Identity Access Management Is a Cornerstone of Good Cybersecurity

Keep your friends close and your enemies closer.
This is especially true in the cutthroat world of business in the digital age, where everyone and everything can be a threat to the organisation’s IT infrastructure.
Actually, key decision-makers will have to keep their enemies close and their friends closer. This is because the biggest enemy might actually be a “friend”—or someone within the company already.
Complicating things is the continuing rise of remote work, which has given cybercriminals a wider attack surface. With a widely distributed workforce, there are more backdoors to breach an organisation’s network and do all kinds of damage.
This is why identity access management is fast becoming a necessity in this modern age of business.
What Is Identity Access Management?
Identity access management, or simply IAM, is essentially a framework of policies and technologies put in place to ensure that the right people have the right access to the right resources at the right time. It is a cybersecurity paradigm that necessitates the use of various technologies, including authentication mechanisms (passwords and biometric data), and authorisation mechanisms (role-based access control).
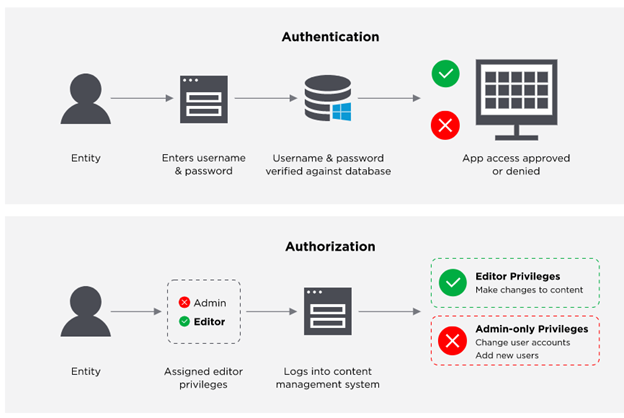
Fig. 1. Graphical representations showing how IAM works

An IAM system is critical in ensuring that sensitive data and resources are protected from unauthorised access or misuse. It is also vital in ensuring compliance with regulatory requirements. Not for nothing then that Bugcrowd CISO Nick McKenzie describes IAM as “a cornerstone of security.”
“[IAM] plays a major part in the current distributed workplaces ecosystem. With the increase of remote working, the requirement for SaaS (Software-as-a-Service) applications, VPNs (virtual private networks) and access to data-sharing applications has increased significantly,” McKenzie explains. “This implies that management of these various applications needs to be completed in a central and automated fashion. Using something like an Identity Provider (IdP) is generally a great start.”

David Hope, Senior Vice President, Asia Pacific & Japan, at ForgeRock, views IAM similarly, calling it “a mission-critical component in an organisation’s approach to cybersecurity.”
“Everyone and everything that connects to the Internet has an identity that must be confirmed and permissions that have to be assessed before any access is granted to any resource,” says Hope. “The job of verifying these identities, which can be in the millions, is best handled by a comprehensive IAM platform that is both fast and scalable to make smart access decisions even during traffic surges.”
Sherif El-Nabawi, Vice President, Sales Engineering, Asia Pacific and Japan, at Crowdstrike, concurs. He adds that “organisations must ensure they are providing the right level of access to all users in a seamless and efficient way” to ensure that their infrastructure and assets, including data, are safe, secure and fully compliant with regulations.
Why Is IAM Critical Today?
Holistic, multilayered security has become indispensable in a digital landscape full of malicious actors and sophisticated, continuously evolving threats. One of these layers, again, is IAM.

