Securing Software-Defined Vehicles
By: Hwee Yng Yeo, Smart Mobility Advocate, Keysight Technologies
Old car models with mechanical components are rapidly giving way to the increasingly software-defined vehicle (SDV) with features that not only allow drivers and passengers to stay connected to the digital world but to enjoy a safer and easier journey with automated driving features (see Figure 1).
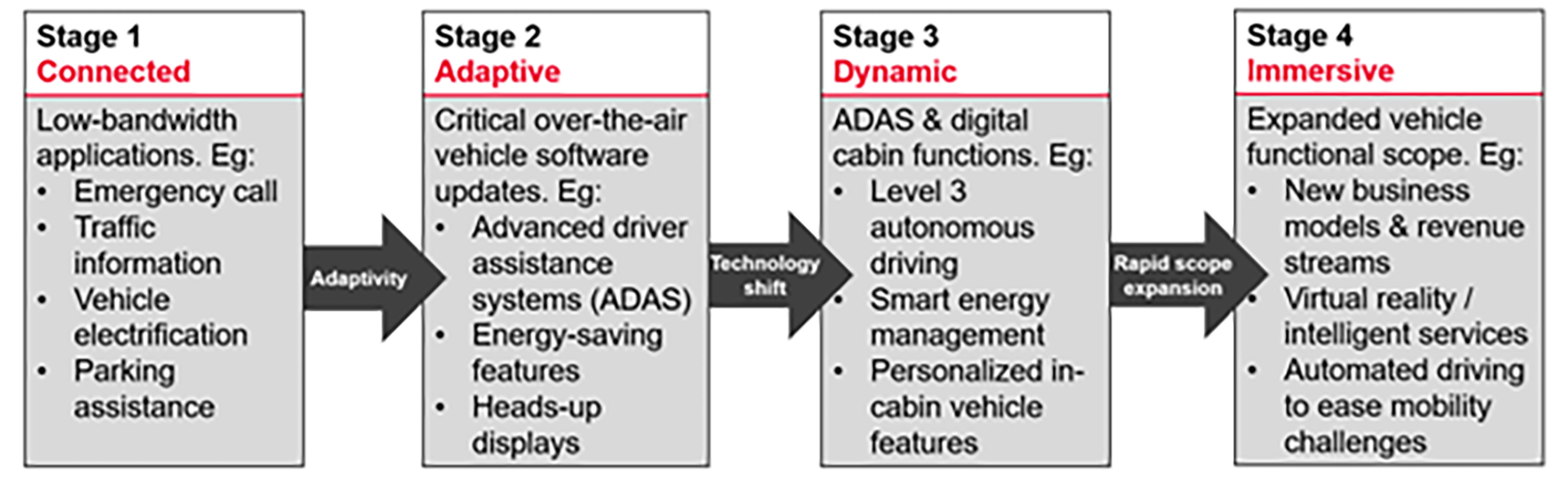 Figure 1: Four key stages of development for software-defined vehicles (Source: World Economic Forum)
Figure 1: Four key stages of development for software-defined vehicles (Source: World Economic Forum)
With increasing connectivity comes greater exposure to cybersecurity risks, as attested by the Internet of Things (IoT). It wasn’t so long ago when the conveniences of mobile connectivity seemed like a real boon – from banking and buying bespoke brands just a click away. That was until cybercrimes became a bane and a scourge, estimated to cost the global economy more than US$20 trillion by 2026, a 1.5 times increase compared to 2022 data (source: Statista).
These staggering dollar costs are hard lessons learned, and the automotive industry is stepping up on preemptive efforts to secure the next big data mine on wheels – the software-defined vehicle.
However, securing software-defined vehicles is extremely challenging, as increased connectivity means an increased number of potential attack interfaces (see Figure 2). Not only are cyber-hacking tools more advanced, but attackers are also moving beyond direct attacks against individual vehicles – targeting fleets, mobility applications, and services.
