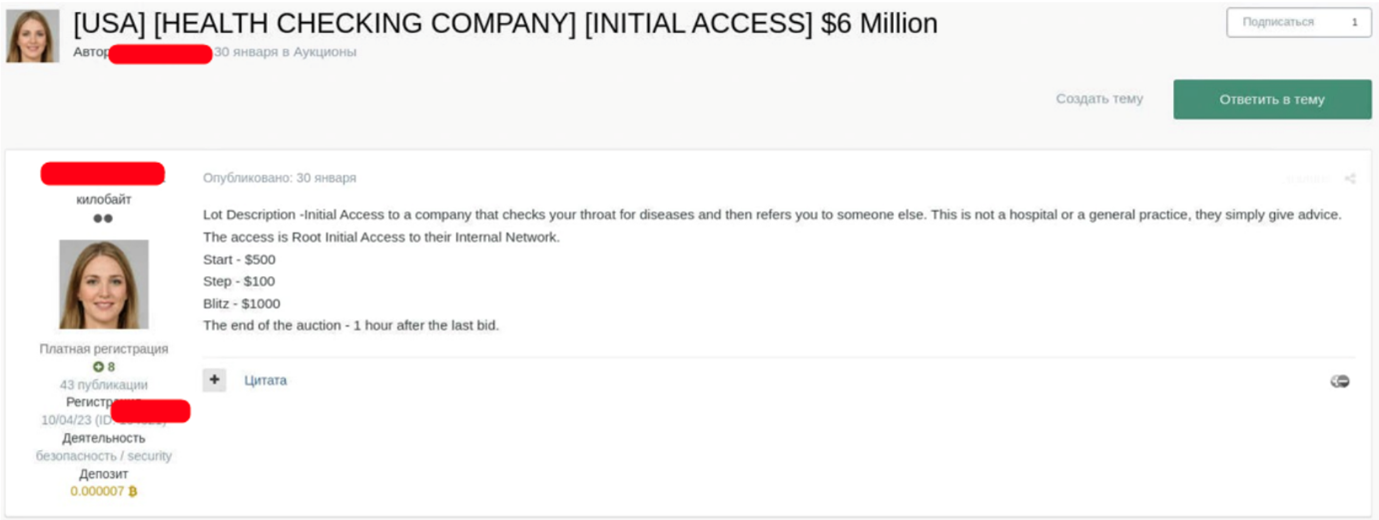
Hospitals and patients are frequently targeted by well-coordinated ransomware attacks. Ransomware groups provide encryption tools and infrastructure to collaborators, and stolen sensitive data is often posted online to pressure victims into paying. This tactic leverages the fear of hefty fines for privacy violations and the risk to patient safety or hospital operations. Additionally, hackers sell access to hospital systems on underground forums. Some act as intermediaries, purchasing initial access to assess the quality for permission abuse, mapping networks, and then selling this access to others. For example, an alleged Russian-speaking cybercriminal active in underground forums since January 2024 has been selling access to Brazilian hospitals, offering it for $250, targeting institutions with revenues of $55 million, and then launching another round of attacks.
Overall, the cost of many cyber tools, data and access, and infrastructure is relatively low, yet a successful attack can cause enormous damage and put patients’ health at risk with ransoms running into the millions and sometimes tens of millions of dollars.
“In most cases, cybercriminals refrain from indicating to their partners who to attack. Only attacks on the Commonwealth of Independent States are usually taboo but with no other restrictions. We can speculate that its due to hackers’ preference not to attack the countries in which they operate. In the early days, some RaaS groups claimed they would not attack healthcare-related organisations which was later modified to attacks should not include data encryption to avoid interruption of services, but data theft and extortion are permissible. In reality, none of these rules are followed anyway,” says Sergey Shykevich, Threat Intelligence Group Manager, Check Point Research. “An analysis of victims publicly extorted on ransomware groups’ websites showed that nearly 10% of victims in the last year are from the healthcare industry.”
The differences between the groups are mostly subtle. But there are exceptions. ALPHV/BlackCat has publicly encouraged its partners to focus specifically on hospitals and healthcare. This was supposed to be revenge for the police operation against group’s infrastructure. As a result, the victim ratio from the health sector reached more than 15% in the last 12 months.