“Employees may be accessing sensitive information from a variety of locations and devices. This creates new opportunities for attackers to gain unauthorised access to systems and data, and puts sensitive information at risk,” explains Edwardcher Monreal, Principal Solutions Architect, IAM Consumer Authentication Solutions, at HID. “IAM can help organisations address these risks by providing centralised control over access to resources, ensuring that only authorised users can access sensitive information. This can help prevent data breaches and other security incidents.”
Preventing breaches and security incidents is the ultimate end goal of IAM—and the lack of it exposes an organisation needlessly. In fact, according to the CrowdStrike Overwatch™ threat hunting team, 80% of breaches are identity-driven. The reason is that attackers generally bypass the traditional cyber kill chain by directly attacking compromised credentials. In doing so, they can move laterally within a network at a much faster rate and launch more catastrophic attacks.
Corroborating CrowdStrike’s findings on the prevalence of identity-based attacks is a recent report from Identity Defined Security Alliance (IDSA). The ISDA report states that 84% of organisations experienced an identity-related breach in 2021, with 78% suffering direct business impact.
Compromising the Bottom Line and More
That impact can come in various forms, but the most crippling is generally the massive costs of an attack. For instance, data from Egnyte pegs the global cost of a data breach at over USD $4 million. Closer to home, a data breach in Southeast Asia costs a business about USD $2.62 million with close to 22,500 records breached on average. These are lower than the global average of about USD $3.92 million on 25,575 compromised records, but they are nonetheless significant. The bottom line is that a breach alone can be costly, and it is getting costlier. In fact, Egnyte estimates that the cost of a data breach is increasing by roughly 10% each year, making security even more critical.
That is not to mention the other ramifications of a cyber attack—regulatory fines, reputational damage, prolonged disruptions of work, intense scrutiny from the media and authorities, and reduced staff morale, to name a few. Exacerbating matters is that every business is a target, and the likelihood of an attack is greater now more than ever. Consider:
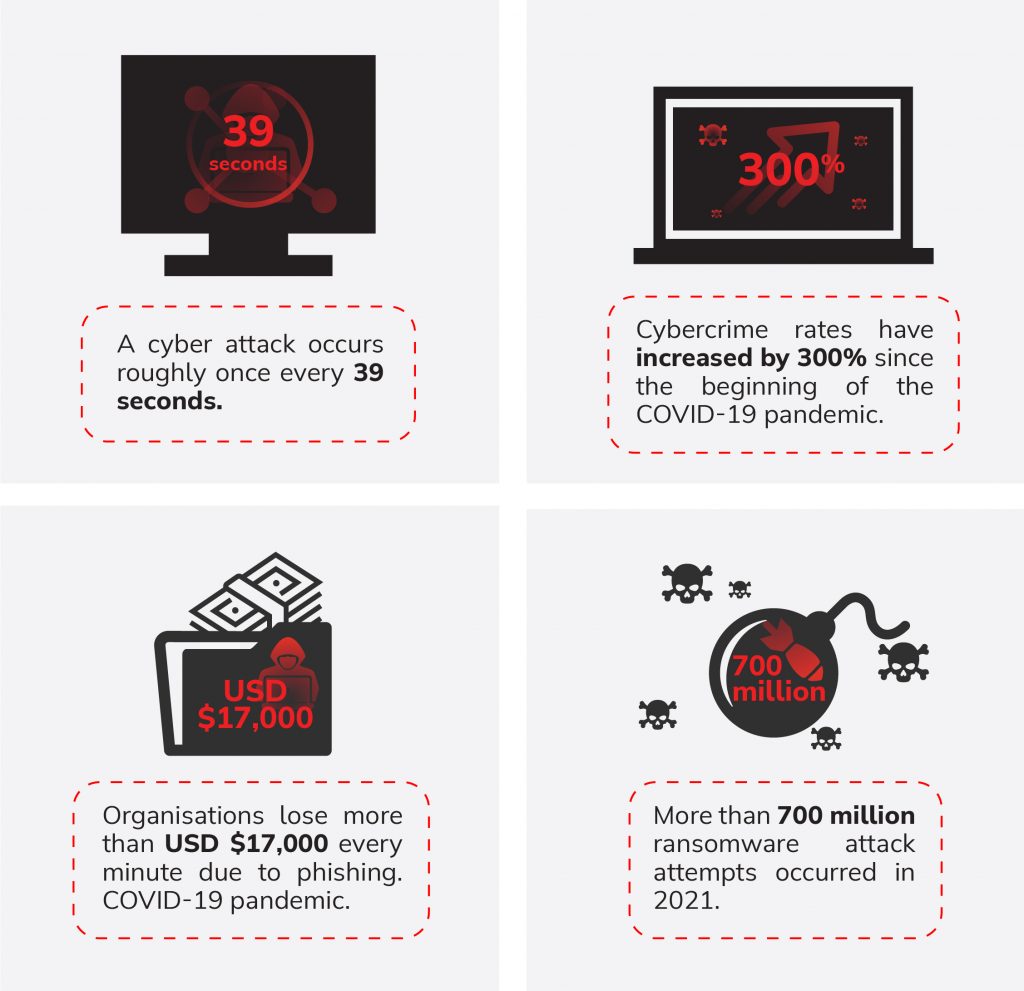
To be clear, IAM is no panacea that will completely protect organisations from potentially crippling attacks. But it can certainly help a big deal.
IAM Best Practices
The question now is: How can organisations best implement IAM? Here are a few suggestions:
Be Strategic and Look at Holistic Implementation
A common advice among the experts Cybersecurity Asia consulted for this feature is the need to be strategic and holistic in as far as implementing IAM across the organisation and its network. In this regard, companies need to look at things from a bigger-picture perspective and realise that IAM is not simply about granting and controlling access. Rather, it is as much about weaving together security, identity management and compliance to enable more stringent security and build cyber resiliency in general.