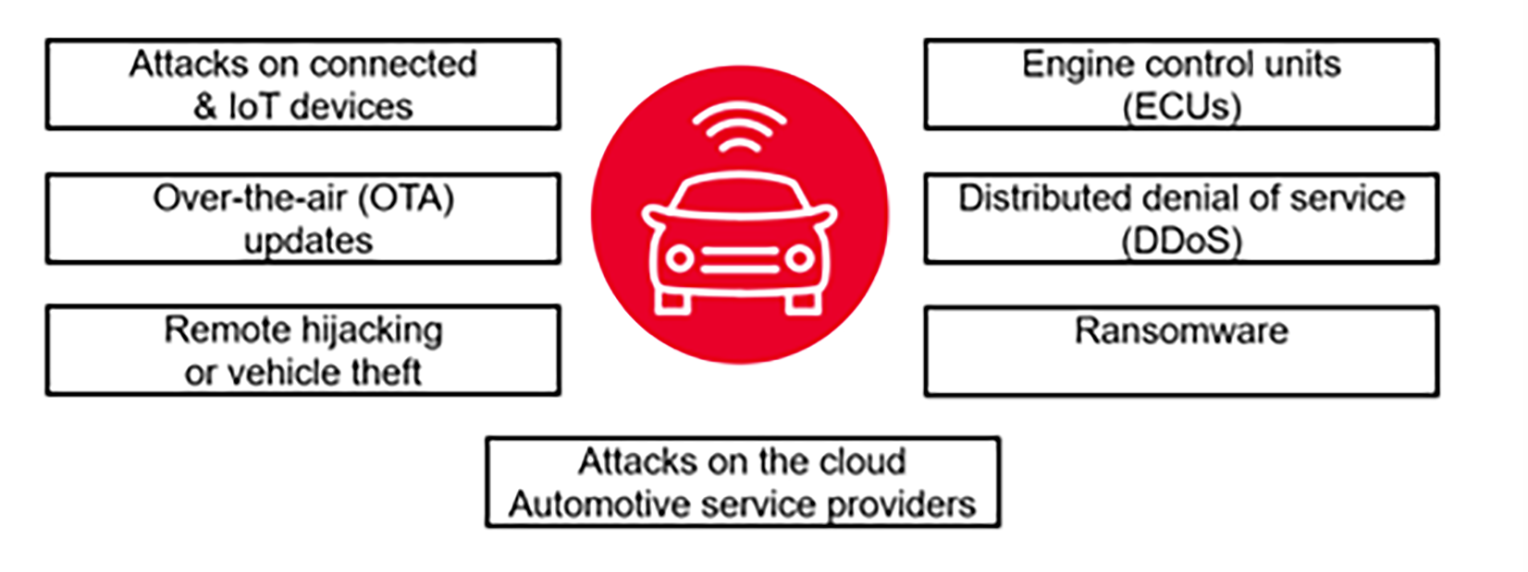 Figure 2: Greater connectivity interfaces increase the vulnerability of software-defined vehicles to cyberattacks.
Figure 2: Greater connectivity interfaces increase the vulnerability of software-defined vehicles to cyberattacks.
Evolving Regulations and Standards
In the recent past, there were no global automotive cybersecurity standards, with only best practices from key automakers and their Tier 1 supply chain developing their own unique cybersecurity testing requirements.
The good news is that in 2020, the United Nations’ World Forum for Harmonisation of Vehicle Regulations, known as WP.29 for short, introduced an automotive cybersecurity regulatory framework for automakers.
For example, UN Regulation 155 (UN R155) mandates rigorous cybersecurity management system audits for automakers and their suppliers. It also requires automakers to obtain “vehicle type approval”, which involves auditors conducting tests on vehicle products sharing the same electrical architecture. On 1st September 2021, the Society of Automotive Engineers (SAE) and the International Organisation for Standardisation (ISO) jointly published the ISO/SAE 21434 standard. Table 1 explains what these regulations and standards cover:
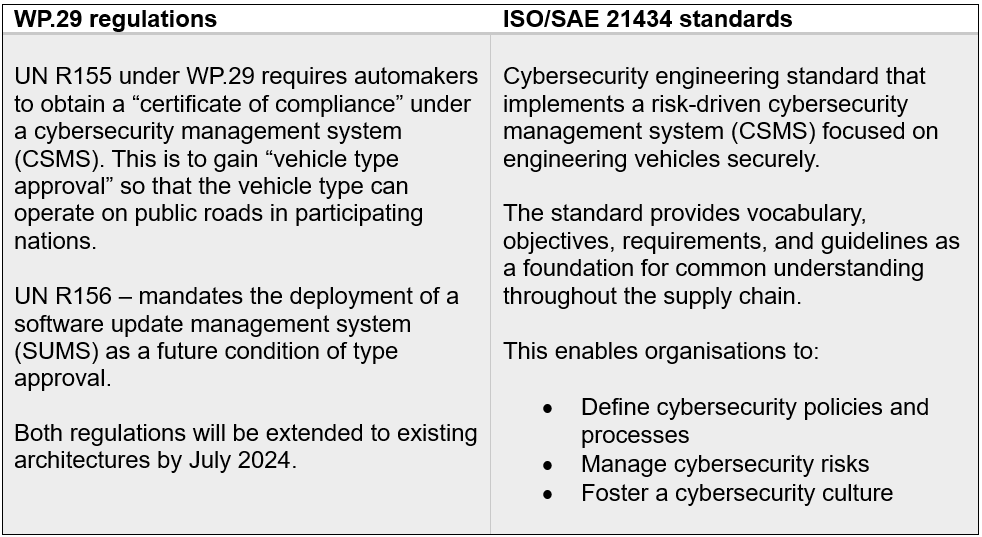 Table 1: An overview of UN R155 and R156 vs ISO/SAE 21434
Table 1: An overview of UN R155 and R156 vs ISO/SAE 21434
Automakers and their key suppliers must comply with UN R155 regulations while the ISO/SAE 21434 standard is a set of guidelines. Both must go hand-in-hand if automakers want to bring new vehicle models to market.