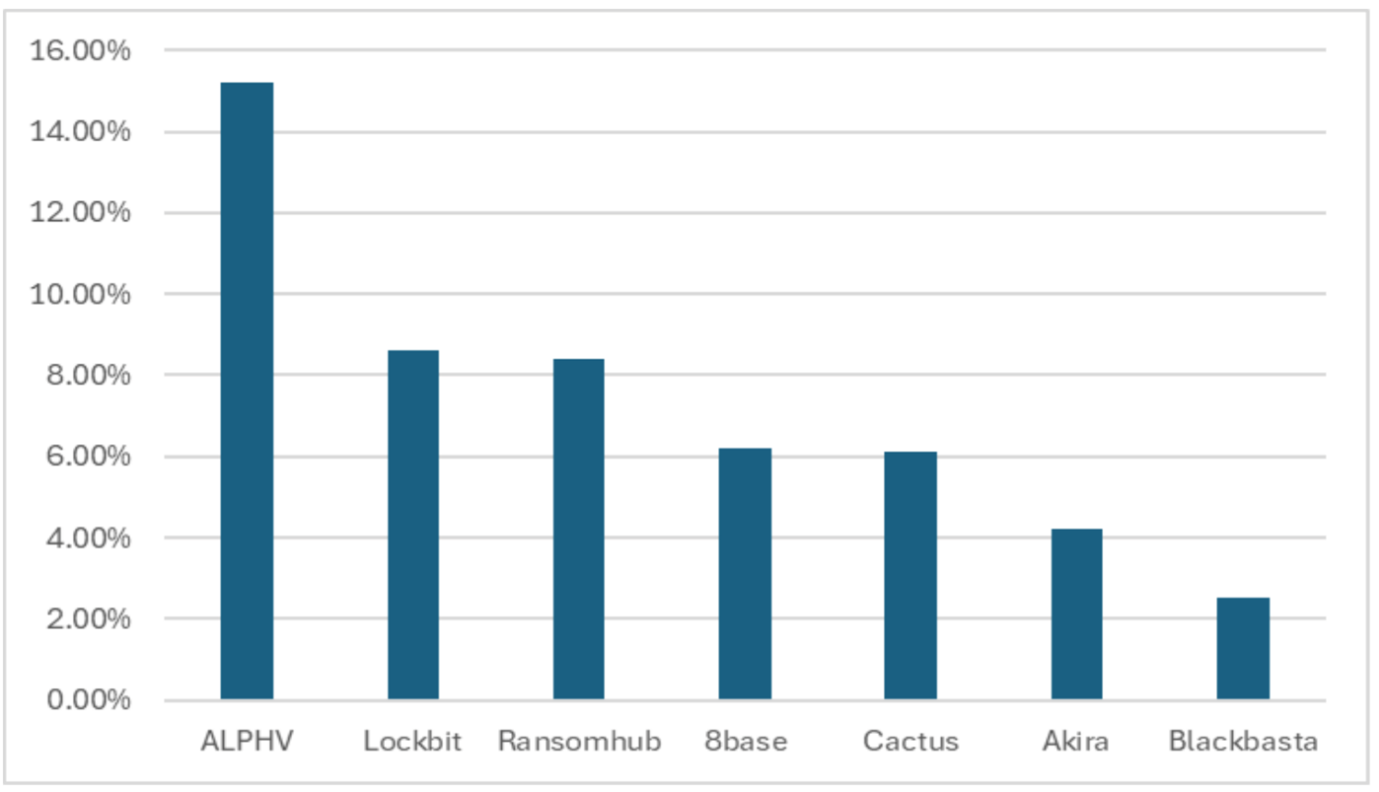
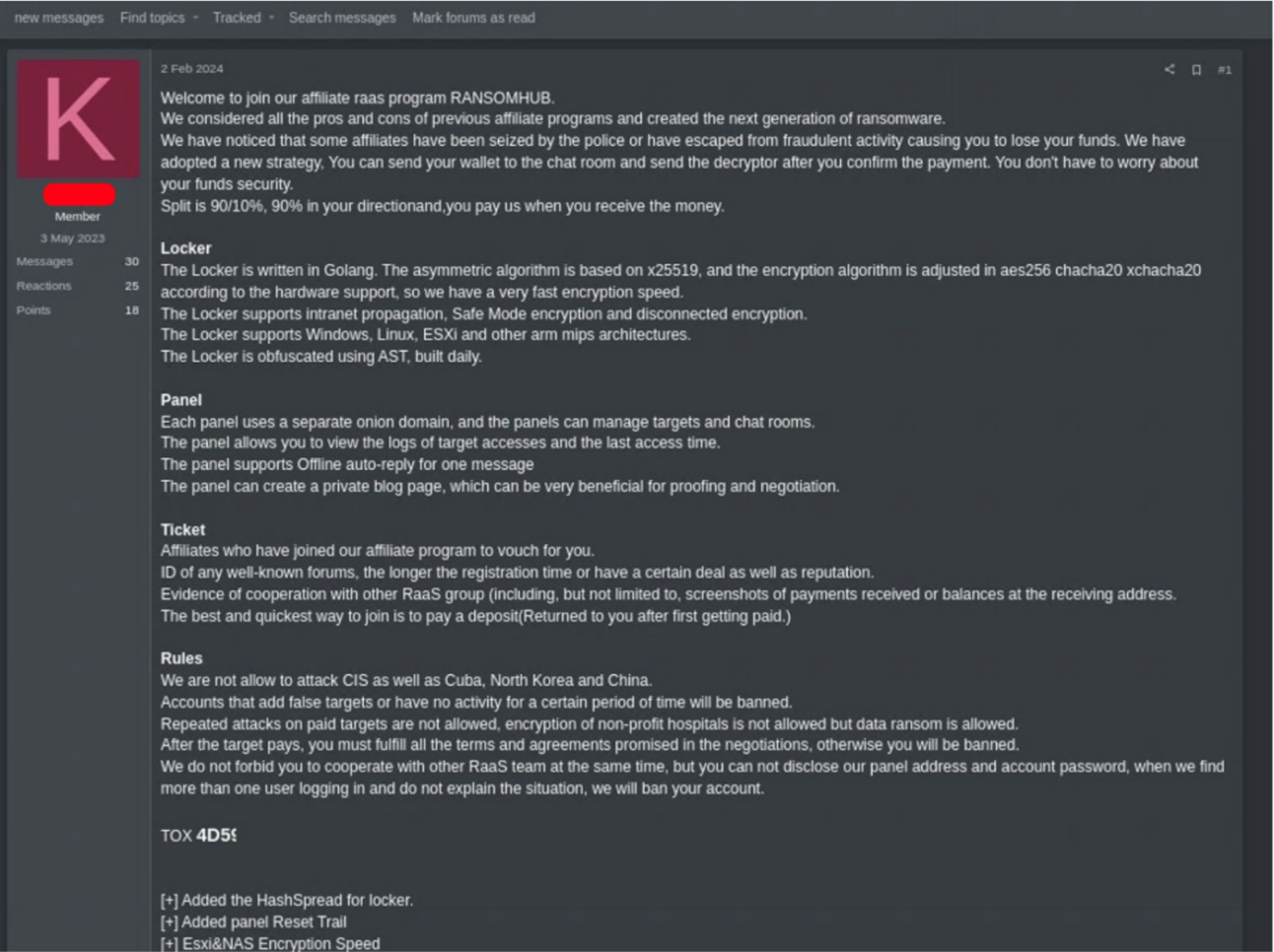
RansomHub, the most active ransomware group in July and August, posted an advertisement on a dark net forum and promised, that 90% of the ransom revenue could be kept by the partners, with only 10% to be paid to the group for providing the infrastructure. In return, partners would receive sophisticated attack management tools and other benefits. The advertisement mimicked traditional companies offering their services and demonstrating their competitive advantages. This again shows that cybercrime is a pure business, with many hacker organisations no different, structurally from other tech companies.
The Importance of Cyber Security In Healthcare
“In some cases, we’re seeing that if one attack occurs, another can follow relatively soon. Cybercriminals are counting on the fact that perhaps there will be a failure to recover properly, that there is still some chaos or that there will be an underestimation because hospitals won’t expect to be targeted repeatedly,” adds Sergey Shykevich. “In short, healthcare organisations face a huge risk and patients are often held hostage. So, it’s not just on World Patient Safety Day that we should remind ourselves that prevention is also essential in protecting against computer viruses, cyber infections, threats and attacks. Ensuring patient safety in the digital age simply requires not only technological solutions but also a culture of safety and continuous threat awareness.”
Security Tips for Healthcare Organisations
To ensure cyber security in healthcare, it is essential to take comprehensive measures including technology solutions, staff training and improved security policies. Key steps include:
- Beware of Trojans – Ransomware attacks usually do not start with ransomware directly, but use Trojans for initial access. Trojan infection occurs days or weeks before the ransomware attack.
- Be alert on weekends and holidays – Most ransomware attacks during these times when IT teams may be off-duty, slowing response times.
