Breaking the Cycle: Preventing Re-Victimisation in Cyber Extortion Attacks

Cyber extortion has evolved into multi-layered threats that go beyond locking systems and demanding ransom, combining data encryption with tactics like stealing sensitive information, threatening exposure, and even targeting customers of victimised organisations. According to the Cy-Xplorer 2024 report by Orange Cyberdefense, re-victimisation increased by 77% in just 12 months, involving 60 different threat actors and affecting 4,374 victims.
This article examines the complex nature of ransomware, the expanding attack surface in modern IT environments, and strategies businesses can adopt to prevent repeat attacks.
The Complex Phenomenon of Re-Victimisation in Cyber Extortion
Re-victimisation in cyber extortion is a growing concern that amplifies the impact of ransomware attacks. It refers to the cycle where victims of an initial breach are repeatedly targeted. As outlined in the Cy-Xplorer 2024 report, this phenomenon involves organisations being listed multiple times on Dedicated Leak Sites (DLS), either by the same or different threat actors. These repostings can occur within days, months, or even years of the initial attack, presenting a persistent threat to the organisation.
How Re-Victimisation Happens
Re-victimisation can manifest in three primary ways:
- Repeated Attacks: Threat actors launch a second, unrelated attack on the same victim, often exploiting the same vulnerabilities or new entry points.
- Re-Use of Data: Stolen data circulates within the cybercriminal ecosystem, allowing other attackers to leverage it for subsequent extortion attempts.
- Affiliate Crossover: Affiliates operating under multiple ransomware groups utilise previously compromised data to amplify pressure on the victim.
These scenarios highlight the fluidity of the cybercrime ecosystem. Affiliates, who often customise tools provided by Ransomware-as-a-Service (RaaS) operators, play a pivotal role in these repeat incidents. Unlike core operators, affiliates can move between different ransomware brands, making them unpredictable variables in the ecosystem.
Sectors Affected by the Multi-Layered Extortion
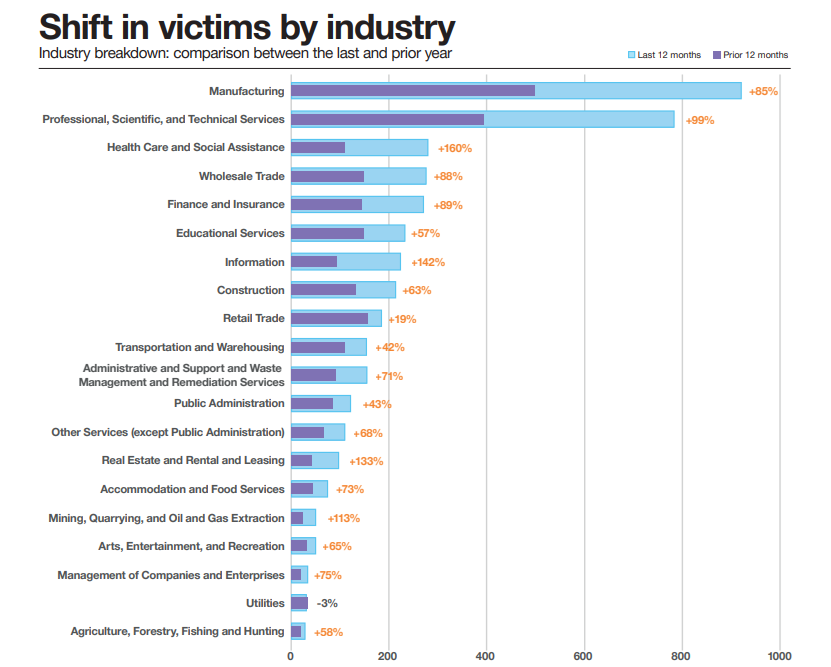
Ransomware groups increasingly target industries reliant on sensitive data and critical operations, with the Cy-Xplorer report highlighting sharp increases in incidents over the past year. Manufacturing leads with an 85% rise, followed by Professional, Scientific, and Technical Services (+99%) and Health Care and Social Assistance (+160%). Other sectors like Finance and Insurance (+89%), Information (+142%), and Wholesale Trade (+88%) also saw notable spikes, as ransomware operators exploited their vast stores of personal and financial data using “double extortion” tactics.