Exactly how then can automakers and their Tier 1 suppliers translate both regulation and standard into action to secure the software-defined vehicle? The automotive industry has the benefit of leveraging learnings from cybersecurity experts who have been trying to stay ahead of hackers for decades since the Internet of Things.
For example, non-profit cybersecurity advocates Open Web Application Security Project has an OWASP Top 10 list of vulnerabilities that automakers reference, to secure the various attack interfaces of the software-defined vehicle.
Table 2 shows the OWASP Top10 list, and the tests that automakers can implement for boosting automotive cybersecurity:
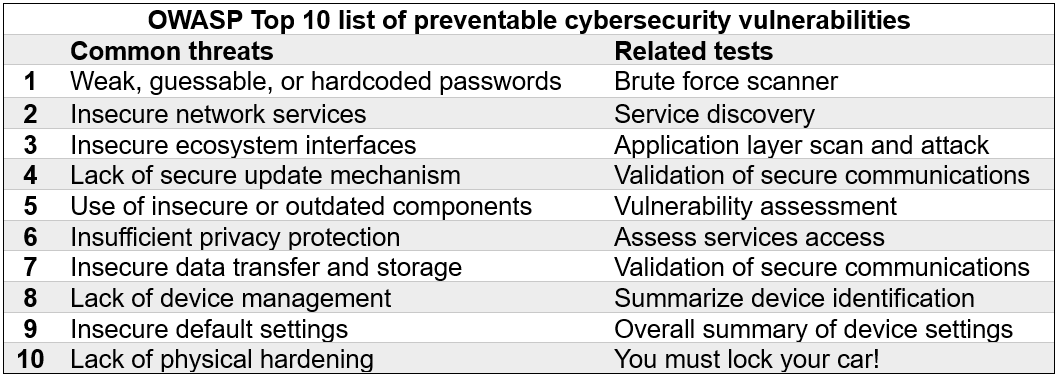 Table 2: Leveraging the OWASP Top 10 as a checklist to implement automotive cybersecurity testing.
Table 2: Leveraging the OWASP Top 10 as a checklist to implement automotive cybersecurity testing.
Putting Security to the Test
Testing is an essential part of the UN R155 automotive cybersecurity management system (CSMS). Different systems must be thoroughly tested, from onboard hardware like physical in-vehicle networks, electronic control units, and charging ports for electric vehicles, through all layers of the open systems interconnection (OSI) stack. Multiply that with different threat scenarios and design iterations, the list of tests is extensive.
