Cyberespionage Attacks by the China-Aligned FamousSparrow Group in the United States, ESET Research Discovers
ESET uncovers cyberespionage activity by China-aligned group FamousSparrow, targeting financial, research and government institutions across the Americas.
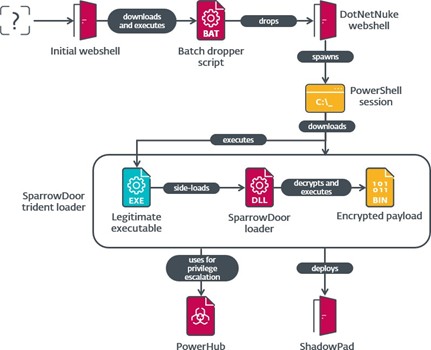
ESET Research investigated suspicious activity on the network of a trade group in the United States that operates in the financial sector. While helping the affected entity remediate the compromise, ESET made an unexpected discovery in the victim’s system: malicious tools belonging to FamousSparrow, a China-aligned APT group. The group was thought to be inactive, as there had been no publicly documented activity by FamousSparrow since 2022. The ESET investigation shows that FamousSparrow was not only still active during this period, but that it must have also been developing its toolset, since the compromised network revealed not one, but two previously undocumented versions of SparrowDoor, FamousSparrow’s flagship backdoor.
ESET Research uncovered additional activity by the group during the 2022-2024 period, including the targeting of a governmental institution in Honduras. Furthermore, ESET discovered that, as part of this campaign, the threat actor managed to breach a research institute in Mexico just a couple of days prior to the compromise in the U.S. — both of which were compromised in late June 2024. Both of these versions of SparrowDoor constitute marked progress over earlier iterations, especially in terms of code quality and architecture, and one implements parallelization of commands.
“While these new versions exhibit significant upgrades, they can still be traced back directly to earlier, publicly documented versions. The loaders used in these attacks also present substantial code overlaps with samples previously attributed to FamousSparrow,” says ESET researcher Alexandre Côté Cyr, who made the discovery.
In order to gain initial access to the affected network, FamousSparrow deployed a webshell on an IIS server. While ESET was unable to determine the exact exploit used to deploy the webshells, both victims were running outdated versions of Windows Server and Microsoft Exchange, for which there are several publicly available exploits.
As for the toolset used in the campaign, the threat actor employed a mix of custom tools and malware along with those shared by China-aligned APT groups, as well as from publicly available sources. The final
payloads were backdoors SparrowDoor and ShadowPad. Among them were plugins capable of running commands, file system operations, keylogging, transferring files, listing and killing processes, monitoring file system changes, and taking screenshots.
In September 2024, the Wall Street Journal published an article reporting that internet service providers in the United States had been compromised by a threat actor named Salt Typhoon. The article relays claims by Microsoft that this threat actor is the same as FamousSparrow and GhostEmperor.
“It was the first public report that conflates the latter two groups. However, we see GhostEmperor and FamousSparrow as two distinct groups. There are few overlaps between the two but many discrepancies. Based on our data and analysis of the publicly available reports, FamousSparrow appears to be its own distinct cluster with loose links to the others,” explains Côté Cyr.
FamousSparrow is a cyberespionage group that has been active since at least 2019. ESET Research first publicly documented the group in a 2021 blogpost when it observed it exploiting the ProxyLogon vulnerability. The group was initially known for targeting hotels around the world but has also targeted governments, international organizations, engineering companies, and law firms. FamousSparrow is the only known user of the SparrowDoor backdoor.
For a more detailed analysis and technical breakdown of the FamousSparrow toolset, check out the ESET Research blogpost “You will always remember this as the day you finally caught FamousSparrow” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X), BlueSky, and Mastodon for the latest news from ESET Research.