Timeframes of Re-Victimisation
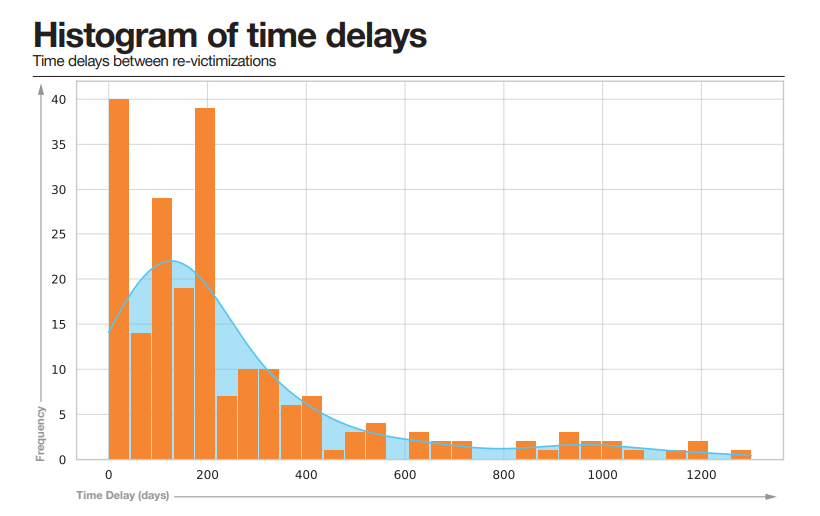
An analysis of 207 re-victimisation occurrences from the Cy-Xplorer dataset reveals that the median time between incidents is 177 days, or roughly six months. However, the delays can range from as short as a single day to as long as 1,301 days (about 3.5 years). This variability underscores the unpredictability of re-victimisation, with some victims facing immediate re-listing while others are targeted years later.
Preventing Re-Victimisation: A Holistic Approach
Preventing re-victimisation requires a comprehensive strategy that addresses both immediate threats and long-term vulnerabilities. Here are some key steps organisations can take to ensure they don’t fall victim to repeated attacks.
- Securing the Attack Surface
Modern IT environments, with cloud, IoT, and remote work, create vulnerabilities, making the attack surface—the sum of potential entry points of unauthorised access—a critical cybersecurity focus. Where traditional tools falter because they are limited to predefined perimeters and known assets, External Attack Surface Management (EASM) is able to map the full extent of an organisation’s attack surface. This includes shadow IT, cloud misconfigurations and unmanaged digital assets that attackers exploit. The real difference EASM makes is it continuously monitors and remediates these vulnerabilities in real-time. So it not only pre-empts potential breaches but also complements zero trust and endpoint detection systems to create a multi-layered defence that significantly reduces exposure to threats such as supply chain compromise. - Improving Cyber Hygiene
Human error remains a top threat. Regular employee training on social engineering, multi-factor authentication (MFA), timely software updates, and strong password policies are essential to mitigate ransomware risks. - Incident Response Plans
While detecting threats is important, the real test lies in how an organisation responds when an incident occurs. Effective strategies include isolating infected systems, conducting forensic investigations to address vulnerabilities, and simulating attacks to improve readiness. - Crisis Management
Ransomware often exploits reputational risks. Crisis plans should ensure transparent communication, monitor dark web activity, and provide legal counsel for navigating regulatory challenges. - Threat Intelligence and Collaboration
Threat intelligence platforms are becoming increasingly important as they provide real-time data on vulnerabilities, attack vectors and adversary tactics to help organisations stay ahead of emerging cyber threats and adapt their defences accordingly. Organisations can also do their part by sharing anonymised threat data with industry peers to strengthen collective security without compromising proprietary information.
Future-Proofing Against Re-Victimisation
The threat of ransomware is unlikely to diminish. Its evolution into a multi-layered extortion model demands that businesses adopt equally sophisticated defences. Solutions like Orange EASM can help secure the growing attack surface, while robust incident response plans, employee training, and collaborative efforts ensure long-term resilience.
Breaking the cycle of re-victimisation is possible, but it requires commitment at all levels of an organisation. By staying vigilant and embracing proactive measures, businesses can protect their data, customers, and reputation in an increasingly perilous digital landscape.
If you want to find out how you can protect your organisation from re-victimisation and strengthen your defences against evolving cyber threats with EASM tools, click to learn more.