To manage the exhaustive lists of tests and be able to manage and pass audit trails, automakers, and their suppliers are turning to turnkey automotive cybersecurity test solutions. These solutions comprise electronic systems and software to emulate a victim vehicle and hacker(s). They typically comprise these key elements (see Figure 3):
- Wireless and wireline signal emulators and analysers to simulate and monitor the vehicle’s communication systems
- Reconnaissance and exploitative attack servers
- Application and threat intelligence library from which different attacks can be selected and scheduled
- Automation and tracking platform to manage test data and results for reporting and auditing
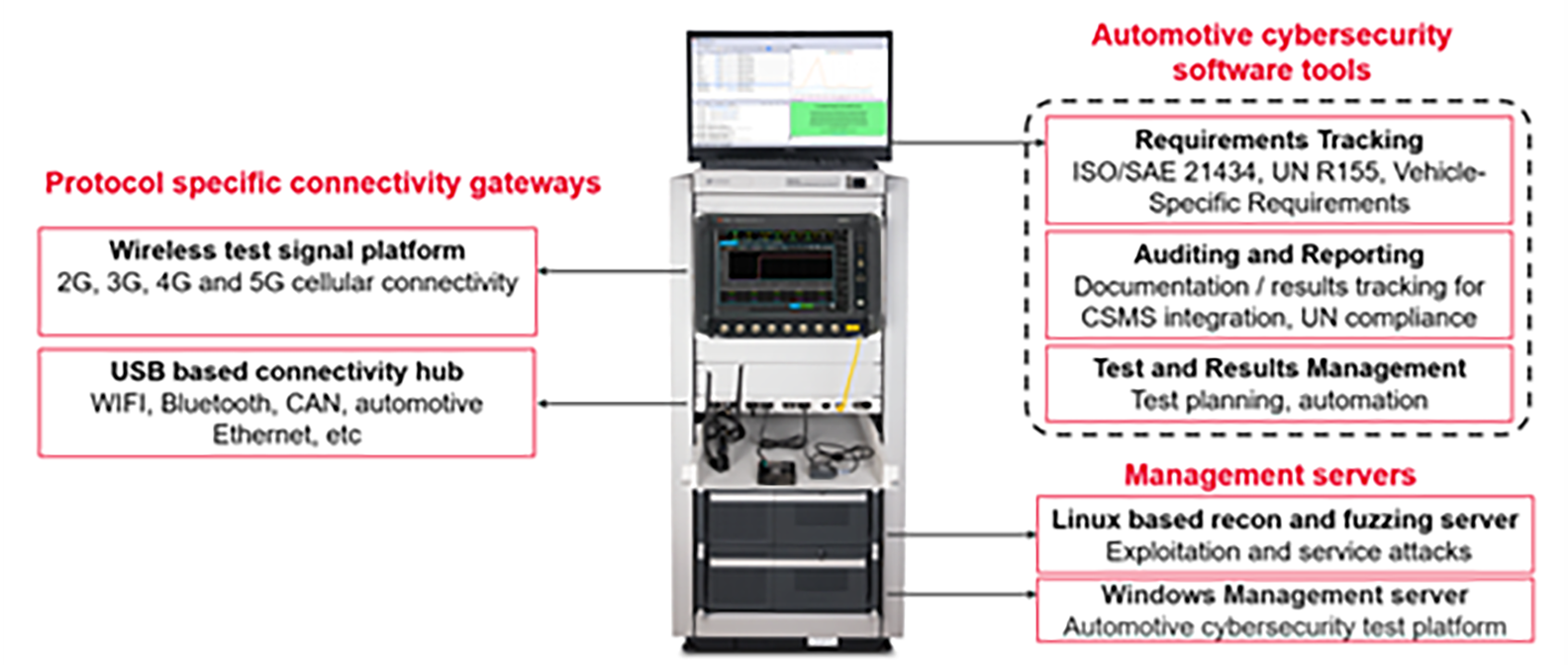 Figure 3: Example of an automotive cybersecurity test setup. (Image source: Keysight Technologies)
Figure 3: Example of an automotive cybersecurity test setup. (Image source: Keysight Technologies)
Early Detection Saves Money – and Reputation
Taking a page from the history of the Internet of Things, and in more recent times, the smartphone, where millions of dollars are lost daily to scammers and hackers, securing the connected smart vehicle of the future is both important and urgent.
IoT and the smartphone changed the way we live. There is no going back to an off-grid world for most of us, despite the dangers of cyber exploitations. And software-defined vehicles will likely expand upon the connected way of living for us.
Hopefully, with lessons learned on how to secure our connected world, automakers and their key suppliers can stay many steps ahead of cybercriminals waiting to exploit both individual car owners and organisations that run fleets and associated transportation systems, and electric vehicle supply equipment. Rigorous testing throughout the vehicle’s life cycle will help minimise the risks of automotive cyberattacks and help keep automakers and service providers off the headlines of who’s been hacked.