- Use anti-ransomware – To prevent sophisticated ransomware attacks, an anti-ransomware solution can detect unusual activity or suspicious behaviour, or repair any damage and return everything to normal in minutes, preventing massive damage.
- Back-up data – Consistent backups ensure a quick data recovery, without paying a ransom, making consistent backups necessary, including automatic backups on employee devices.
- Segment and limit access to only necessary information – Restrict user access to necessary data only and segment networks to prevent an attack from spreading. Whilst dealing with post-attack aftermath can be difficult, repairing a network-wide attack aftermath is much more challenging.
- Education is an essential part of protection – Train staff to recognise phishing and other cyber threats to avoid falling victim to social engineering.
- Regularly install updates and patches – WannaCry hit organisations around the world hard in May 2017, infecting over 200,000 computers in three days. Yet a patch for the exploited EternalBlue vulnerability was available a month before the attack. Regularly update software and systems to prevent vulnerabilities from being exploited, or use an Intrusion Prevention System (IPS) with virtual patching capabilities if updates are not possible.
- Ensure strong and non-default passwords, especially on internet-facing servers are in place – Default passwords are easy targets for attackers, so updating them with complex, hard-to-guess combinations and MFA can significantly reduce the risk of unauthorised access and add an extra layer of protection.
- Legal and Regulatory Framework – Compliance with national and international privacy standards and regulations is essential to ensure patient safety.
- Secure everything and settle for the best – Protect all devices, from computers, servers, mobile devices, as well as smart light bulbs or any other IoT or IoMT device, and use the best security solutions and, if necessary, with external teams specialised in detecting and hunting threats.