Ian Lim, Field Chief Security Officer, Asia Pacific & Japan, at Palo Alto Networks suggests pretty much the same strategic, big-picture approach. A good start, according to Lim, would be to enforce the principle of least privilege, which ensures only a minimum level of access, thereby reducing the attack surface.
Lim also recommends enforcing strong multi-factor authentication (MFA) to help prevent unauthorised access to systems and applications. Implementing MFA adds an extra layer of security by requiring users to provide more than one form of authentication. However, Lim warns of SMS-based MFA being easily exploitable, which is why organisations must instead opt for reputable authenticator app-based MFA. For sensitive data and critical systems, hardware-based security keys (like FIDO2) might be the best option.
Be Scientific and Have Clear Targets

Grant Orchard, Field CTO, Asia Pacific & Japan, at HashiCorp, recommends something akin to trial-and-error, but more scientific and targeted.
“The first principle is to focus on workflows, not technology. I would strongly recommend writing down the different workflows you are trying to solve for,” Orchard notes. “This is similar to Test Driven Development (TDD), a software development principle whereby you start with a set of tests for functions to pass and fail, and tweak your code until those tests complete successfully. Capturing the multitude of workflows and scenarios under which users should be able to access systems will form a strong starting point to develop the IAM policies.”
Orchard gives as an example the levels of access an organisation would normally grant its Site Reliability Engineering team for a given application. This time, in performing their task, will likely not need read/write access to said organisation’s production database systems. But suppose they are on call and an incident is logged, and they are connecting from a company device. In such case, a set of credentials with appropriate permissions could be generated to enable a dynamic connection to the target systems. Once the incident is resolved, however, both the credentials and the connections should be revoked.
Leveraging the Concept of Zero-Trust
Closely intertwined with IAM is the concept of zero-trust, where everyone and everything is considered as a potential threat. Hence, nothing and no one is supposed to be trusted—unless their identity is established and verified. The idea behind deploying zero-trust solutions in this regard is to authenticate each user or device not only when entering the network, but also as it moves within it or attempts to access files or documents.
Therefore, implementing zero-trust solutions within the IAM framework only strengthens the latter by enabling granular identity verification. When deployed in tandem, the IAM can grant predefined access to one specific user (an identity), while the zero-trust architecture will require that user to verify their identity before access is actually granted.
This added layer of identity vetting is critical because as much as 73% of data breaches are mismanaged or stolen credentials. But with zero-trust, an intruder who has acquired identity credentials will still have to go through a verification process to confirm the identity.
A Step-By-Step Approach
Crowstrike’s El-Nabawi is more specific in his recommendations, outlining the following implementation strategies:
- Establish the core set of objectives for the IAM solution.
- Audit existing and legacy systems to identify gaps within the existing architecture.
- Identify core stakeholders to help with identity mapping and defining user access rules.
- Capture all user groups and include as much granularity as necessary.
- Identify all user access scenarios and define corresponding rules, taking into account cloud assets and how access within the cloud environment differs from on-premises access.
- Consider any integration points with other security systems or protocols including the zero-trust solution or identity security system.
Validation, Education and Tech Integration
It should also be noted that IAM implementation is not a one-time thing. You do not just set it up and let it be. Instead, you need to keep improving it and adding to its capabilities.
To this end, Palo Alto’s Lim suggests continuous validation. One way to do this, Lim explains, is to continually baseline normal user activities and investigate abnormal user activities. Another is to regularly review and update access rights. Doing so ensures that employees only have access to the resources they need to perform their job functions. It also helps identify and remove any dormant or unused accounts to reduce the attack surface.
Education is also a vital part of good IAM, says Lim. Among other things, organisations must educate their staff on creating strong passwords, avoiding phishing scams and reporting suspicious insider activity. Employees can also be trained to recognise and respond to potential security threats, thus offering the enterprise another layer of security.
The business landscape is changing. And to keep abreast with these changing dynamics, enterprises must provide their workforce with easy access to work applications and systems regardless of location but without compromising security. IAM can help in this regard, but its successful implementation, according to ForgeRock’s Hope, will ultimately depend also on the use of the right platforms. Ideally, this platform should offer real-time user access orchestration and integration into everything—from legacy to modern applications.




